Secure IoT Access: SSH Tunneling & Reverse Proxy Guide
Can you imagine a world where your devices, scattered across locations, are always within your secure reach? The answer lies in the powerful and often underutilized technology of SSH reverse tunneling, offering a robust solution for remote access, control, and secure communication within the ever-expanding realm of the Internet of Things (IoT).
In today's interconnected world, the ability to remotely manage and troubleshoot devices is no longer a luxury, but a necessity. Whether you're a hobbyist tinkering with a Raspberry Pi, a hacker exploring the possibilities of embedded systems, or a seasoned professional managing a fleet of IoT devices, the challenges of remote access are ever-present. Firewalls, Network Address Translation (NAT) routers, and the inherent complexities of securing communication channels often stand in the way, making remote management a costly and time-consuming endeavor.
| Aspect | Details |
|---|---|
| Definition | SSH reverse proxy tunneling is a technique that establishes a secure, encrypted connection from a remote device or server back to a local machine, allowing access to local services and devices, even when behind firewalls or NAT. |
| Core Functionality | Creates an encrypted SSH connection in the reverse direction, essentially acting as a secure "pipeline" for data transfer. |
| Common Use Cases | Remote IoT control, database access, gaming, accessing internal services, and secure remote management of devices behind firewalls. |
| Security Benefits | Encryption of all data passing through the tunnel, providing a secure channel for communication and protecting against eavesdropping and data breaches. |
| Components Involved | Local machine (e.g., your computer), remote server (e.g., an SSH server), and the SSH client/server software. |
| Alternatives | VPNs, which establish a secure network connection, and tools like Pinggy, that simplify the tunneling process. |
| Advantages Over Traditional Methods | Overcomes challenges posed by firewalls and NAT, providing secure remote access without the need to open ports. |
| Practical Applications | Managing Raspberry Pi projects remotely, accessing internal databases from outside the network, and securely controlling IoT devices. |
| Best Practices | Use strong, unique passwords; choose reliable tunneling services; implement firewalls; and regularly update security software. |
| Reference Link | Example: Comprehensive Guide to SSH Reverse Tunneling (Please replace with an actual reliable source.) |
The concept of SSH reverse tunneling, however, offers a solution to these issues. It's a secure method of establishing remote access to your IoT devices or any machine (servers, laptops, or PCs) located behind a NAT router or firewall. Think of it as a virtual, encrypted pipeline, allowing you to connect to your local services and devices from anywhere, even when they're shielded from direct external access.
- Baby Alien Fan Bus Videos Watch Explore The Viral Trend
- Cho Seung Woo Relationship Status Personal Life Explored
At its core, SSH reverse tunneling works by creating an encrypted SSH connection in the opposite direction from the norm. Instead of connecting to a remote server from your local machine, a reverse tunnel connects from the remote device to your local machine. This reverses the usual direction, hence the name. This seemingly simple technique unlocks a world of possibilities for secure remote access, overcoming common obstacles like firewalls and NAT routers.
