Secure IoT Access: How To SSH Into Devices On Windows 10 & Beyond
Have you ever pondered the vulnerabilities lurking within the seemingly innocuous realm of your smart home or office? The pervasive integration of Internet of Things (IoT) devices has ushered in an era of unparalleled convenience, but it has also amplified the risk of cyberattacks. Understanding how to fortify these digital gateways is no longer a luxury; it's a necessity.
The digital landscape is riddled with threats, from sophisticated malware to brute-force attacks. Common shortcuts and insecure backend methods employed by developers can inadvertently create backdoors, inviting cybercriminals to waltz into your network. The implications are vast, ranging from data breaches and identity theft to complete system compromise. The good news is that there are effective strategies for safeguarding your connected devices, and one of the most robust is Secure Shell (SSH).
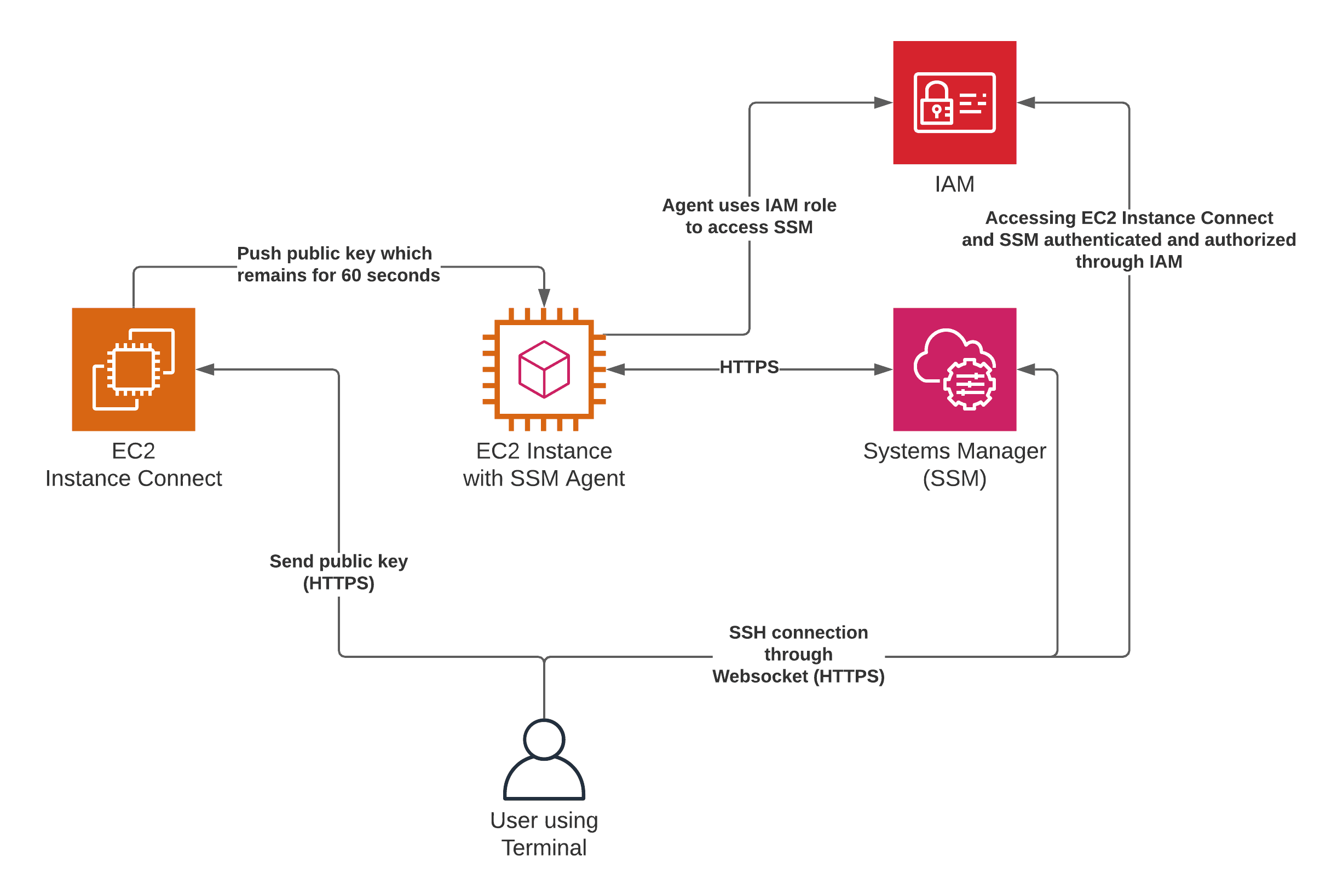
SSH, a cryptographic network protocol, provides a secure channel for remote access to devices. It's the digital equivalent of a highly secure vault, ensuring that only authorized individuals can access sensitive information. With SSH, remote access to IoT devices becomes safe, easy to deploy, and remarkably dependable.
This guide delves into the specifics of harnessing the SSH protocol for securely supervising IoT networks, protecting your data, and ensuring the safety of individuals. We'll walk you through every step, ensuring that whether you're a novice or an experienced user, you can confidently configure and utilize SSH on your IoT devices.
