Unlock Remote Device Access: AWS IoT Secure Tunneling Guide
Are you grappling with the challenge of accessing and managing your Internet of Things (IoT) devices deployed remotely, especially when they are guarded by robust firewalls? The answer lies in a sophisticated solution: AWS IoT Secure Tunneling, designed to establish secure, bidirectional communication with devices situated behind firewalls, all managed seamlessly by AWS IoT.
The realm of IoT is rapidly expanding, with devices becoming increasingly prevalent in diverse settings. However, the challenge of accessing and managing these devices, particularly when they are deployed behind firewalls that restrict inbound traffic, has long been a stumbling block. Traditional methods often involve sending technicians on-site, a process that is not only time-consuming but also escalates operational costs. This is where AWS IoT Secure Tunneling steps in, offering a streamlined and secure approach to remote device access and management.
| Feature | Details |
|---|---|
| Secure Connection | AWS IoT Secure Tunneling establishes a secure, bidirectional communication channel. This ensures that data transmitted between your local device and the remote device is encrypted and protected. |
| Firewall Agnostic | One of the key advantages of AWS IoT Secure Tunneling is its ability to bypass the need for updates to existing inbound firewall rules. This means you can maintain the same level of security provided by your firewall while enabling remote access. |
| Management by AWS IoT | The entire tunneling process is managed by AWS IoT, simplifying the setup and maintenance. AWS handles the complexities of establishing and maintaining the secure connection, allowing you to focus on your core business logic. |
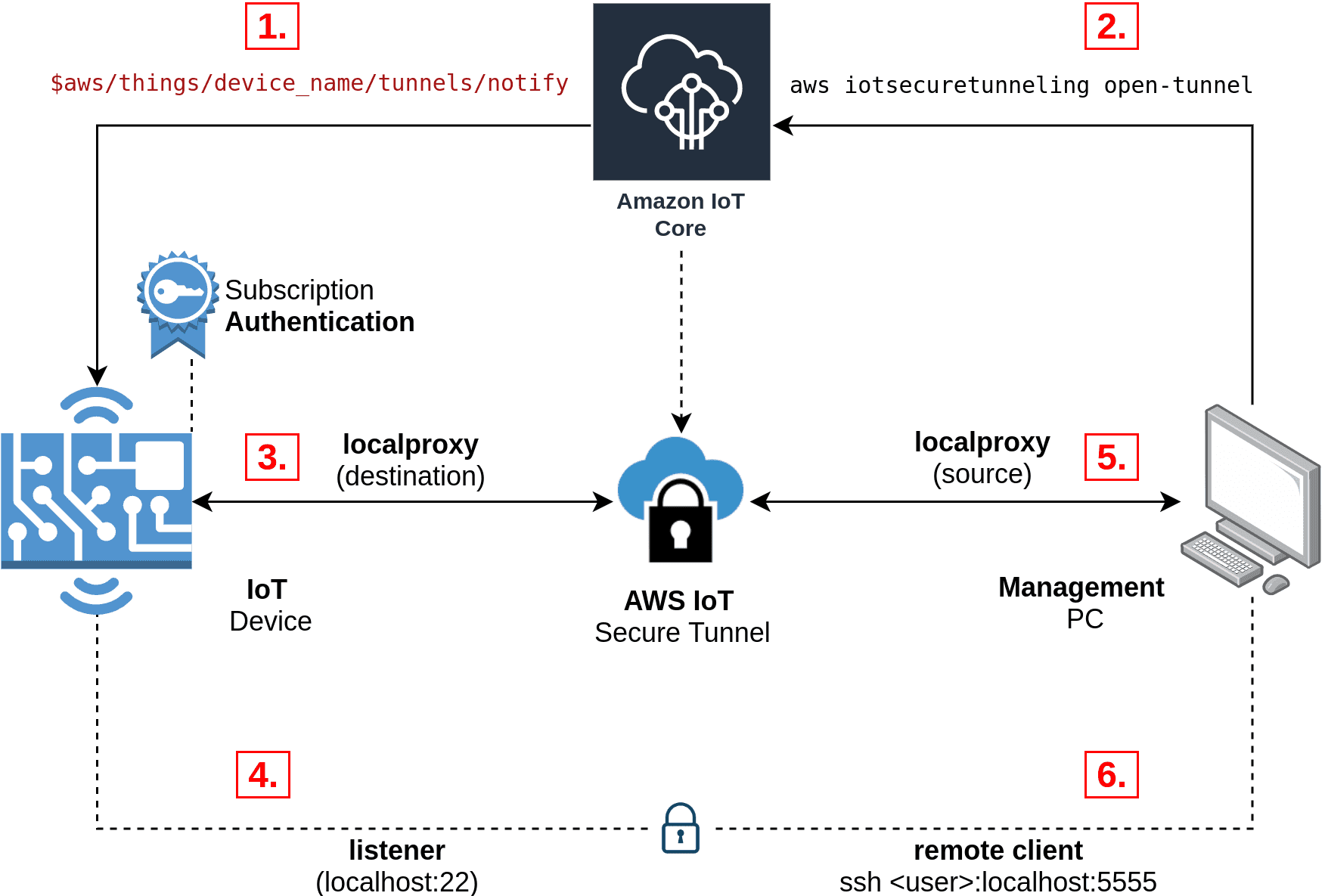
| Client Access Tokens | Upon initiating a tunnel through the AWS IoT Secure Tunneling management API, you receive a pair of client access tokens. One token is for the source local proxy, and the other is for the destination. These tokens are used to connect two local proxy clients, which act as intermediaries at each end of the tunnel. |
| Bidirectional Communication | AWS IoT Secure Tunneling allows for bidirectional communication, enabling you to send commands to the remote device and receive responses back, facilitating troubleshooting, configuration updates, and other operational tasks. |
| Multiplexing | A single tunnel can support up to three data streams simultaneously through tunnel multiplexing. This allows for efficient use of the tunnel connection. |
| Timeout Settings | For enhanced security, you can specify a timeout on the client access tokens, limiting the duration for which they are valid. This reduces the risk if the tokens are leaked. |
| Remote Operations | AWS IoT Secure Tunneling enables you to carry out remote operations such as accessing remote devices for troubleshooting, configuration updates, and other operational tasks. |
| Integration with AWS SDKs | The service integrates with AWS SDKs, allowing developers to seamlessly incorporate secure tunneling into their applications using code examples and comprehensive documentation. |
