AWS SSH Tunneling: Securely Access Your Resources & More!
Is it possible to securely access and manage your remote devices without exposing them to the public internet? The answer is a resounding yes, thanks to the power of Secure Shell (SSH) tunneling and its various implementations, particularly within the Amazon Web Services (AWS) ecosystem.
The need for secure remote access to devices and servers is a cornerstone of modern IT infrastructure. Firewalls, while essential for security, often complicate this access, blocking inbound traffic and making direct connections impossible. This is where SSH tunneling comes to the rescue, providing a secure pathway for communication. By creating an encrypted tunnel, you can bypass firewall restrictions and establish a secure connection to your target device.
| Feature | Details |
|---|---|
| Technology | SSH (Secure Shell) Tunneling, Secure Copy Protocol (SCP), AWS Systems Manager Session Manager, AWS IoT Secure Tunneling |
| Purpose | Securely access and manage remote devices, bypass firewall restrictions, transfer files, and establish bidirectional communication. |
| Key Components | Client (your local machine), Server (remote device), SSH client, AWS Systems Manager Session Manager, AWS IoT console/API |
| Benefits | Enhanced security through encryption, no need for public IP addresses, firewall-friendly, bidirectional communication, file transfer capabilities, and streamlined access to resources behind firewalls. |
| Use Cases | Connecting to EC2 instances, accessing RDS databases, managing IoT devices, remote server administration, secure file transfer, accessing private networks. |
| Tools | AWS CLI, SSH clients (e.g., OpenSSH), utilities for creating tunnels (e.g., Session Manager). |
| AWS Services | Amazon EC2, Amazon RDS, AWS Systems Manager, AWS IoT Core. |
| Considerations | Network configuration, Security group settings, proper user permissions, authentication. |
| Reference | AWS Blog - SSH related articles |
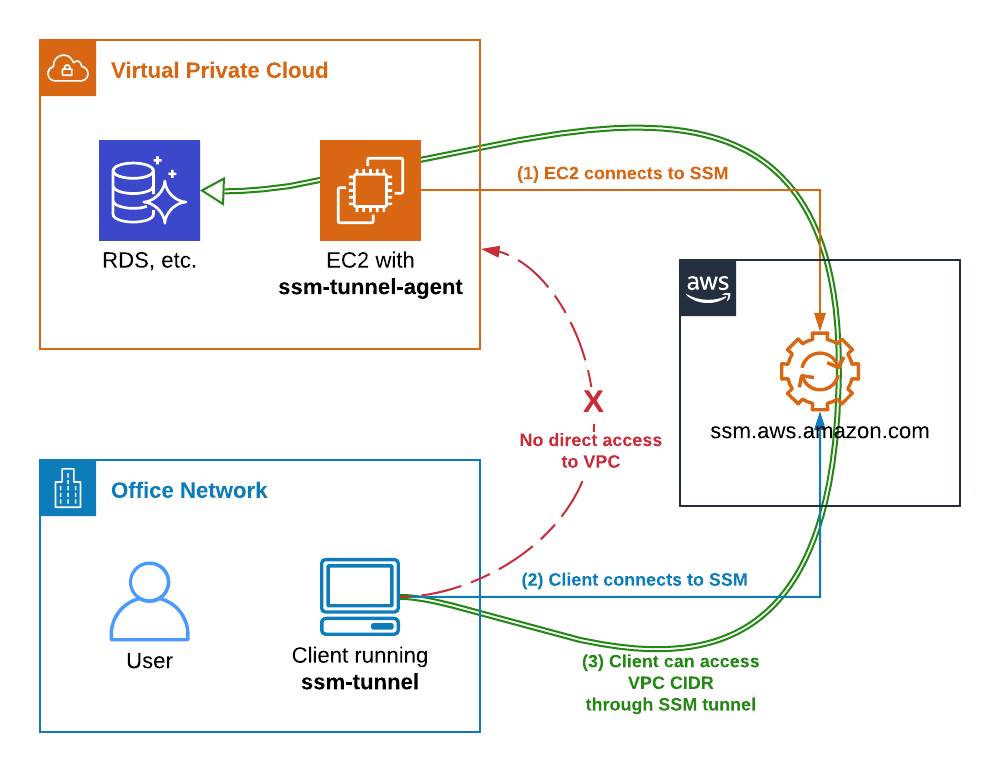
Several methods exist to achieve SSH tunneling. One prominent approach leverages AWS Systems Manager Session Manager. This allows users within your AWS account to employ the AWS Command Line Interface (CLI) to initiate SSH connections to managed nodes. This method is particularly appealing because it does not require exposing bastion servers publicly, enhancing security by routing traffic through a secured AWS Systems Manager session. Furthermore, Session Manager enables secure file transfer using the Secure Copy Protocol (SCP) between your local machine and managed nodes.