In the contemporary interconnected world, IoT devices have become ubiquitous, seamlessly integrating into our daily lives. From smart thermostats that regulate our home environments to security cameras that monitor our surroundings, the presence of these devices is undeniable. Yet, their very ubiquity poses a unique set of security challenges.
The underlying issue is that many IoT devices, designed for simplicity and ease of use, often lack robust security measures. This vulnerability creates appealing targets for hackers. Common exploits include default passwords, unencrypted communication channels, and outdated firmware. These weaknesses provide entry points for malicious actors to gain unauthorized access, launch attacks, or steal sensitive data.
- Marla Maples Life After Donald Trump Whats She Up To
- Find Jamelizzz Linktree Onlyfans More Your Guide
Consider the hypothetical scenario of a smart home compromised by a cyberattack. An attacker could remotely control the locks on doors, disable the security system, or access private conversations through smart assistants. Similarly, in a corporate setting, attackers might gain access to confidential company data, disrupt operations, or even hold systems for ransom.
That's where Secure Shell (SSH) becomes a vital tool. It functions much like a superhero in this complex, ever-evolving landscape of technology and internet connectivity, offering a powerful means of safeguarding your IoT devices.
The primary function of SSH is to establish a secure, encrypted connection between a user's computer and a remote device. This is a huge improvement over other older, unsecure methods.
When considering security, SSH is a very significant improvement. With SSH, all communication is encrypted. This means that any data transmitted between your computer and the IoT device, including usernames, passwords, and any commands or data exchanged, is unreadable to anyone eavesdropping on the network. This end-to-end encryption is crucial in preventing unauthorized access and data breaches.
SSH also provides a robust authentication mechanism. Users must provide valid credentialstypically a username and password, or, more securely, a cryptographic keybefore they can access the device. This added layer of security makes it extremely difficult for unauthorized individuals to log in, even if they manage to intercept the connection.
This guide is designed to give you all the knowledge and information needed to safeguard your IoT devices. In this guide, we will address the following points:
- Understanding the fundamentals of SSH.
- Configuring your Windows 10 machine for SSH.
- Setting up your IoT device for remote access.
- Establishing a secure connection.
- Managing and troubleshooting connected devices.
- Implementing security best practices.
By enabling SSH on Windows 10, configuring your IoT device, and setting up your network for remote access, you can effectively manage your connected devices from anywhere. Implementing security measures and following best practices will help you maintain a secure and reliable setup.
Openssh server is available as an optional feature in all new versions of windows starting with windows 10 (build 1809) and windows server 2019. The openssh server feature can be installed on windows 10 and 11 via the settings app.
More importantly, this also means port scanners or hackers from the internet cannot access your iot device ssh server port. This is an alternate method for remotely connecting to your iot devices ssh server using the socketxp solution.
Connecting to an IoT device via SSH on Windows 10 is a straightforward process. You'll need an SSH client like PuTTY, the IP address of your IoT device, and the login credentials. Simply install PuTTY, configure it with your devices details, and establish the connection. In fact, it is a powerful way to manage remote devices securely.
Connecting to an IoT device via SSH on Windows 10 is a powerful way to manage remote devices securely. Whether you're a beginner or an advanced user, this guide will walk you through every step of the process, ensuring you can confidently set up and use SSH on your IoT devices. Learn how to securely SSH into an IoT device and access its functionality and settings.
You'll need to set up an SSH client on your Windows 10 machine, configure port forwarding on your router, and ensure your IoT device is accessible. By enabling SSH on Windows 10, configuring your IoT device, and setting up your network for remote access, you can efficiently manage your connected devices from anywhere.
This article will teach you everything there is to know about SSH and how it protects our internet of things devices. From understanding the basics of SSH to configuring your IoT device for remote access, well cover everything you need to know.
Just getting started with Windows 10 IoT Core on Raspberry Pi 3. Shell or PowerShell when booting into Windows on a Pi. Connect the device via PowerShell or SSH.
Once SSH port forwarding is established, you can do the following based on the device type: You can run adb commands to interact with the device or run any other scripts or applications from your machine that utilizes adb commands. You can SSH to the device to interact with it.
Before you can SSH into your IoT device, you need to make sure SSH is ready to roll on your Windows 10 machine. Dont worryits easier than you think. In this guide, well dive deep into how you can SSH into an IoT device using Windows 10. Trust me, its easier than it sounds.
Once authenticated, youre connected through a secure channel, ensuring only the right people can access your device.
Windows 10 IoT (on Raspberry Pi 2) has the WinUSB driver (found in c:\\windows\\system32\\winusb.dll) but I can't get Windows 10 IoT to use this driver for my device. When the RP2 gets back up your device should be listed under connected devices on the default startup app, and you should now be able to use functionality from windows.devices.usb to communicate with the USB device.
Implementing SSH on your Windows 10 machine involves several steps.
- Enabling the OpenSSH Server Feature:
Go to Settings > Apps > Optional features > Add a feature. Search for and install "OpenSSH Server."
- Configuring the Windows Firewall:
Ensure that the Windows Firewall allows incoming connections on port 22 (the default SSH port). You can add a rule to the firewall settings to allow SSH traffic.