For further information, please visit the official AWS documentation: AWS IoT Secure Tunneling
To get started with AWS IoT Secure Tunneling, you can leverage the AWS IoT Secure Tunneling demo available on GitHub. This demo provides practical examples and code snippets to help you quickly understand and implement secure tunneling in your projects. This demo will guide you through the process of establishing bidirectional communication with remote devices over a secure connection managed by AWS IoT. By using this demo, you can quickly configure and test your secure tunneling setup, and see how it works with different types of devices and network configurations.
One of the compelling advantages of Secure Tunneling is its non-intrusive nature. It doesn't require alterations to your current firewall rules. This simplifies deployment and maintains the security level afforded by existing firewall configurations. The service is integrated with AWS SDKs, facilitating straightforward integration into your existing IoT projects. Numerous code examples offer a clear understanding of how to implement the basics of AWS IoT with the AWS SDKs. This feature is especially valuable for companies that have strict security policies.
The core of AWS IoT Secure Tunneling involves the creation of a secure channel. The `OpenTunnel` action within the AWS IoT Secure Tunneling management API is a pivotal element. This action generates a pair of client access tokens. These tokens are designed for use by two local proxy clients, one at the source and one at the destination of the tunnel. The source local proxy utilizes one token, while the destination uses the other. This token-based system ensures the security of the connection and permits the establishment of bidirectional communication.
The implementation of AWS IoT Secure Tunneling is designed to be flexible, offering robust support for diverse operational tasks. Secure tunneling enables remote operation capabilities such as sending commands to devices and receiving responses. Whether it's configuring settings, updating software, or diagnosing operational issues, this capability dramatically decreases the need for on-site technicians. By enabling remote access, it significantly reduces both the complexity and costs associated with device management.
The process of establishing a tunnel begins with creating a new tunnel. This can be accomplished through the AWS IoT Secure Tunneling management API. During this phase, the system generates two client access tokens. These tokens play a critical role, as they are used by the clients to establish a connection to the AWS IoT Secure Tunneling proxy server. This ensures the secure exchange of data. You have the ability to define a specific tunnel duration, tailored to your operational requirements.
For enhanced security, you can set a timeout on the credentials. This timeout setting serves to limit the period of time during which the generated tokens remain valid. This practice helps to mitigate the potential risks associated with token compromise. It's recommended to keep this value low to minimize the exposure. If the tokens are leaked, they will naturally expire, which reduces the potential impact.
