SSH Remote IoT On Mac: Setup & Secure Access Guide
Are you ready to unlock the full potential of your IoT devices, from anywhere in the world? The answer lies in mastering SSH remote IoT on macOS a powerful combination that empowers you to securely access, manage, and troubleshoot your devices with unparalleled ease.
In today's interconnected landscape, the proliferation of Internet of Things (IoT) devices has revolutionized how we interact with technology. From smart home appliances to industrial sensors, IoT devices are collecting and transmitting data, enabling us to monitor, control, and automate various aspects of our lives. However, with this growing adoption comes a critical need: secure remote access.
Whether you're a seasoned IT professional, a budding hobbyist, or simply curious about the possibilities, this guide is designed to be your comprehensive resource. We'll delve into the essentials of SSH (Secure Shell), explore its seamless integration with remote IoT, and equip you with the practical steps needed to set up and configure it on your Mac. Moreover, we will address troubleshooting and best practices ensuring a secure and efficient experience. This will empower you to take full advantage of the convenience and power of remote device management.
- Understanding Suicide Methods Important Information You Need To Know
- Alana Cho Leaks Porn Where To Find The Hottest Content 2024
This article will cover the essentials of SSH, how it integrates with remote IoT, and the steps you need to take to set it up on your Mac. We'll also discuss best practices to ensure your connection remains secure and efficient. Let's make sure you're ready for whatever IoT challenge comes your way! Understanding how to use SSH remote IoT on Mac for free can significantly enhance your ability to manage devices remotely.
This guide aims to simplify the process while providing actionable insights for beginners and advanced users alike. Now that you know how to use SSH for IoT on your mac, here are some best practices to keep in mind: Always use strong, unique passwords for your IoT devices. Avoid using common words or easily guessable information. By following the steps in this guide, you can securely connect to and control your IoT devices from anywhere in the world. To connect to a remote system using SSH, well use the SSH command.
Before diving into the technical aspects, let's clarify what SSH actually is. SSH is a cryptographic network protocol that provides a secure channel over an unsecured network. It is particularly valuable for remote device management because it encrypts all communication between your computer (the client) and your IoT device (the server). This encryption protects your data from eavesdropping and unauthorized access, making SSH an indispensable tool for secure remote access.
- Unveiling Jennifer Landon From Yellowstones Teeter To Michael Landons Legacy
- Explore Mia Khalifas Tiktok Viral Videos Sound
The fundamental principles of SSH involve establishing a secure, encrypted connection between two devices over a network. This process typically involves the following steps:
- Authentication: The client verifies the identity of the server, typically by validating the server's public key. This ensures that you are connecting to the intended device and not a malicious imposter.
- Key Exchange: The client and server negotiate a shared secret key, which is then used to encrypt all subsequent communication.
- Encryption: All data transmitted between the client and server is encrypted using the shared secret key, ensuring confidentiality and integrity.
Once the connection is established, you can use SSH to securely execute commands, transfer files, and tunnel other network traffic. This makes SSH a versatile tool for managing your IoT devices remotely, allowing you to diagnose problems, update software, and configure settings without being physically present.
