Edge Of Tomorrow: Tom Cruise In Time Loop War
Is the concept of a "private cage" merely a secure server room, or does it represent a deeper commitment to data protection in an increasingly volatile digital landscape? The answer, in short, is that a private cage transcends the basic function of physical security, offering a bespoke solution tailored to the nuanced needs of modern businesses, ultimately providing an enhanced level of control and peace of mind.
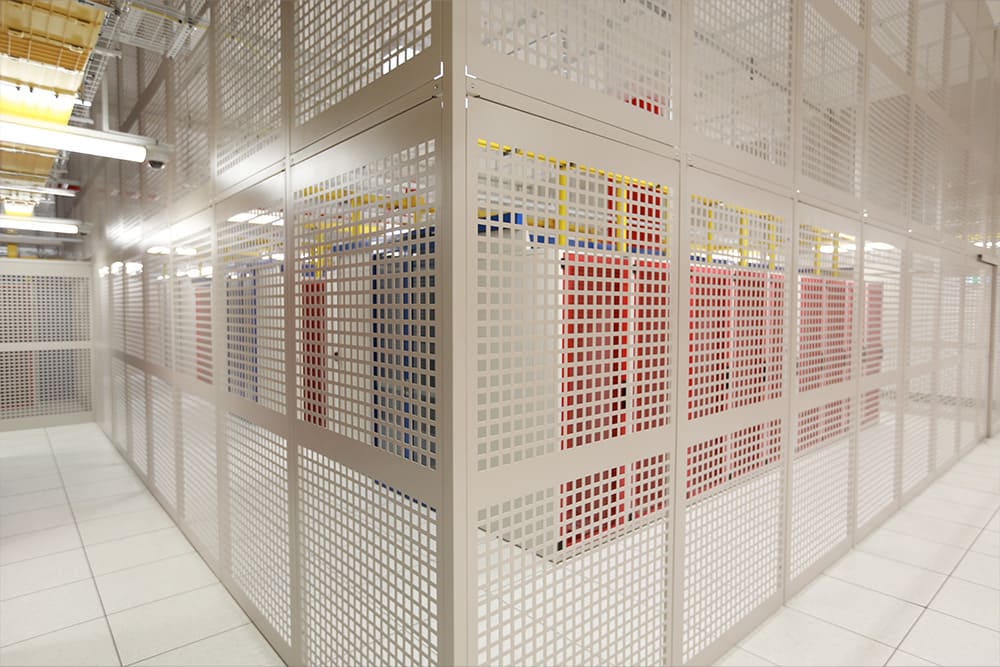
The term "private cage" itself is a bit of a misnomer. While it certainly denotes a physical, lockable space, its more accurately a specialized environment designed for housing and protecting critical IT infrastructure. These cages, often located within secure data centers, are custom-built to meet the specific requirements of individual clients. Unlike shared colocation environments, a private cage provides exclusive access, ensuring that only authorized personnel can physically interact with the contained servers and equipment.
The evolution of private cages is directly linked to the growing demands for data security and the increasing complexity of IT operations. As businesses generate and store ever-larger volumes of sensitive information, the risks associated with data breaches, cyberattacks, and physical security threats have become more pronounced. A private cage offers a robust defense against these threats, creating a controlled environment that mitigates risk and ensures business continuity. This approach is particularly crucial for industries dealing with stringent regulatory requirements, such as finance, healthcare, and government agencies. They must adhere to strict compliance standards like HIPAA, PCI DSS, and GDPR, which mandate the safeguarding of sensitive data.
- Fikfap Your Guide To Short Videos Entertainment Get Started
- Rhodes Family The Legacy Story Of Wrestlings Royalty
The concept of a private cage can be viewed through the lens of several key elements. The following table will highlight the key aspects of a typical private cage installation:
| Feature | Description |
|---|---|
| Physical Security | Individually lockable steel cages, often with biometric access controls and video surveillance, providing superior protection against unauthorized access. |
| Customization | Designed to specific requirements, including size, power density, cooling needs, and network connectivity, tailored to individual business needs. |
| Dedicated Resources | Exclusive access to power, cooling, and network infrastructure, ensuring optimal performance and eliminating the risks of resource contention. |
| Compliance | Meeting compliance requirements for various industries and regulations, offering a secure environment to manage sensitive data. |
| Scalability | Designed to support growth, with options to expand the cage space as needed, providing flexibility to adjust to changing IT needs. |
| Control | Provides the client with complete control over their IT infrastructure, with access limited to authorized personnel and secure configurations. |
For further information about data center security and private cages, visit Coresite.