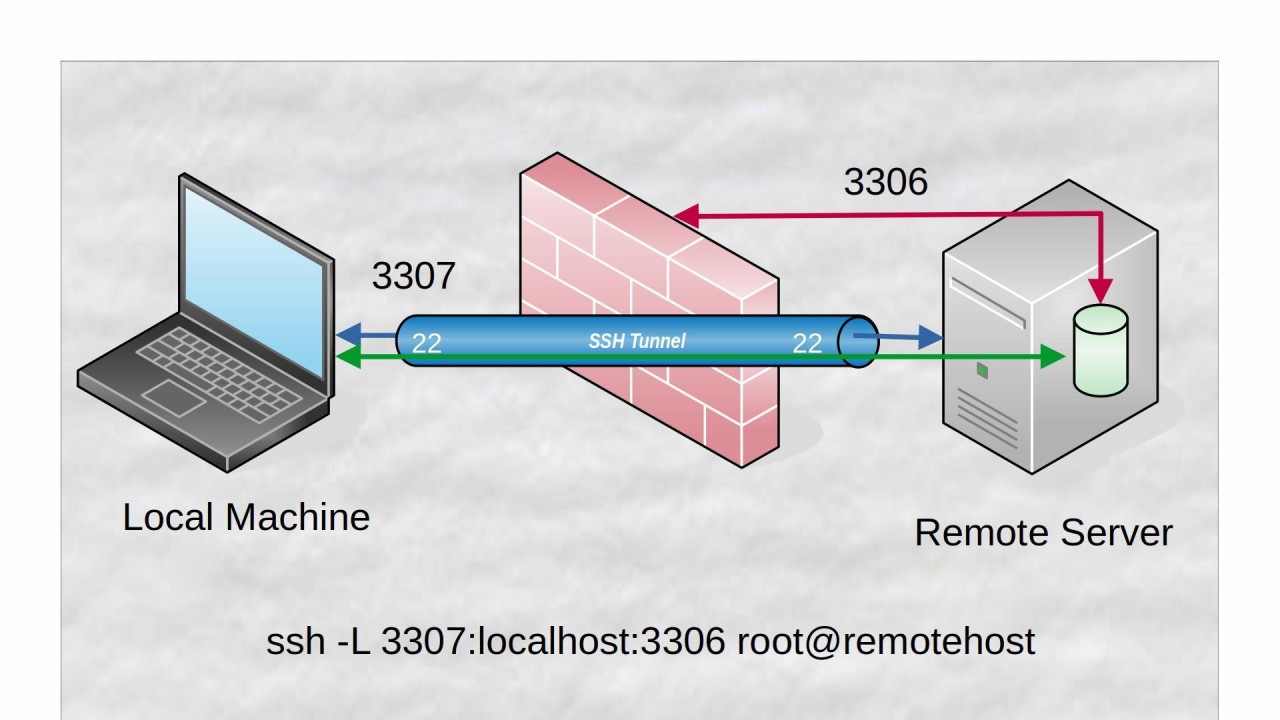
The mechanics are fairly straightforward. The remote device, acting as the SSH client, initiates a connection to an SSH server that you control (which can be a server on the internet or a machine in your network with a public IP address). This establishes a secure tunnel. Once the tunnel is established, any traffic directed to a specific port on the SSH server is then forwarded through the tunnel to a corresponding port on your local machine. This means you can access local services as if you were directly connected to the remote network, even if the device is behind a firewall.
This is particularly useful for the Internet of Things (IoT), where devices are often deployed in remote locations or behind restrictive network setups. With SSH reverse tunneling, you can securely manage and monitor these devices, access their internal services, and perform tasks like software updates and troubleshooting, all without needing to open ports or configure complex firewall rules.
Lets delve deeper into the specifics. You can utilize a quick setup method to rotate access tokens and SSH into the remote device directly within your browser. To employ this method, it is crucial to have established an IoT thing within the AWS IoT registry. Each service, undoubtedly, presents its own set of features and limitations, but leveraging your own server offers greater control and flexibility in the setup process.
Consider the example of configuring an SSH tunnel for a Raspberry Pi. This setup allows for remote access, enabling tasks such as controlling the Pi, accessing files, or running commands. Similarly, SSH remote IoT examples provide a secure and reliable way to manage IoT devices. By adhering to established best practices and implementing strong security measures, you can ensure your IoT communications remain private and protected.
SSH tunneling is the very foundation of IoT SSH over SSH examples. Envision it as a virtual pipeline, linking your local machine to a remote server. This pipeline guarantees that all data transmitted through it is both encrypted and secure. This article serves as a comprehensive guide to SSH reverse tunneling, detailing its role in securing access to local services from distant locations, even when behind firewalls or NATs.