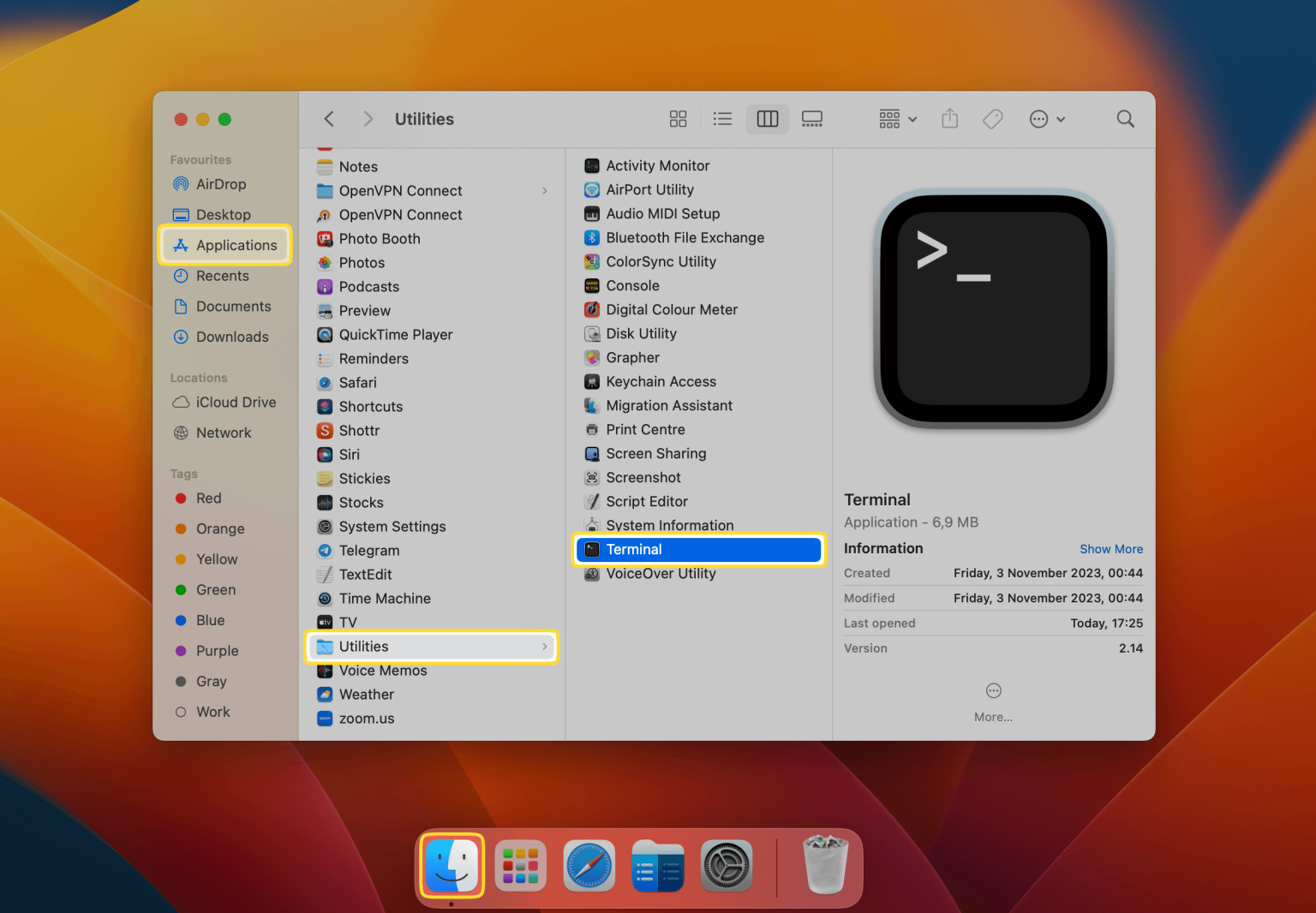
Now, let's explore the practical steps of setting up SSH on your Mac for remote IoT access. The process can be broken down into the following key phases:
If you are using Windows, youll need to install a version of OpenSSH in order to be able to SSH from a terminal. If you prefer to work in Powershell, you can follow Microsofts documentation to add OpenSSH to Powershell. This will open a file called ssh_config. Scroll down to the host section and add lines mentioned in ssh configuration if you haven't already. Save the file and close it. Connect to the remote server. Now that your SSH key is configured, you can connect to HPG using VS Code. To do this, follow these steps:
- Enabling Remote Login: On your Mac, the first step is to enable the SSH server. This involves activating the "Remote Login" feature in the Sharing preferences. By enabling this, you grant permission for other devices to connect to your Mac via SSH.
- Firewall Configuration: MacOS has a built-in firewall. You may need to configure the firewall to allow incoming SSH connections on port 22 (the default port).
- User Account Setup: Ensure you have a user account on your Mac with a strong password. This account will be used to log in to your Mac remotely.
Now, with the foundation laid, it's time to explore how to connect to your Mac via SSH from another device.
To connect to a remote system using SSH, well use the SSH command. Ssh is frequently used to tunnel insecure traffic over the internet in a secure way.
Whether you're a hobbyist or a professional, understanding how to use SSH remote IoT on mac for free can significantly enhance your ability to manage devices remotely. This guide aims to simplify the process while providing actionable insights for beginners and advanced users alike.
Here's a breakdown of how to establish a secure connection:
- Open Terminal: On the device you are connecting from, open a terminal or command prompt window.