- Checking the SSH Service Status:
Verify that the OpenSSH SSH Server service is running. You can check this in the Services app (search for "Services" in the Windows search bar) and ensure the service is set to start automatically.
- Finding Your Windows 10 Machine's IP Address:
You'll need your machine's IP address to connect to it via SSH. You can find this in the network settings (Settings > Network & Internet) or by using the `ipconfig` command in the Command Prompt.
Setting up the IoT Device
- Enable SSH on the IoT Device:
The process for enabling SSH will vary depending on the specific device and operating system. Typically, you'll need to access the device's settings or configuration interface and find the SSH option. Make sure SSH is enabled and, if applicable, configure the SSH port (usually 22).
- Set Up a User Account:
You'll need to create a user account on the IoT device with appropriate privileges for remote access. Ensure the user has a strong password or is configured for SSH key-based authentication.
- Find the IoT Device's IP Address:
Determine the IP address of your IoT device. This is crucial for connecting to it. You can usually find this information in the device's network settings or by checking your router's connected devices list.
Establishing a Secure Connection:
- Choosing an SSH Client:
Select an SSH client for your Windows 10 machine. PuTTY is a popular, free option. Other choices include OpenSSH (which you can use from the Command Prompt or PowerShell), or specialized SSH clients available on the market.
- Configuring the SSH Client:
Open your chosen SSH client and enter the following information: The IP address of your IoT device, The SSH port (usually 22), and The username and password you created on the IoT device.
- Connecting:
Click "Connect" in your SSH client. If everything is configured correctly, you will be prompted to enter your password. Upon successful authentication, you'll gain access to the command-line interface of your IoT device. You're now connected via a secure SSH tunnel.
Maintaining a Secure Setup
- Regular Updates:
Regularly update your IoT devices operating system (OS) and SSH software to patch any known security vulnerabilities. This includes installing security updates and patches for the OS and SSH software as they become available.
- Strong Passwords and Key-Based Authentication:
Always use strong, unique passwords for all user accounts on your IoT devices. Whenever possible, implement SSH key-based authentication, which is significantly more secure than password-based authentication. This involves generating a cryptographic key pair (a private key and a public key) and using the public key to authenticate you.
- Firewall and Network Segmentation:
Utilize a firewall to restrict network traffic to your IoT devices. Segment your network to isolate your IoT devices from other devices, further reducing the risk of a security breach spreading across your network.
- Monitoring and Auditing:
Implement monitoring and auditing tools to track SSH connections and system logs on your IoT devices. This allows you to detect suspicious activity and identify potential security threats promptly.
Troubleshooting Common Issues:
- Connection Refused:
If you receive a "connection refused" error, double-check the IP address, port number, and SSH service status on your IoT device. Ensure the Windows Firewall is not blocking incoming SSH connections.
- Authentication Failures:
If you encounter authentication failures, carefully verify your username and password or SSH key configuration. Ensure that the Caps Lock key is not accidentally enabled and that the user account has the necessary permissions.
- Port Forwarding Problems:
If you're accessing your IoT device from outside your local network, confirm that port forwarding is correctly configured on your router. Make sure the router is forwarding traffic on the correct port (usually 22) to the IP address of your IoT device.
In summary, SSH is an essential tool for securing IoT devices on Windows 10. By implementing the steps outlined in this guideenabling SSH, configuring devices, setting up your network, and following security best practicesyou can significantly enhance the security of your connected devices. Remember to stay vigilant, regularly update your systems, and employ strong security measures to protect your data and privacy in the rapidly evolving world of IoT.


Detail Author:
- Name : Hilbert Bednar
- Username : ahmed.bartell
- Email : vdamore@gmail.com
- Birthdate : 2004-11-24
- Address : 1405 Farrell Stream Winnifredchester, IN 36712-8520
- Phone : 1-732-840-1085
- Company : Buckridge, Moore and Flatley
- Job : Forming Machine Operator
- Bio : Veritatis ipsam sit qui deleniti. Nulla consectetur fugiat animi culpa maiores itaque. Tempore maxime ea aut voluptatum voluptas. Repellendus qui temporibus debitis quia facilis amet qui occaecati.
Socials
tiktok:
- url : https://tiktok.com/@hulda_schmitt
- username : hulda_schmitt
- bio : Itaque optio natus architecto cupiditate exercitationem sint.
- followers : 186
- following : 1129
twitter:
- url : https://twitter.com/hulda_real
- username : hulda_real
- bio : Iure quod molestiae voluptatem veritatis. Sint quia architecto qui consequuntur assumenda tenetur impedit. Autem omnis ullam dolorem debitis vitae vel.
- followers : 1366
- following : 753
instagram:
- url : https://instagram.com/hulda_schmitt
- username : hulda_schmitt
- bio : Consectetur aliquid velit nisi fugit. Molestiae cum non expedita dicta provident.
- followers : 3944
- following : 75
linkedin:
- url : https://linkedin.com/in/schmitth
- username : schmitth
- bio : Vitae rerum voluptatem quidem ut qui unde.
- followers : 748
- following : 2118