Secure IoT Devices: Your Guide To Remote SSH Access
Are you ready to unlock the full potential of your IoT devices and manage them securely from anywhere in the world? Securing your IoT devices with Secure Shell (SSH) is not just a technical necessity; it's a fundamental step towards safeguarding your data and ensuring operational efficiency in an increasingly connected world.
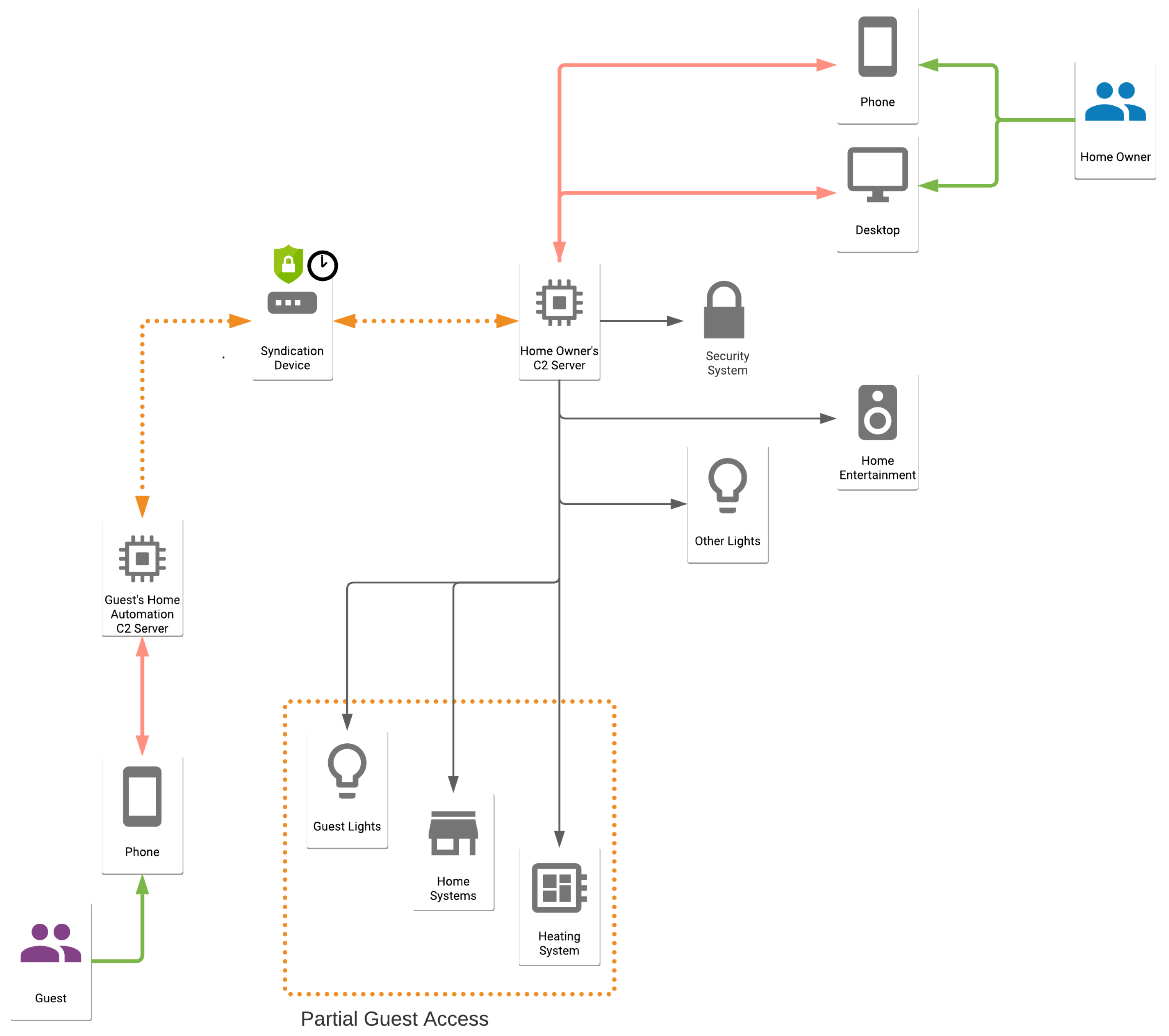
Imagine a world where your smart home system, equipped with thermostats, security cameras, and lighting controls, is seamlessly integrated into your daily life. Now, picture being able to access and control each of these devices, regardless of your physical location, with a level of security that rivals the most sophisticated enterprise systems. This is the promise of IoT device remote SSH, or Secure Shell, a protocol that acts as a virtual key, granting you access to your IoT gadgets from anywhere with an internet connection. This article serves as your guide to navigating the intricacies of SSH within the realm of IoT, providing you with the knowledge and tools to not only understand but also implement these critical security measures.
Before we dive deep, let's establish a clear understanding of the core concepts. SSH, at its essence, is a cryptographic network protocol that allows you to establish a secure channel to a remote device. This secure channel ensures that all data transmitted between your device and the remote server, or vice versa, is encrypted, protecting it from eavesdropping and tampering. In the context of IoT, SSH provides a reliable and secure method to access and control devices, manage configurations, and troubleshoot issues remotely. We'll be using Amazon Web Services (AWS) as the infrastructure for this setup, with the Raspberry Pi acting as our example device. The Raspberry Pi's versatility and widespread adoption make it an ideal platform for demonstrating these concepts. This approach is particularly relevant for businesses or individuals managing a fleet of IoT devices, such as security cameras, smart lighting systems, and environmental sensors. Remote access and management are crucial for operational efficiency.