The origins of the "private cage" concept can be traced to the early days of data centers. As businesses began to outsource their IT infrastructure, the need for secure and reliable hosting environments became apparent. The initial solutions were often shared colocation racks, where multiple clients would share the same physical space. However, as the demand for enhanced security and control grew, private cages emerged as a more sophisticated option. These early cages were relatively simple, often consisting of a fenced-off area within a data center. However, as technology advanced, the design and functionality of private cages evolved to meet the increasing demands of modern businesses.
- Stefan Thomass Bitcoin Nightmare Lost Password 240m At Risk
- Explore Voice Acting Games Comics Your Guide Finds
In the realm of cinematic narratives, the themes of confinement and control often intersect with the exploration of existential threats. Consider, for example, the film Edge of Tomorrow, where Major William Cage, played by Tom Cruise, finds himself trapped in a time loop while battling an alien invasion. While the film's focus is on combat and survival, it subtly underscores the psychological and physical limitations imposed by a recurring, confined reality. Much like a private cage, Cage's time loop represents a controlled environment, albeit one dictated by alien forces, where he must learn to adapt and strategize in order to break free from his perpetual cycle.
This thematic resonance extends to the concept of data protection. The data housed within a private cage can be seen as a valuable resource, much like Cage's ability to learn from his repeated experiences. Both require careful management and strategic deployment to ensure survival in the face of external threats. The private cage, in this analogy, becomes a sanctuary, shielding critical information from the chaotic realities of the digital world.
The landscape of colocation is diverse, and several options are available to businesses. Private cage colocation is often preferred by businesses that require enhanced security, compliance, and dedicated resources. Then there is private suite colocation, which offers a higher level of isolation, providing four hardened walls and a secure door to house equipment. Both options offer advantages over traditional shared colocation, where resources are pooled, and security is more generalized. When choosing between these colocation options, businesses must assess their specific needs, budget, and risk tolerance.
Let's delve deeper into the technical aspects of private cages. They are meticulously built to accommodate a wide array of IT equipment, ranging from servers and storage arrays to network switches and routers. The design incorporates several essential elements. First and foremost is the physical structure itselfa robust, lockable enclosure constructed from high-strength materials. These cages are often equipped with biometric access controls and round-the-clock video surveillance to ensure only authorized personnel can enter. Secondly, power infrastructure is critical. Private cages are provisioned with dedicated power feeds, often including redundant power supplies and uninterruptible power supplies (UPS) to guarantee continuous operation. Third, cooling systems are essential to dissipate heat generated by the IT equipment. This can range from standard air conditioning to more sophisticated methods, such as liquid cooling, depending on the power density of the equipment and client requirements. Finally, network connectivity is crucial. Private cages offer a variety of connection options, including copper and fiber optic cables, allowing clients to connect to a wide range of networks and service providers.
The process of implementing a private cage is a collaborative effort between the client and the data center provider. The first step is a comprehensive needs assessment, during which the client's IT infrastructure and business requirements are thoroughly evaluated. Based on this assessment, the data center provider designs a custom cage solution that meets the client's specific needs. This process involves determining the size and configuration of the cage, as well as the power, cooling, and network requirements. Following the design phase, the data center provider builds and installs the cage, ensuring it meets all relevant security and compliance standards. Finally, the client's equipment is deployed within the cage, and the data center provider provides ongoing support and maintenance.
In many ways, the appeal of a private cage extends beyond the mere provision of physical security. It's about establishing a strategic advantage. Consider businesses that deal with intellectual property, confidential client data, or regulated information. For them, the level of control and security offered by a private cage is essential. Furthermore, the ability to customize the cage to meet specific requirementswhether it's the installation of specialized cooling systems or the integration of advanced security measuresprovides a level of flexibility and responsiveness that is often lacking in shared environments. The design allows for scalability, enabling businesses to adjust their IT infrastructure as their needs evolve.
Let's move on to another narrative framework for considering private cages. The film Edge of Tomorrow features aliens called mimics, and the humans fighting them are thrust into a relentless battle for survival. This high-stakes environment provides a useful analogy for the risks faced by businesses today. Just as the soldiers in the film must adapt and learn from their experiences to defeat the mimics, businesses must proactively protect their data from a myriad of threats. In this setting, the private cage is an important asset; the fortified fortress in which valuable data is protected from intruders.
The evolution of data security has been rapid. In the early days of computing, security was a less critical concern, and protection was often limited to physical security measures, like locked rooms and limited access. As technology advanced and data became increasingly valuable, security threats grew in both sophistication and severity. This led to a proliferation of security solutions, including firewalls, intrusion detection systems, and encryption technologies. Today, data breaches are a frequent occurrence, resulting in significant financial losses, reputational damage, and legal liabilities. In this environment, a holistic approach to data security is essential, which includes physical security measures and advanced cybersecurity protocols.