It covers common applications, such as remote IoT control, database access, and gaming, while emphasizing security best practices and exploring alternatives, like VPNs and Pinggy. Pinggy is a helpful tool that simplifies the tunneling process. Reverse SSH tunneling is a technique utilized to establish a secure connection from a remote server or an IoT device back to a local machine. At its core, it involves establishing an encrypted SSH connection in the reverse direction of the norm.
The device proxy is a crucial element, taking on the role of a client by setting up a connection to the SSH daemon on the IoT device. Both proxy applications efficiently tunnel traffic between local instances and the IoT hub streaming endpoint. In simpler terms, this tunneling can be seen as a copying process between two streams, as demonstrated in the example of the device proxy. Another approach to remotely connecting to your IoT devices SSH server involves the SocketXP solution.
With the AWS IoT managed tunnel, you can seamlessly open the necessary SSH connection for your device. Examples of SSH in IoT applications are numerous. Secure Shell (SSH) plays a significant role in numerous Internet of Things (IoT) applications, facilitating secure remote access, management, and communication between IoT devices and their controlling systems. The state of the tunnel is meticulously reported in the connection logging section within the UI, a feature that proves invaluable in diagnosing connectivity problems.
To configure a tunnel, specific information is essential: the host and port of the SSH server, formatted as SSH://:. For instance, in a specific configuration, the tunnel is forwarded from remoteserver to the web server running on 10.10.10.10. The web server will then recognize remoteserver as the source of web requests. Clicking "connect" and entering your VNC password grants instant remote desktop access to your IoT device.
It is essential to follow best practices and security tips. Always use strong, unique passwords. Opt for reliable tunneling services to encrypt remote sessions securely. Another measure involves utilizing firewalls to protect and secure access to IoT devices. It can be difficult to access and manage devices deployed remotely, behind firewalls that block all incoming traffic. Troubleshooting devices might necessitate sending technicians on-site to connect to those devices. This can increase the complexity and cost of device management.
To delete an individual or multiple tunnels within the AWS IoT console, navigate to the tunnels hub. Choose the tunnels you wish to remove, then select the "delete tunnel" option. Furthermore, to eliminate a tunnel using the AWS IoT API reference, you can utilize the closetunnel API operation. To avoid any ongoing charges, it is advisable to delete any infrastructure created for testing, such as IoT things or EC2 instances.
Another useful aspect of this technique is to understand how the SSH reverse proxy tunnel functions. This method enables a remote server to access services running on a local machine through an encrypted SSH connection. This proves beneficial when exposing a local service to a remote machine without opening ports on the local network. This allows access to the device's SSH server using a different method involving the SocketXP solution.
Examples of SSH in IoT applications abound, with secure shell (SSH) playing a significant role in various IoT applications. This enables secure remote access, management, and communication between IoT devices and their controlling systems.
In essence, SSH reverse tunneling provides a powerful and secure means of remote access, vital for the modern interconnected world. By understanding its principles and best practices, you can unlock the full potential of your IoT devices and ensure secure remote management.


Detail Author:
- Name : Missouri Brown
- Username : urath
- Email : jacobson.laurence@hotmail.com
- Birthdate : 2006-04-02
- Address : 66024 Daphnee Freeway Hermanfort, CO 72952
- Phone : +1-561-588-6022
- Company : Wilkinson Ltd
- Job : Recreational Therapist
- Bio : Et vero omnis occaecati magnam vitae saepe. Omnis hic a autem quam sit. Eos sed labore dolor doloremque. Odit ea dolor necessitatibus saepe in et.
Socials
linkedin:
- url : https://linkedin.com/in/tyreekheathcote
- username : tyreekheathcote
- bio : Tenetur et minus facilis ad iure.
- followers : 4520
- following : 1000
facebook:
- url : https://facebook.com/heathcotet
- username : heathcotet
- bio : Ex dolorem reprehenderit et nam voluptatem aspernatur dolorum.
- followers : 1249
- following : 2220