Secure Remote IoT: P2P SSH Guide + Free Download
Can you truly secure your Internet of Things (IoT) devices and harness their full potential from anywhere in the world? The answer is a resounding yes, and the key lies in understanding and implementing secure remote access solutions like remoteiot p2p. This article will serve as your comprehensive guide, unraveling the intricacies of securely connecting your devices, specifically your Raspberry Pi, to a remote peer-to-peer (p2p) environment. We will explore the practical steps, the underlying technical principles, and the critical benefits of utilizing remoteiot, empowering you to take control of your IoT ecosystem with confidence.
The modern landscape of connected devices is rapidly expanding, encompassing everything from smart home appliances to industrial sensors. This interconnectedness brings unprecedented opportunities, but it also introduces significant security challenges. Without proper precautions, your devices can become vulnerable to cyberattacks, data breaches, and unauthorized access. Remote access is often a necessity, allowing you to monitor, control, and manage your devices from afar. However, this access must be secured to protect your data and your network. Remoteiot p2p offers a robust and secure solution, enabling you to connect to your devices remotely without exposing them to the public internet. This approach ensures privacy and reduces the risk of vulnerabilities.
Before diving into the technical aspects, let's highlight some of the core advantages of remoteiot, particularly in the context of your Raspberry Pi:
- Ruth Madoff Today What Happened After Bernies Scheme
- Sha Gz Height How Tall Is The Bronx Drill Star Really
- Secure Remote Access: Establish secure, encrypted connections, safeguarding your data from eavesdropping and unauthorized access.
- Direct P2P Connections: Utilize a virtual private cloud (VPC) network that provides direct peer-to-peer connections for minimal latency and maximum bandwidth, ensuring smooth and responsive remote access.
- Free Downloadable Tools: Gain access to essential software and tools that simplify the setup and configuration process, allowing you to get started quickly and efficiently.
- Enhanced Remote Surveillance: Leverage features such as remote photo capture, video recording, and remote video playback to monitor your environment securely.
- Cost-Effectiveness: Benefit from a free download option, reducing initial costs and making remote access accessible to a wider audience.
To fully grasp the power of remoteiot p2p, you need to understand the principles behind it. The p2p architecture eliminates the need for a central server, instead establishing direct connections between your devices. This architecture provides several benefits, including enhanced security, reduced latency, and increased resilience. The virtual private cloud (VPC) network used by remoteiot further enhances security by creating a private, isolated network for your devices. Data communication occurs directly between the devices within this VPC, minimizing the attack surface and maximizing privacy.
