IoT Security: SSH Tunneling & Remote Access Explained
Are you grappling with the challenges of accessing and managing your Internet of Things (IoT) devices, especially when they are deployed in remote locations, shielded behind firewalls that restrict inbound traffic? The very nature of IoT, with its widespread deployment and often intricate network configurations, demands robust and secure remote access solutions.
The modern landscape of the Internet of Things (IoT) presents both unprecedented opportunities and complex hurdles. As organizations increasingly integrate IoT devices into their operations, the need for secure and efficient remote access becomes paramount. Traditional methods, often involving on-site visits by technicians, not only increase costs but also introduce operational delays. This article delves into the intricacies of SSH tunneling as a solution for remotely accessing and managing IoT devices, focusing on AWS IoT Secure Tunneling as a prime example.
The cornerstone of any effective IoT deployment lies in the ability to securely and remotely manage the devices. Firewalls, while essential for protecting against unauthorized access, frequently complicate this aspect. The conventional approach of sending technicians to connect to devices on-site is time-consuming, expensive, and often impractical. This is where secure tunneling solutions like SSH come into play.
At its core, SSH tunneling facilitates the transportation of arbitrary networking data over an encrypted SSH connection. This allows for secure access to devices without needing to alter firewall settings or know the device's IP address. In essence, all data transmitted is encapsulated within an encrypted SSH tunnel, adding an additional layer of security.
AWS IoT Secure Tunneling provides a robust solution to the remote access challenge. By creating a secure tunnel to your IoT device, you can perform remote operations over SSH. This method eliminates the need to discover the IoT device IP and circumvents the limitations of firewall configurations, thereby simplifying the management process. When opting for this solution, users are able to SSH into their IoT devices using system user or SSH key-based secure authentication, and the standard client tools like PuTTY. It is also worth noting, the alternative method for remotely connecting to your IoT device's SSH server is the socketxp solution.
SSH tunneling offers a secure method to establish remote access, a technique especially valuable for devices behind NAT routers or firewalls. Furthermore, SSH tunneling is great for hobbyists, hackers, and professionals tinkering with IoT devices. The quick setup method allows for access token rotation and SSH access into the remote device directly from the browser, enhancing usability. The setup requires the creation of an IoT thing in the AWS IoT registry. Furthermore, it is also possible to create a tunnel from the thing details page of the AWS IoT console and to specify whether to create a new tunnel or open an existing one.
- Explore Latest Telugu Movies More Movierulz Updates
- Webtoon Mod Apk 2025 Download Enjoy Free Features