- Use the SSH Command: Type the following command, replacing `username` with your Mac username and `hostname` with your Mac's IP address or hostname:
- Authentication: You will be prompted for your Mac user account password.
- Successful Connection: Upon successful authentication, you will be logged into your Mac's terminal, allowing you to execute commands and manage your system.
Once connected, you can interact with your Mac as if you were sitting in front of it. This is where the real power of SSH comes into play. You can execute commands, such as:
- Managing Files: Use commands like `ls` (list files), `cd` (change directory), and `cp` (copy) to navigate and manage your files on your Mac.
- Running Applications: Launch programs or scripts on your Mac remotely.
- Monitoring System Performance: Utilize commands like `top` or `htop` to monitor CPU usage, memory consumption, and other system resources.
Now, let's shift our focus to practical applications, showcasing how SSH can be integrated with your IoT devices. Imagine scenarios where you can remotely control and monitor your smart home devices or manage a network of sensors deployed in a remote location.
The first crucial step is to establish an SSH connection to your IoT devices. This typically involves the following:
- Enable SSH on the Device: Most IoT devices run on embedded Linux systems. Enable SSH on the device, often through its configuration settings.
- Configure Network Settings: Ensure your IoT device has a static IP address or a DHCP reservation to maintain a consistent connection.
- Use the SSH command: Type the following command, replacing `username` with your device username and `hostname` with your device's IP address or hostname:
After establishing the SSH connection, the real magic begins. You can now send commands and transfer data to your IoT devices securely. This opens the door to a wide range of possibilities:
- Remote Control: Execute commands to control your devices. For instance, you could turn on/off a light, adjust the thermostat, or trigger a sensor remotely.
- Data Collection: Retrieve data from your sensors and store it for analysis or display. You can collect temperature readings, environmental data, or any other sensor information.
- Firmware Updates: Safely update firmware on your devices to ensure the latest features, security patches, and bug fixes.
- Troubleshooting: Remotely diagnose problems. Access logs, restart services, and resolve issues without physically accessing your devices.
SSH is not just about establishing a secure connection; it offers an array of advanced functionalities, including:
- Port Forwarding: Tunnel other network traffic through the SSH connection.
- Key-Based Authentication: Enhance security by using SSH keys instead of passwords for authentication.
- X11 Forwarding: Display graphical applications running on your remote Mac on your local machine.
If you want to toggle SSH off and on and avoid the command line, you can do so by enabling remote login in the sharing preference panel on a Mac, or stop the server by leaving it unchecked. If you do not regularly use SSH, there is no reason to enable the SSH server on a Mac.
Turning on remote login to access your mac from another computer using ssh (secure shell protocol) or sftp (ssh file transfer protocol). Set up remote login on your mac on your mac, choose apple menu > system settings, click general in the sidebar, then click sharing. How to access a mac via ssh. After enabling ssh, you can connect to that mac via ssh. Open terminal or other ssh software. To initiate contact, you will need to use this format: Ssh username@hostname or sftp username@hostname. In a virtual network computing (vnc) environment, it is possible to encrypt connections using ssh port forwarding (tunneling) via the ssh command or through putty. To tunnel vnc connections over ssh, run the following command in the terminal or command line: How to turn off the ssh server on a mac.
When it comes to securing your SSH connections, the following best practices are essential:
- Use Strong Passwords: Choose strong, unique passwords for your Mac user account and IoT device accounts. Avoid easily guessable words or personal information.
- Implement Key-Based Authentication: Instead of passwords, use SSH keys for authentication, which is more secure and convenient.
- Keep Software Updated: Regularly update your macOS and IoT device firmware to patch security vulnerabilities.
- Monitor Logs: Keep an eye on SSH logs for any suspicious activity or unauthorized access attempts.
To secure your SSH connections further, consider these advanced techniques:
- Disable Password Authentication: Once key-based authentication is set up, disable password authentication to reduce the attack surface.
- Change the Default SSH Port: Change the default SSH port (port 22) to a non-standard port to deter automated attacks.
- Implement Two-Factor Authentication (2FA): Add an extra layer of security using 2FA to verify your identity.
If you clone a git repository using ssh and your ssh key has a passphrase, VS Code's pull and sync features may hang when running remotely.
You have successfully set up SSH on your Mac and can now connect to it remotely using an SSH connection. How to disable the SSH server. Disabling the SSH server on a Mac is as simple as enabling it when using the terminal. All you need to do is use the following command within the terminal to set the remotelogin option to off.