Let's translate these advantages into concrete actions. One of the core steps involves installing the remoteiot service on any IoT device equipped with a TCP/IP stack. This process typically involves downloading and installing the necessary software, configuring the device's network settings, and setting up security protocols. The specific steps may vary depending on your device's operating system and configuration, but the underlying principles remain consistent: prioritize security and ensure a reliable connection.
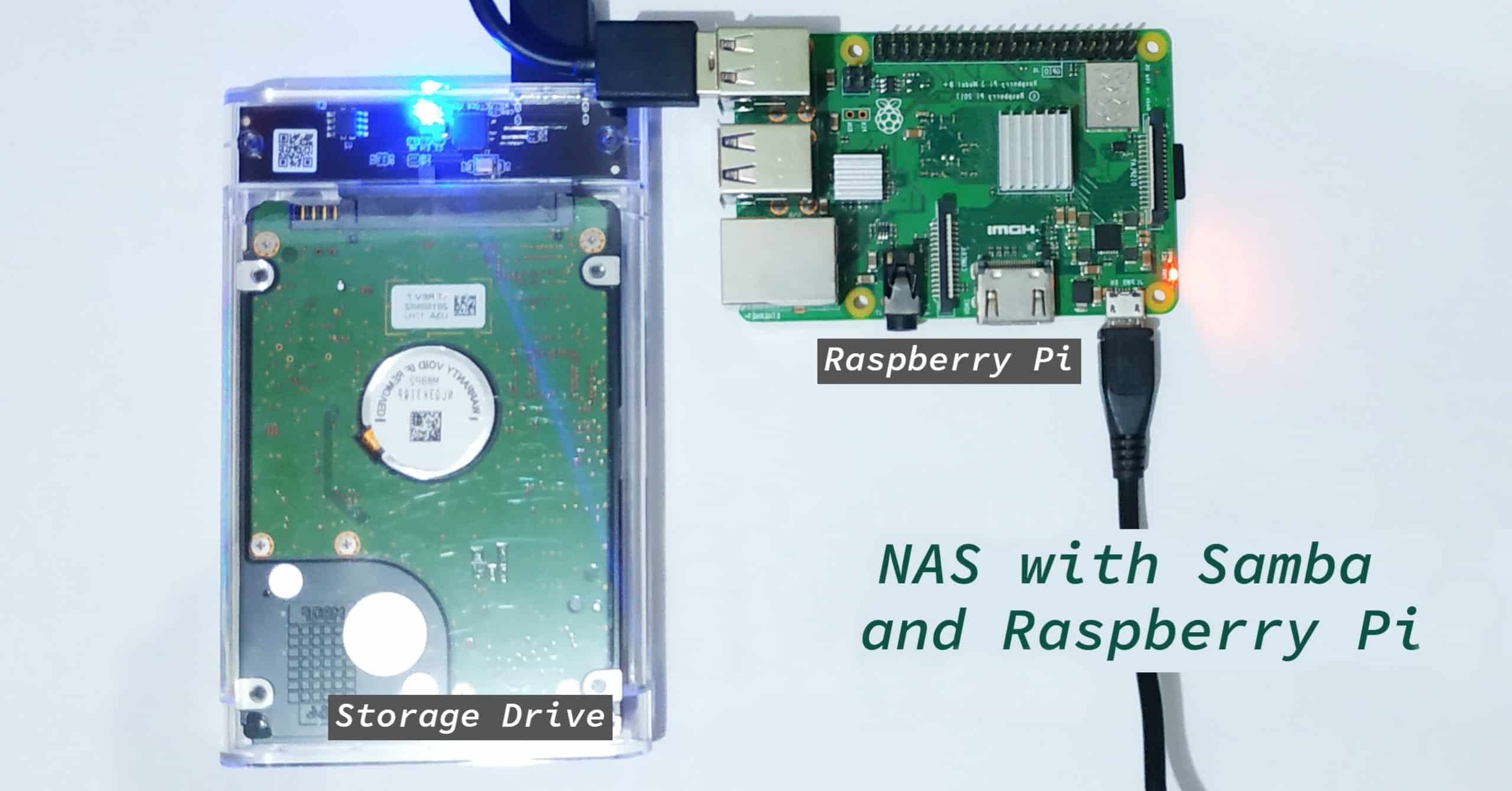
The Raspberry Pi, with its versatility and affordability, is an ideal platform for experimenting with remoteiot. Installing the service on a Raspberry Pi typically involves downloading the appropriate software package, configuring the network settings, and generating SSH keys. This establishes a secure connection, allowing you to access the Raspberry Pi's command line interface, transfer files, and control its functionality from a remote location.
- Michel Stern Inside Lisa Kudrows Husbands Life Love Story
- Carol Burnett Still Alive Emmy Nomination Life Update
To demonstrate the real-world application of remoteiot, consider a scenario where you want to monitor your home from a remote location. By installing the remoteiot service on a Raspberry Pi connected to a camera, you can capture photos, record videos, and even access real-time video playback. This provides a comprehensive security solution, allowing you to monitor your home's security, check on pets, or simply keep an eye on things while you're away. The utility offered by this solution extends beyond basic surveillance.
The use of SSH (Secure Shell) plays a critical role in ensuring a secure connection. SSH provides an encrypted channel for communication, protecting your data from eavesdropping and unauthorized access. When connecting to your Raspberry Pi via SSH, you typically use a username and password for authentication. However, for enhanced security, it is highly recommended to use SSH keys. SSH keys are cryptographic keys that are used to authenticate a user without requiring a password. This enhances security by making it significantly more difficult for attackers to gain unauthorized access to your device. Using SSH keys is a critical step in securely connecting your remote IoT devices. You can generate SSH keys on your local machine, copy the public key to your Raspberry Pi, and then disable password-based authentication. This approach reduces the risk of brute-force attacks and ensures that only authorized users can access your device.
The process of downloading and configuring the remoteiot p2p solution is crucial. While we will provide a general overview of the process, it is important to consult the specific documentation provided by the remoteiot service provider. The free download option typically includes the necessary software, configuration files, and documentation. Following the instructions carefully will ensure that you install and configure the service correctly. Make sure to follow all security best practices during the installation process, and make sure that you understand and configure firewall settings. Proper configuration is key, and it's vital that all devices are authenticated. Authentication confirms that the device is who it claims to be.
When using remoteiot, consider the potential risks. Even with encryption and secure protocols, there is always a risk of vulnerabilities. To mitigate these risks, ensure that you:
- Keep your software and firmware up to date with the latest security patches.