SSH reverse proxy tunneling offers a secure avenue for remote access, especially for devices located behind firewalls or NAT routers. This method proves beneficial when a local service needs to be exposed to a remote machine without requiring open ports on the local network.
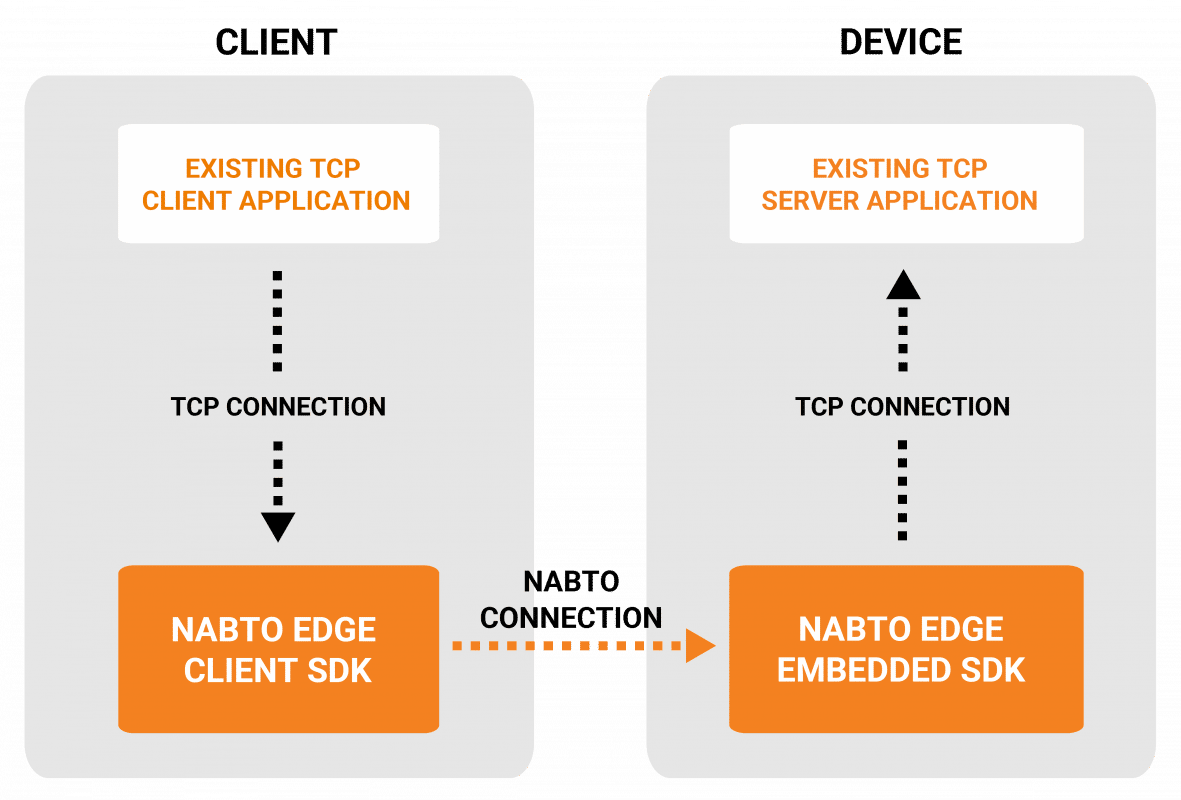
However, as with any technology, it's crucial to acknowledge that SSH tunneling isn't the only option available. Alternatives such as Nabto Edge TCP tunneling exist, offering unique advantages for IoT solutions. Nabto Edge provides IoT developers with greater control and input from IoT experts. SSH, in comparison to Nabto Edge, requires more effort in terms of setup.
When you are no longer in need of the test, confirm the deletion and also delete tunnel to avoid any ongoing charges, you will have to delete any infrastructure that you have created for this test.
Key Advantages of SSH in IoT Deployments
Secure Shell (SSH) presents a range of compelling advantages for establishing secure communication in IoT deployments. Some of the key benefits of using SSH in IoT are detailed below:
- Data Encryption: SSH provides data encryption, ensuring that the data exchanged between devices is secure from eavesdropping.
- Access Control: SSH facilitates fine-grained access control, allowing you to restrict who can access the device and what actions they can perform.
- Secure Communication: SSH creates a secure tunnel for data transmission, guarding it from interception or tampering.
- Simplified Remote Access: SSH simplifies remote access to your IoT devices, making it easier to manage and troubleshoot them from a distance.
- No need for IP discovery: With SSH, you don't need to discover the IP address of the IoT device.
- Firewall friendly: SSH can tunnel through firewalls, allowing access without having to change firewall settings.
In the following table, we explore different benefits of Secure Shell (SSH) in IoT deployments.
| Benefit | Description |
|---|---|
| Encrypted Communication | All data transmitted through the SSH tunnel is encrypted, ensuring confidentiality and preventing eavesdropping. |
| Secure Authentication | SSH supports strong authentication methods (e.g., SSH keys) to verify the identity of the connecting user or device, reducing the risk of unauthorized access. |
| Port Forwarding | SSH tunneling can forward ports, allowing access to services running on the IoT device (e.g., web servers, databases) without opening those ports directly to the internet. |
| Firewall Traversal | SSH can traverse firewalls and NAT routers, allowing remote access to IoT devices that would otherwise be inaccessible. |
| Simplified Management | SSH provides a secure and straightforward way to manage IoT devices remotely, including updating software, configuring settings, and troubleshooting issues. |
| Data Integrity | SSH includes mechanisms to ensure the integrity of transmitted data, protecting against data corruption or tampering. |
| Versatility | SSH can be used for various tasks, including remote command execution, file transfer, and creating secure connections to other services. |
By understanding these benefits, IoT developers can fully utilize SSH to create a more secure and maintainable environment.