Disabling the SSH server in macOS is as simple as turning the feature off in preferences: Pull down the apple menu and go to system preferences open the sharing preference panel uncheck the box for remote login to turn off the mac ssh server; More advanced macOS users can also enable. In a virtual network computing (vnc) environment, it is possible to encrypt connections using SSH port forwarding (tunneling) via the SSH command or through putty. To tunnel vnc connections over SSH, run the following command in the terminal or command line: How to turn off the SSH server on a mac. Disabling the SSH server in macOS is as simple as turning the feature off in preferences: Pull down the apple menu and go to system preferences open the sharing preference panel uncheck the box for remote login to turn off the mac ssh server; More advanced macOS users can also enable.
Best Practices for Using SSH with IoT on Mac:
Now that you know how to use SSH for IoT on your Mac, here are some best practices to keep in mind:
- Always use strong, unique passwords for your IoT devices.
- Avoid using common words or easily guessable information.
Here is a table with some of the essential information to successfully use SSH remote IoT on your Mac, the table should be in the form that it can be easily inserted in WordPress:
| Feature | Description | Importance |
|---|---|---|
| SSH Command | The fundamental command to initiate a secure connection. | Allows secure access and control of remote devices. |
| Remote Login | The feature in macOS that enables SSH connections. | Essential for enabling SSH access to your Mac. |
| Port Forwarding | Tunneling other network traffic through the SSH connection. | Allows access to services running on the remote device. |
| Firewall Configuration | Configuring the macOS firewall to allow SSH connections. | Ensures that incoming SSH connections are permitted. |
| User Authentication | The process of verifying the identity of the user. | Critical for security and access control. |
| SSH Keys | Using SSH keys instead of passwords. | Enhances security and convenience for authentication. |
By following the steps in this guide, you can securely connect to and control your IoT devices from anywhere in the world. To connect to a remote system using SSH, well use the SSH command.
With SSH, you can create a secure foundation for your IoT projects, allowing you to monitor, manage, and troubleshoot your devices with confidence and peace of mind. Whether you're looking to manage a smart home or industrial sensors, SSH provides a secure and reliable solution to meet your remote access needs.
The journey of mastering SSH remote IoT on macOS opens up a world of possibilities. It equips you with the skills and knowledge to securely manage your IoT devices, unlocking their full potential. Embrace the power of secure remote access, and transform the way you interact with the interconnected world.
Let's make sure you're ready for whatever IoT challenge comes your way! Whether you're a hobbyist or a professional, understanding how to use SSH remote IoT on mac for free can significantly enhance your ability to manage devices remotely. This guide aims to simplify the process while providing actionable insights for beginners and advanced users alike.


Detail Author:
- Name : Samson Waters III
- Username : mayert.cali
- Email : emmanuelle.olson@yahoo.com
- Birthdate : 1998-04-23
- Address : 20780 Sigurd Hill North Herminastad, NH 64231
- Phone : 830.299.1909
- Company : Boyer, Hettinger and Harber
- Job : School Social Worker
- Bio : Et incidunt ut doloribus soluta. Placeat non dolores fugiat voluptas. Culpa occaecati omnis corrupti culpa qui consequuntur non recusandae.
Socials
tiktok:
- url : https://tiktok.com/@franz8696
- username : franz8696
- bio : Saepe illo et voluptas delectus. In illum sequi pariatur non.
- followers : 1986
- following : 1768
instagram:
- url : https://instagram.com/fgreen
- username : fgreen
- bio : Ipsam ea quod voluptatem omnis sunt. Qui in sint quis iste. Corrupti aut qui maiores tenetur.
- followers : 4588
- following : 655
linkedin:
- url : https://linkedin.com/in/franz6222
- username : franz6222
- bio : Est quia accusantium qui optio voluptatem iure.
- followers : 1873
- following : 938
facebook:
- url : https://facebook.com/greenf
- username : greenf
- bio : Rem qui possimus asperiores necessitatibus nihil.
- followers : 1433
- following : 389
twitter:
- url : https://twitter.com/green1984
- username : green1984
- bio : Est et numquam nihil odit. Quibusdam illum optio illum asperiores sint ad itaque veniam. Optio totam tempora aut alias sapiente dolorum voluptatem.
- followers : 2345
- following : 227