The implementation of a private cage solution requires careful consideration of several key factors. One of the primary factors is the selection of a data center provider. Clients should choose a provider with a proven track record of providing reliable, secure, and compliant data center services. The provider should offer a range of amenities and services, including 24/7 support, remote hands-on services, and robust power and cooling infrastructure. Additionally, the data center should be located in a secure and accessible location, with redundant power feeds and network connections. Another critical factor is the design of the private cage itself. The cage should be customized to the client's specific requirements, with adequate space, power, cooling, and network connectivity. The cage should also comply with all relevant security and compliance standards.
The benefits of a private cage extend beyond just security and compliance. They can also provide significant cost savings. For businesses that require a significant amount of IT infrastructure, a private cage can be more cost-effective than building and maintaining their own data center. The data center provider handles the upfront investment, ongoing maintenance, and security costs, allowing businesses to focus on their core competencies. Furthermore, private cages offer increased operational efficiency. By outsourcing their data center operations, businesses can free up their IT staff to focus on strategic initiatives, such as developing new applications and improving customer service. Lastly, private cages provide enhanced scalability. As a business grows, it can easily expand its cage space and power resources to accommodate its increasing IT needs.
The use of private cages is not limited to a specific industry. They are used by businesses across a wide range of sectors, including finance, healthcare, government, and technology. Financial institutions use private cages to protect their sensitive financial data and ensure compliance with regulatory requirements. Healthcare organizations use private cages to safeguard patient data and comply with HIPAA regulations. Government agencies use private cages to store classified information and ensure the security of their IT infrastructure. Technology companies use private cages to host their servers and applications and to provide their customers with secure and reliable services.
The landscape of data security is constantly evolving, with new threats and vulnerabilities emerging all the time. To stay ahead of these threats, businesses must adopt a proactive and layered approach to data security. This involves implementing a range of security measures, including physical security, cybersecurity, and data encryption. Physical security is essential for protecting data from unauthorized access and physical damage. Cybersecurity measures, such as firewalls, intrusion detection systems, and vulnerability scanning, are essential for protecting data from cyberattacks. Data encryption is used to protect data from unauthorized access, even if the data is compromised. Regular security audits and penetration testing are crucial to identify and address vulnerabilities. By taking a proactive and layered approach to data security, businesses can protect their data and ensure business continuity.
Consider the perspective of General Brigham in Edge of Tomorrow. His main responsibility is to ensure the success of the war. He would appreciate the level of control and security that private cages offer. In a world constantly at war with mimics, data security would be a matter of life and death. Private cages, like the hardened defenses deployed in a warzone, act as a last line of defense, safeguarding valuable assets from external threats. It provides the critical infrastructure that allows the defense force to continue its fight.
The future of data security will be shaped by several key trends. One trend is the increasing use of artificial intelligence (AI) and machine learning (ML) for security. AI and ML can be used to automate security tasks, detect threats more effectively, and improve the overall security posture of an organization. Another trend is the growth of cloud computing. As more businesses migrate their data to the cloud, they will need to ensure that their data is secure. Cloud providers are investing heavily in security, but businesses must also take steps to protect their data in the cloud, such as encrypting their data and implementing robust access controls. Furthermore, the importance of data privacy is increasing. With the rise of data privacy regulations, such as GDPR and CCPA, businesses must be more diligent in protecting the privacy of their data. This includes implementing data privacy policies, encrypting sensitive data, and providing individuals with control over their personal data. Lastly, the threat landscape is constantly evolving. New cyberattacks and vulnerabilities emerge all the time, requiring businesses to stay vigilant and adapt their security strategies accordingly.
The concept of a private cage, therefore, is more than just a secure space. It is a strategic asset, a testament to a commitment to data security, and a reflection of a business's commitment to protecting its most valuable assets. Whether battling mimics or navigating the complexities of the digital age, the right precautions and a well-secured private cage can make all the difference.


Detail Author:
- Name : Francesco Gorczany
- Username : francisca64
- Email : lorena.metz@hotmail.com
- Birthdate : 1994-01-31
- Address : 18573 Farrell Parks Kennediville, TX 25381-7303
- Phone : 1-970-617-3735
- Company : Green Ltd
- Job : Mental Health Counselor
- Bio : Qui rerum iste minima porro distinctio in in. Vero et cupiditate et soluta fugiat provident dignissimos. Itaque enim labore eaque optio. Et et alias asperiores esse illum voluptate minus.
Socials
tiktok:
- url : https://tiktok.com/@klabadie
- username : klabadie
- bio : Sint quisquam debitis dolorem. Alias sit eum id deserunt consequatur quisquam.
- followers : 809
- following : 698
instagram:
- url : https://instagram.com/kurtlabadie
- username : kurtlabadie
- bio : Veritatis et maiores dolorem eos at. Ullam aspernatur dolorum eos deserunt esse in impedit.
- followers : 4926
- following : 357