AWS IoT Secure Tunneling
AWS IoT Secure Tunneling facilitates the creation of a secure tunnel to your IoT device and facilitates remote operations through SSH. This secure tunnel allows for remote access without the need to discover the device's IP address or modify firewall configurations. All data is transported within an encrypted SSH tunnel, ensuring security. The core concept involves utilizing the device proxy, which operates as a client establishing a connection with the SSH daemon on the IoT device. Both proxy applications then tunnel the traffic between local instances and the IoT hub streaming endpoint, creating a copying process between two streams.
To leverage AWS IoT Secure Tunneling, you typically need to create an IoT thing within the AWS IoT registry. This "thing" serves as a representation of your IoT device within the AWS ecosystem. When creating a tunnel from the thing details page of the AWS IoT console, you have the option to create a new tunnel or open an existing one. To manage your tunnels, you can navigate to the Tunnels hub in the AWS IoT console, select the desired tunnel, and view its details. From there, you can expand the Secure Shell (SSH) section and initiate a connection. Note that to avoid ongoing charges, remember to delete the tunnel and any associated infrastructure after use.
Reverse SSH Tunneling
Reverse SSH tunneling is an essential technique for establishing a secure connection from a remote server or IoT device back to a local machine. At its core, it involves establishing an encrypted SSH connection in the opposite direction from what is typically done. This method is particularly useful when you need to expose a service running on a local machine to a remote machine, even if the local machine is behind a NAT router or firewall. A reverse SSH tunnel allows you to forward a port, enabling access to the service running on your local machine from the remote location.
| Reverse SSH Tunneling - How it Works | |
|---|---|
| 1. Initiate the Connection | The remote machine (or IoT device) initiates an SSH connection to the local machine (e.g., a server with a public IP). |
| 2. Port Forwarding Configuration | The local machine's SSH server is configured to listen on a specific port and forward traffic received on that port to a port on the remote machine. |
| 3. Traffic Flow | When a connection is made to the specified port on the local machine, the SSH server forwards the traffic through the secure tunnel to the specified port on the remote machine. |
| 4. Security | All data is encrypted as it passes through the SSH tunnel, providing a secure channel for communication. |
This setup proves invaluable for various scenarios, including:
- Accessing a local development environment from a remote location.
- Exposing a service running on a home network (e.g., a web server) to the internet.
- Managing an IoT device located behind a firewall without opening specific ports.
By understanding the mechanics of reverse SSH tunneling, you can create highly flexible and secure remote access solutions.
Step-by-Step
Setting up an SSH tunnel, especially to a device like a Raspberry Pi, might seem daunting at first. However, by following a structured approach, you can securely supervise your IoT networks. This guide aims to simplify the process, ensuring the confidentiality of your data and safety.
- Prerequisites:
- An IoT device with an SSH server installed and configured.
- A local machine from which you'll initiate the SSH tunnel (e.g., your laptop).
- An SSH client (e.g., PuTTY, OpenSSH) installed on your local machine.
- Network connectivity between your local machine and the IoT device.
- Establishing the SSH Tunnel:
- Open your terminal or SSH client.
- Use the following command to establish the SSH tunnel (adjust the parameters according to your setup):
ssh -L [local_port]:[iot_device_ip]:[remote_port] [username]@[server_ip]- Replace:
[local_port]with the port on your local machine to access the service.[iot_device_ip]with the IP address of your IoT device.[remote_port]with the port on your IoT device that the service is running on.[username]with the username for SSH access to your IoT device.[server_ip]with the IP address or hostname of your IoT device.
- Example:
ssh -L 8080:192.168.1.100:80 pi@192.168.1.101(This forwards local port 8080 to the webserver on the IoT device).
