Secure Remote IoT: P2P SSH On Windows 10 - Your Guide!
Are you wrestling with the complexities of managing and securing your Internet of Things (IoT) devices? Ensuring the secure connection of remote IoT devices using Peer-to-Peer (P2P) Secure Shell (SSH) on Windows 10 is no longer a luxury, but a fundamental requirement for anyone navigating the increasingly interconnected landscape of the digital age. This guide serves as your comprehensive compass, steering you through the intricacies of establishing secure and efficient communication channels for your IoT ecosystem.
The path to securing your IoT infrastructure begins with understanding the core principles and practical implementations of P2P SSH on Windows 10. The growth of the Internet of Things (IoT) continues to surge, and the need for securing connections between devices has reached unprecedented levels. This demand necessitates a robust, secure, and easily manageable solution, and P2P SSH on Windows 10 provides precisely that.
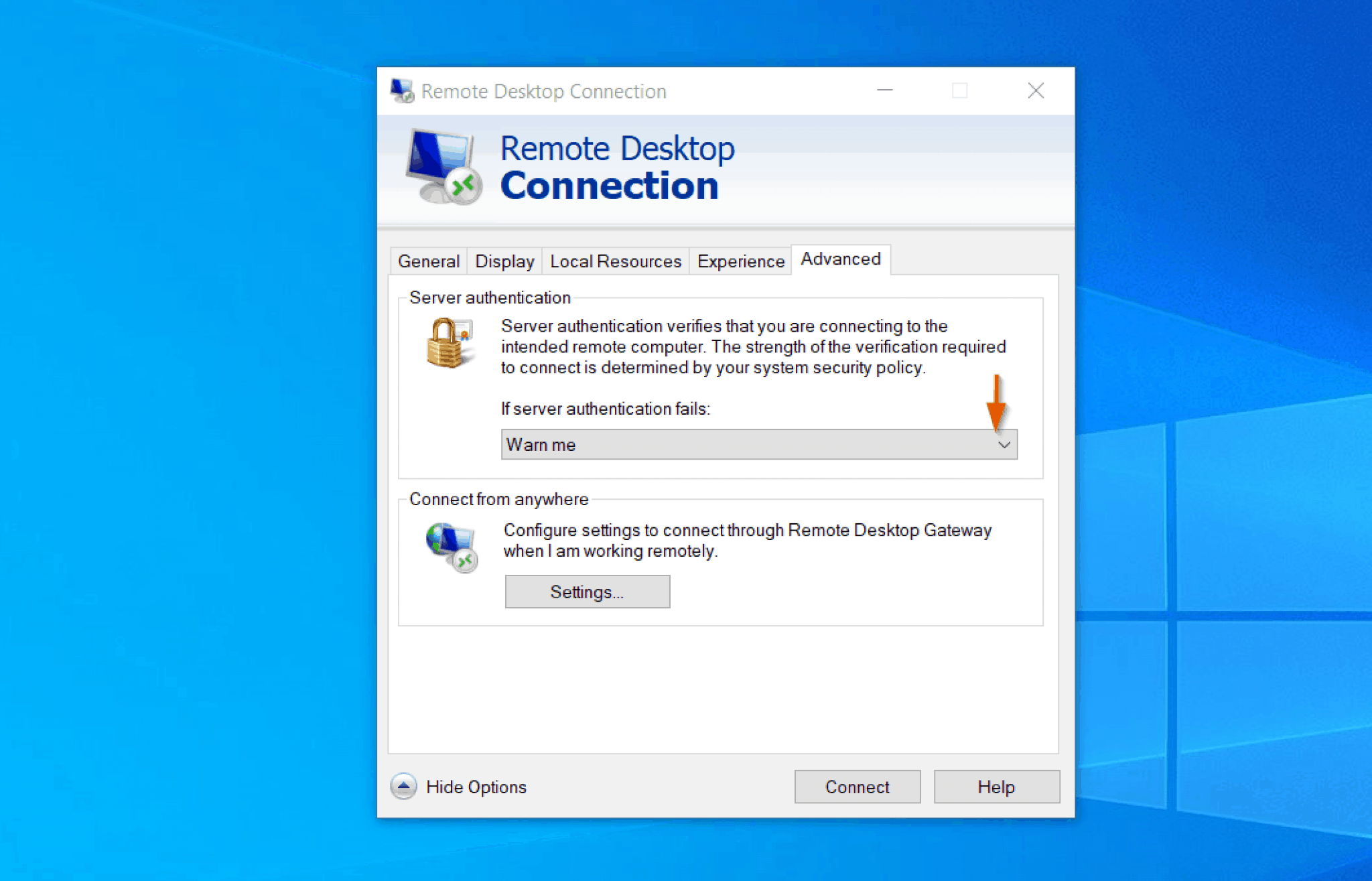
The foundation of this secure connection lies in the RemoteIoT client. This software acts as the central nervous system of your connection, facilitating smooth communication between your local machine and the remote IoT devices. Windows 10's native OpenSSH capabilities bring the essential tools needed to forge these secure, direct connections. This integration allows for straightforward implementation and seamless security management without requiring additional third-party installations.