The table below outlines some fundamental data related to the application of SSH in IoT devices.
| Category | Details |
|---|---|
| Definition | The use of the Secure Shell (SSH) protocol to establish secure connections between IoT devices and remote servers. |
| Purpose | To enable secure remote access, management, and communication between IoT devices and their controlling systems. |
| Key Features |
|
| Applications |
|
| Benefits |
|
| Tools & Technologies |
|
| Security Considerations |
|
| Advanced Features |
|
| Reference Website | AWS IoT - What is IoT? |
This guide is tailored for a broad audience, including tech enthusiasts, developers, and business professionals who wish to enhance their IoT device management and cybersecurity. You'll learn to leverage SSH effectively for your projects, understand various SSH IoT device examples, and how these contribute to a secure IoT ecosystem. Consider the scenario of a small business owner managing a fleet of IoT devices. The ability to remotely access and control these devices securely becomes a paramount concern. Ssh remote IoT examples provide a secure and reliable way to manage such devices, offering peace of mind while keeping your IoT communications private and protected.
Let's explore the core functionality. When you establish an SSH connection, youre essentially creating a secure tunnel. This tunnel encrypts all data transmitted between your device and the IoT device, preventing unauthorized access. Imagine your IoT devices as locked doors, and SSH as the key. Properly configured, SSH grants authorized users secure access to manage, monitor, and maintain these devices from anywhere in the world. One of the critical applications of SSH is in securing the remote access and control of these devices, it guarantees that data is shielded during transmission and that only authorized users have access.
Here are some practical examples of using SSH for IoT devices. Consider temperature monitoring with a Raspberry Pi. By using SSH, you can securely connect to the Pi and retrieve the temperature data remotely. This could be valuable for monitoring conditions in a remote location or for data logging purposes. AWS IoT Secure Tunneling takes this a step further by establishing bidirectional communication to remote devices that are behind a firewall. This feature is managed by AWS IoT, ensuring a secure connection.
In the real world, this translates to using your Android device to remotely manage and control these IoT devices. The rise of smart devices and the Internet of Things (IoT) has made remote management via SSH on Android devices increasingly important. Similarly, in Ubuntu environments, SSH plays a crucial role in secure and efficient remote access to devices. The importance of IoT remote SSH connection examples cannot be overstated; they are pivotal in enabling secure and efficient remote access to these devices.
Setting up an SSH reverse proxy tunnel is a powerful technique. Imagine you have a web server running on your local machine on port 8080, but you want to make it accessible to a remote server on port 9090. An SSH reverse proxy tunnel allows you to achieve this, essentially creating a secure, encrypted connection that forwards traffic from the remote server to your local web server. This is a common approach for accessing services behind firewalls or in private networks. To get started, you initiate the tunnel, which often involves specifying the local port and the remote server's address. The traffic is then routed through this secure tunnel. Deviceproxy, which represents a local proxy for your IoT device, acts as a client for the local SSH daemon. It's responsible for authenticating against the IoT hub and creating a WebSocket connection to the streaming endpoint. This setup ensures a secure and reliable connection.
The commands that you will use form the foundation of SSH operations in a remote IoT setting, are indispensable for managing IoT networks. In addition to basic commands, advanced SSH features, such as port forwarding and tunneling, can enhance the functionality of remote IoT SSH setups. Whether you're a developer, a system administrator, or a hobbyist, knowing how to use SSH to manage and configure IoT devices can greatly enhance your capabilities.
Consider the example of a small business using security cameras. With SSH, the business owner can securely access the camera's settings, view live feeds, and adjust configurations remotely. Similarly, for smart lighting systems, SSH allows for remote control of lights, adjusting schedules, and monitoring the system's status. For environmental sensors, such as those used in agriculture, SSH enables secure access to data and remote adjustment of sensor parameters. Connection to different devices, for example, via serial, SSH or telnet are also possible. The "PuTTY" software can be downloaded. The ability to manage and control these devices remotely, securely, is a cornerstone of effective IoT deployment.
The ability to remotely access, manage, and troubleshoot IoT devices is a cornerstone of modern device management. SSH provides a powerful and secure way to achieve this. By understanding the fundamental concepts and implementing the best practices, you can ensure that your IoT ecosystem is both functional and secure, ready for the challenges of today's connected world. This guide has offered you a solid foundation. Use it to build a more secure, manageable, and efficient IoT experience.


Detail Author:
- Name : Prof. Delilah Boyer
- Username : champlin.alex
- Email : greenfelder.stacy@yahoo.com
- Birthdate : 1987-02-17
- Address : 785 Spencer Walk Suite 268 West Cedrick, NV 39178
- Phone : 838.681.2011
- Company : Batz, Reichert and Streich
- Job : Agricultural Equipment Operator
- Bio : Expedita atque repudiandae optio. Est deserunt ipsum atque doloribus molestiae nam. Ut voluptatem deleniti architecto dolorum.
Socials
facebook:
- url : https://facebook.com/catharine.batz
- username : catharine.batz
- bio : Dolores quos laboriosam ab ullam cupiditate quibusdam.
- followers : 4446
- following : 713
tiktok:
- url : https://tiktok.com/@cbatz
- username : cbatz
- bio : Animi officia amet eum repudiandae beatae qui qui.
- followers : 950
- following : 1513
instagram:
- url : https://instagram.com/batz1993
- username : batz1993
- bio : Sit magnam quae quod enim nam est qui. Consectetur aut fugiat in. Velit et beatae ut ipsa facere.
- followers : 4165
- following : 1562
linkedin:
- url : https://linkedin.com/in/catharine9518
- username : catharine9518
- bio : Voluptatem ut eum soluta.
- followers : 1119
- following : 1356