- Use strong passwords and change them regularly.
- Use SSH keys.
- Only open necessary ports on your firewall.
- Regularly monitor your network for suspicious activity.
- Consider enabling two-factor authentication, if available.
The ability to remotely access your Raspberry Pi unlocks countless benefits, and also provides an easy way to remotely connect to other IoT devices you may have. The remoteiot p2p solution, is capable of creating direct connections. This translates to the fastest possible data communication between devices, with the lowest latency and the highest bandwidth. You can use this setup for almost anything, for example to control your smart home devices from anywhere, to manage industrial sensors, or even to remotely monitor the performance of your computer. The possibilities are almost limitless.
One of the most compelling features of remoteiot is its suitability for remote surveillance. This is a crucial element in numerous IoT applications. You can utilize the features like remote photo capture, video recording, and remote video playback, which allows you to monitor your devices. The combination of these features, when used correctly, will give you the power to enhance the security of your home, your office, or any other place you are trying to keep an eye on.
Here are the steps to securely connect remote IoT devices:
- Install the Remoteiot service: on each IoT device with a TCP/IP stack.
- Download and install the free software: Follow the provider's installation instructions and ensure you obtain the software from a trustworthy source to avoid introducing vulnerabilities.
- Configure Network Settings: Properly configure the network settings for each device. This may include assigning static IP addresses, configuring port forwarding, and setting up firewall rules.
- Generate SSH Keys: Generate SSH keys on your local machine and copy the public key to your IoT devices. This significantly enhances security by eliminating the need for password-based authentication.
- Configure SSH: Configure the SSH daemon on your IoT devices. Ensure SSH is running and listening on a secure port. Consider disabling password authentication and enabling key-based authentication only.
- Test the Connection: Once everything is set up, test the connection to your IoT devices using SSH. Ensure you can successfully connect remotely and that all security measures are in place.
- Ensure All Devices are Properly Configured and Authenticated: double-check all configurations and authentication settings. Proper authentication is critical to protecting your network.
This guide is designed to walk you through a complex but essential process. Remember that by following best practices, you're not just implementing a technology; you are building a foundation of security and control for all of your connected devices. The journey from a basic setup to a secure, remotely accessible IoT ecosystem is achievable. By understanding the principles and following the steps outlined in this guide, you can harness the full potential of your Raspberry Pi and other IoT devices, ensuring their security and maximizing their utility.
The technical aspects of remoteiot, while essential for understanding its functionality, can be complex. We encourage you to delve deeper, exploring the technical specifications and understanding how p2p connections are established, how data is encrypted, and how the VPC network functions. Researching these aspects will provide you with a deeper understanding and enable you to make informed decisions when implementing remoteiot solutions. Explore the benefits and drawbacks, considering both advantages and disadvantages. This thorough approach will allow you to build a solution that is right for your needs.
With this foundational knowledge in place, you are now prepared to explore the world of remote access and the possibilities it unlocks. You have the ability to securely connect remote IoT devices, and the understanding necessary to implement a reliable and robust solution. The future of the internet of things is here, and with tools like remoteiot, you are ready to take control.


Detail Author:
- Name : Mr. Bell Sipes
- Username : cecile66
- Email : petra.wuckert@yahoo.com
- Birthdate : 1986-05-26
- Address : 4832 Jarrett Locks Swaniawskiburgh, WI 22437
- Phone : +13469800948
- Company : Keebler, Waelchi and Schmidt
- Job : Welder and Cutter
- Bio : Illum odio architecto deleniti voluptatum sint consectetur. Sit quo debitis eveniet aut quia ut laboriosam. Ab quia et consequatur vero optio veniam quia porro.
Socials
facebook:
- url : https://facebook.com/maudo'kon
- username : maudo'kon
- bio : Iure id non debitis enim. Eum corrupti sunt amet debitis ut.
- followers : 1769
- following : 1556
twitter:
- url : https://twitter.com/maud_dev
- username : maud_dev
- bio : Magnam quo cumque et. Aut dolorem provident expedita dolores autem placeat. Rerum quam sunt libero.
- followers : 3667
- following : 2494
linkedin:
- url : https://linkedin.com/in/o'konm
- username : o'konm
- bio : Vel necessitatibus sed amet doloremque in at.
- followers : 2611
- following : 2222
tiktok:
- url : https://tiktok.com/@maud.o'kon
- username : maud.o'kon
- bio : Fuga et et atque voluptatibus.
- followers : 3396
- following : 2161