- Ella Cervetto Unveiling Her World On Instagram Onlyfans
- Kino Yves Net Worth How He Built His Empire Earnings
Let's dive into the specific steps needed to establish a secure P2P SSH connection. The first, and arguably most crucial, step is installing an SSH client. This could involve the installation of the RemoteIoT client or leveraging the OpenSSH tools that are integrated within the Windows 10 operating system.
The advantages of utilizing P2P connections, especially in the context of IoT device management, are numerous. It eliminates the need for complex configurations and reduces the reliance on intermediary servers. This direct communication model significantly enhances the security posture, as it minimizes potential attack vectors and protects your data. The practical application of P2P SSH on Windows 10 makes secure connections accessible to both tech enthusiasts and seasoned professionals, streamlining device management and enhancing overall security.
The following table offers a concise overview of the core components and configurations necessary to achieve a secure P2P SSH connection on Windows 10. These elements are key for understanding the process and effectively managing your IoT environment.
- Stray Kids Youngest In Age Birthday Maknae Facts
- New Keyboard Shortcuts Dns Tips App Info July 11 2024
| Component | Description | Configuration Considerations |
|---|---|---|
| SSH Client | The software used to initiate and manage the SSH connection. This could be the RemoteIoT client, or Windows 10's built-in OpenSSH client. | Ensure the client is properly installed and configured, with the correct settings for hostnames or IP addresses, port numbers, and authentication methods. |
| SSH Server | The SSH server is running on the remote IoT device, allowing incoming secure connections. | The server must be enabled and properly configured on the remote device. This includes setting up user accounts and authentication methods, allowing remote access, and configuring security settings. |
| P2P Network Connectivity | The underlying network setup facilitating the direct connection between the client and the remote device. This can be a local network, or it can be a more complex network configuration. | Requires the proper network configurations. This is essential to avoid any network-related issues like firewalls or port forwarding. |
| Authentication Credentials | The username and password or SSH keys required to authenticate to the remote IoT device. | Strong passwords or SSH keys are crucial to protect against unauthorized access. Regularly update credentials for added security. |
| Port Forwarding (if needed) | If your IoT device is behind a firewall or a NAT, this may require port forwarding to enable direct connections. | Verify the correct port forwarding rules on your router or firewall. Standard SSH uses port 22, but this can be configured for increased security. |
| Security Settings | Settings to optimize the security of your SSH connection. | Review and configure security settings like encryption ciphers, key exchange algorithms, and host key verification. |
Understanding the essential aspects of SSH is crucial. SSH, or Secure Shell, is a cryptographic network protocol operating over a secure channel. It is commonly used for secure remote login, command-line execution, and file transfer. Its importance in the context of IoT communications is paramount, as it provides a secure and encrypted means of communication, thus safeguarding sensitive data from unauthorized access or interception.
The benefits of utilizing a P2P connection within an SSH environment are considerable. P2P SSH establishes a direct, point-to-point connection, eliminating the need for intermediary servers. This direct communication model reduces latency, improves efficiency, and simplifies the network architecture. More importantly, it enhances security by minimizing potential attack vectors and protecting data from eavesdropping or tampering.
The implementation of P2P SSH on Windows 10 is far more manageable than one might imagine. Windows 10 provides built-in OpenSSH capabilities, removing the requirement for additional installations. This simplifies the process and allows for easy implementation. By following a few straightforward steps, you can configure your Windows 10 system to establish a secure, direct P2P connection with your IoT devices. This streamlines your ability to manage and monitor your IoT infrastructure, enhancing its overall utility and value.