- Accessing Services Through the Tunnel:
- Once the tunnel is established, access the service on your local machine using the specified local port.
- For instance, if you've set up a tunnel for a web server running on port 80 of your IoT device, you would open a web browser and go to
http://localhost:8080(assuming you used the example command above).
- Maintaining Security:
- Ensure your SSH keys are securely managed.
- Regularly update your IoT device's software to patch security vulnerabilities.
- Close the SSH tunnel when not in use.
By following these steps, you can create a secure and efficient way to access and manage services on your IoT devices from a remote location.
Tunnel Duration and Tunnel Management
The ability to manage and control the lifespan of your tunnels is critical for maintaining security and preventing unauthorized access. Tunnels can be configured with a specific duration, after which they automatically close. This feature helps to limit the window of vulnerability and ensures that tunnels are not left open indefinitely. If a tunnel's duration expires, the tunnel will be closed. It is important to note that once a tunnel has closed, it cannot be reopened.
For duplicating a tunnel, open the closed tunnel and then select the option for duplicating the tunnel. Then you need to specify the duration of the new tunnel and then create it.
Alternative Solutions
While SSH tunneling presents a solid solution, it's essential to consider alternative methods, such as Nabto Edge TCP tunneling. Nabto Edge TCP tunneling gives IoT developers greater control. Nabto Edge offers various benefits that may make it a more appropriate choice for your IoT solution.
Key differences between Nabto Edge and SSH tunneling for IoT solutions:
- Simplicity: Nabto Edge is often simpler to deploy and manage, particularly for non-technical users.
- Control: Nabto Edge gives IoT developers greater control over the end-to-end process.
- Expert input: Nabto Edge includes input from IoT experts during setup and ongoing use.
In some scenarios, such as needing to expose a local service to a remote machine, SSH reverse proxy tunneling provides a secure solution, creating an encrypted SSH connection.
In essence, the approach involves configuring an SSH client on the remote machine to connect back to the local machine and forward traffic. This allows the remote machine to access local services as if they were running locally.
Best Practices and Conclusion
Securing your IoT environment is a multifaceted undertaking that requires a comprehensive approach. While AWS IoT Secure Tunneling and SSH tunneling solutions offer robust methods for remote access and management, it's equally important to adhere to best practices. This includes regularly updating your devices' software, employing strong authentication mechanisms (such as SSH keys), and continuously monitoring your network for suspicious activities. Regularly review and modify tunnel settings to meet changing security requirements.
In conclusion, the convergence of IoT and remote access solutions underscores the importance of secure and efficient device management. SSH tunneling, with its encryption and port forwarding capabilities, provides a powerful tool for securing remote connections to IoT devices. AWS IoT Secure Tunneling further streamlines this process, providing a managed service that simplifies deployment and management. By embracing these technologies and following best practices, you can create a secure and dependable IoT infrastructure, safeguarding data confidentiality and maintaining control over your devices, no matter their physical location.


Detail Author:
- Name : Francesco Gorczany
- Username : francisca64
- Email : lorena.metz@hotmail.com
- Birthdate : 1994-01-31
- Address : 18573 Farrell Parks Kennediville, TX 25381-7303
- Phone : 1-970-617-3735
- Company : Green Ltd
- Job : Mental Health Counselor
- Bio : Qui rerum iste minima porro distinctio in in. Vero et cupiditate et soluta fugiat provident dignissimos. Itaque enim labore eaque optio. Et et alias asperiores esse illum voluptate minus.
Socials
tiktok:
- url : https://tiktok.com/@klabadie
- username : klabadie
- bio : Sint quisquam debitis dolorem. Alias sit eum id deserunt consequatur quisquam.
- followers : 809
- following : 698
instagram:
- url : https://instagram.com/kurtlabadie
- username : kurtlabadie
- bio : Veritatis et maiores dolorem eos at. Ullam aspernatur dolorum eos deserunt esse in impedit.
- followers : 4926
- following : 357