One can easily connect to the destination device. You can do this from your laptop or desktop computer. This is achieved by utilizing the AWS Cloud. This is a significant advantage, streamlining device management and enabling efficient data transfer and interaction.
When working with AWS IoT Secure Tunneling, it's crucial to recognize the role of policies. You must apply particular policies to authorize permissions for using the Secure Tunneling API. These policies dictate the access rights and permissions granted. They're crucial for maintaining security and ensuring that only authorized entities can interact with the service.
AWS IoT Secure Tunneling incorporates the use of multiplexing. A single tunnel can accommodate up to three data streams simultaneously. This multiplexing capability increases the efficiency of data transfer. It allows for multiple tasks or processes to occur at the same time. This feature is particularly useful when managing devices that require multiple types of communication.
Bandwidth management is an essential element to take note of. There's a predefined limit to the bandwidth that a tunnel can handle. It's essential to consider this limit when planning the data streams and activities that will occur through the tunnel. This limit is mentioned in the AWS public documentation under the section "aws iot secure tunneling", in the "maximum bandwidth per tunnel" row. Understanding the bandwidth limitations ensures optimum performance and efficient use of the tunnel.
The bandwidth for a multiplexed tunnel is the bandwidth consumed by all active streams transferring data via the tunnel connection. The bandwidth used by a tunnel is affected by the amount of data transmitted across all active streams. Consequently, the overall tunnel bandwidth must be carefully considered to maximize the efficiency of data transmission and guarantee reliable performance. Monitoring the bandwidth is essential to avoid bottlenecks and guarantee a seamless experience. Additionally, a good understanding of this helps in optimization for effective IoT operations.
The power of firewalls is undeniable in protecting and securing access to IoT devices. Yet, the reality is that accessing and managing devices deployed in remote locations, especially when behind firewalls, is complicated. The need to send technicians on-site for troubleshooting, for example, becomes a bottleneck, increasing the complexity and expense. This is where Secure Tunneling steps in, providing a secure pathway to manage your IoT assets, no matter their location.
Consider the scenario where devices are deployed behind restrictive firewalls at remote sites. In such cases, obtaining access for tasks like troubleshooting, configuration updates, and other operational duties is essential. Secure Tunneling, a component of AWS IoT device management, directly addresses this challenge. It helps users perform remote tasks securely and efficiently.
The code examples show how to use the basics of AWS IoT with AWS SDKs. This aids those who are new to AWS and IoT to understand how the concepts are implemented in the real world. These examples give a starting point for using the AWS IoT Secure Tunneling service and give a chance to learn about and configure tunnels for their particular device management scenarios. These code examples are useful for users who wish to put theory into practice.
For AWS IoT security details, review the identity and access management for AWS IoT. This document offers in-depth insights into security practices, including details on how to properly apply security policies and access controls to the AWS IoT Secure Tunneling service. AWS IoT is designed with security as a top priority. It provides many features and best practices to aid in securing your IoT infrastructure. It includes features like encryption, access control, and identity management to assist in creating a secure IoT environment.
To summarize, AWS IoT Secure Tunneling offers a powerful solution for securely managing and accessing remote devices, even when they are located behind firewalls. It simplifies device management, reduces operational costs, and enhances security, making it an indispensable tool for modern IoT deployments. By understanding the core concepts, configuration steps, and best practices associated with AWS IoT Secure Tunneling, you can harness its full potential and ensure that your IoT deployments are secure, efficient, and adaptable to the ever-changing needs of the IoT landscape.


Detail Author:
- Name : Francesco Gorczany
- Username : francisca64
- Email : lorena.metz@hotmail.com
- Birthdate : 1994-01-31
- Address : 18573 Farrell Parks Kennediville, TX 25381-7303
- Phone : 1-970-617-3735
- Company : Green Ltd
- Job : Mental Health Counselor
- Bio : Qui rerum iste minima porro distinctio in in. Vero et cupiditate et soluta fugiat provident dignissimos. Itaque enim labore eaque optio. Et et alias asperiores esse illum voluptate minus.
Socials
tiktok:
- url : https://tiktok.com/@klabadie
- username : klabadie
- bio : Sint quisquam debitis dolorem. Alias sit eum id deserunt consequatur quisquam.
- followers : 809
- following : 698
instagram:
- url : https://instagram.com/kurtlabadie
- username : kurtlabadie
- bio : Veritatis et maiores dolorem eos at. Ullam aspernatur dolorum eos deserunt esse in impedit.
- followers : 4926
- following : 357