Let's explore the intricacies of setting up and configuring OpenSSH on your Windows 10 system. This step-by-step guide will ensure a secure and efficient communication channel for your devices:
- Check for OpenSSH Client and Server Installation: Open the "Settings" app, navigate to "Apps" then "Optional features." Search for "OpenSSH Client" and "OpenSSH Server." If they are not installed, click "Add a feature" and install them.
- Enable OpenSSH Server Service: Type "services.msc" in the Windows search bar and open the "Services" application. Find the "OpenSSH SSH Server" service, right-click on it, and select "Properties." Set the startup type to "Automatic" and start the service if it's not already running.
- Configure the SSH Client (if not using RemoteIoT client): Open the Command Prompt or PowerShell. Use the `ssh` command to connect to your IoT device. You'll need the device's IP address and the username and password or SSH key. For example: `ssh user@`
- Authentication: Depending on the configuration, you might be prompted for your password or the pass phrase for your SSH key. Enter your credentials securely.
- Firewall Configuration (if needed): Ensure that your Windows Firewall allows incoming connections on port 22 (or the port you configured for SSH). You can add a new rule in the Windows Defender Firewall settings to allow TCP traffic on the specified port.
- Verification: Once connected, you can execute commands on your remote IoT device. Verify the connection by running a simple command.
- For RemoteIoT client: Once the RemoteIoT client is installed, you can connect to the IoT device through the RemoteIoT user interface. The client will handle the authentication and connection process automatically.
For individuals new to the field, connecting remote IoT devices using P2P SSH on Windows 10 is an increasingly vital skill for both enthusiasts and professionals. With the continuous growth of the Internet of Things (IoT), the ability to establish secure connections is no longer a luxury, but a necessity. This proficiency allows for remote device control, data collection, and efficient network management.
Further securing your IoT infrastructure involves adopting advanced techniques. Consider using SSH keys instead of passwords for authentication; this greatly increases the security of your connections. Regularly update your SSH client and server to benefit from the latest security patches. Implement two-factor authentication (2FA) where possible to add an extra layer of security. Regularly monitor logs for any suspicious activities. All these strategies can collectively create a robust and secure IoT ecosystem.
If you're seeking a reliable method to securely connect remote IoT devices using P2P SSH on Windows 10, consider the RemoteIoT P2P SSH solution. This offers a streamlined method for securely managing IoT devices, bypassing complicated configurations. It ensures seamless management of remote devices while prioritizing robust security measures, which is critical for both business and individual users in today's digital environment.
In this interconnected digital landscape, securely connecting remote IoT devices via P2P SSH on Windows 10 is not merely a technical task; it is a critical skill for securing your digital footprint. By implementing the steps outlined in this guide, you're not just establishing a connection; you're fortifying your data against potential threats.
For those seeking a deeper understanding, remember that every element is a piece of the larger puzzle. You'll gain the expertise to confidently manage and secure your IoT ecosystem. Your data will be protected at all times.


Detail Author:
- Name : Juliana Greenfelder III
- Username : dovie04
- Email : orie.pollich@gmail.com
- Birthdate : 2007-03-09
- Address : 2534 Gerhold Flats Bruenville, VT 63455-6515
- Phone : (904) 640-6639
- Company : Hill-Kuhic
- Job : Railroad Switch Operator
- Bio : In nisi corporis et ad. Quae eius fugiat aliquam magni explicabo expedita non.
Socials
twitter:
- url : https://twitter.com/fisher1989
- username : fisher1989
- bio : Magnam culpa sapiente suscipit quibusdam. Aut dolor pariatur ut nihil quia sequi soluta est. Est ab fugit ipsam ut adipisci occaecati.
- followers : 1387
- following : 1389
instagram:
- url : https://instagram.com/fisher1987
- username : fisher1987
- bio : Voluptas consequatur voluptas vel sunt laboriosam fuga et. Sit animi ab facilis non.
- followers : 6980
- following : 1380
facebook:
- url : https://facebook.com/fisher1986
- username : fisher1986
- bio : Autem temporibus ut voluptas neque et beatae. Tempore iste id aliquam totam ad.
- followers : 5150
- following : 1736
tiktok:
- url : https://tiktok.com/@macy_real
- username : macy_real
- bio : In qui est praesentium deleniti molestias quaerat.
- followers : 5047
- following : 2031