- Explore Latest Telugu Movies More Movierulz Updates
- Steve Harvey Death Hoax Latest News Updates Whats Trending
Another robust solution is AWS IoT Secure Tunneling, ideally suited for establishing bidirectional communication with remote devices that reside behind firewalls. It does not necessitate modifications to your existing inbound firewall rules, thereby maintaining the same level of security. AWS IoT Secure Tunneling can be managed via the AWS IoT console or the AWS IoT API reference API, providing flexibility in managing tunnel creation and deletion. Tunnels can be created from the tunnels hub or the details page of an IoT thing, offering choices in the setup process.
The core concept behind SSH tunneling, or SSH port forwarding, involves transporting data over an encrypted SSH connection. SSH tunnels facilitate the forwarding of connections made to a local port to a remote machine via a secure channel. To create an SSH tunnel, you can leverage Session Manager, which opens a secure pathway to remote devices, even those behind firewalls that block inbound traffic. This is frequently employed for connecting to EC2/RDS machines. An SSH tunnel acts as a secure link, mapping a local port on your machine to a remote IP address/port combination, thereby enabling access to otherwise inaccessible resources.
Consider a scenario where you need to connect to a private database residing on AWS from your local computer. You can establish a secure SSH connection between your local machine and an Amazon EC2 instance using an SSH client. Once connected, you can request a "tunnel" or "forwarded connection" to facilitate access to the database. This is often achieved using local port forwarding, which allows you to connect to the local web server on the primary node by creating an SSH tunnel.
- Miu Shiramine The Rising Star In Japanese Av Get To Know Her
- Riley Mae Lewis Leak What Happened Latest Updates
AWS provides various tutorials and examples to demonstrate the practical application of SSH tunneling. You'll find guidance on remotely accessing a device behind a firewall. Because you can't directly initiate an SSH session due to the firewall's restrictions on inbound traffic, the tutorials illustrate how to open a tunnel and utilize it to start an SSH session to a remote device, also known as port forwarding.
To create an SSH tunnel using Session Manager, several prerequisites must be met. Firstly, you need an AWS account and an EC2 instance running within your AWS environment. Configure your EC2 instance to allow SSH access and ensure that the necessary security groups are configured to permit SSH traffic. You will also need to install the AWS CLI on your local machine and configure it with your AWS credentials.
Once these prerequisites are in place, you can create the SSH tunnel using the AWS CLI and Session Manager. You'll use the `session-manager-plugin` to establish the secure connection. The general command structure involves specifying the instance ID of the EC2 instance you wish to connect to, along with the necessary parameters to define the local port forwarding.
When utilizing AWS IoT Secure Tunneling, you can establish bidirectional communication to remote devices, ensuring that the connection is secure. To do so, start by creating a tunnel through the AWS IoT console. You can choose between a quick setup or a manual setup. Once the tunnel is established, you'll need to configure your client device and the remote device to use the tunnel. This configuration involves specifying the tunnel endpoint and setting up the necessary authentication mechanisms. To delete a tunnel, use the AWS IoT console or the `CloseTunnel` API.
To further exemplify, let's explore the process of establishing an SSH tunnel using a command-line interface. Start by enabling the SSH tunnel and keeping it active for as long as you need it. Terminate the tunnel when you're finished by pressing `Ctrl + C`. This operation will initiate a new session using AWS Systems Manager / Session Manager.
In the context of connecting to RDS databases, SSH tunneling becomes crucial. After youve correctly configured your SSH client and verified SSH access to your instance, you will need to create an SSH tunnel. To establish an SSH tunnel for RDS connectivity, start by launching an Amazon RDS database. Next, configure the SSH tunnel within your preferred database client (like pgAdmin or Sequel Pro). Specify the local port for forwarding, and use `localhost (127.0.0.1)` for the host, along with your RDS username and password for authentication. Configure pgAdmin for SSH tunneling by selecting "Standard TCP/IP over SSH" for the connection method, enter the public IP address of your EC2 instance as the SSH hostname, and input the default SSH username for your EC2 instance, also, specify the .pem key file used for connection.
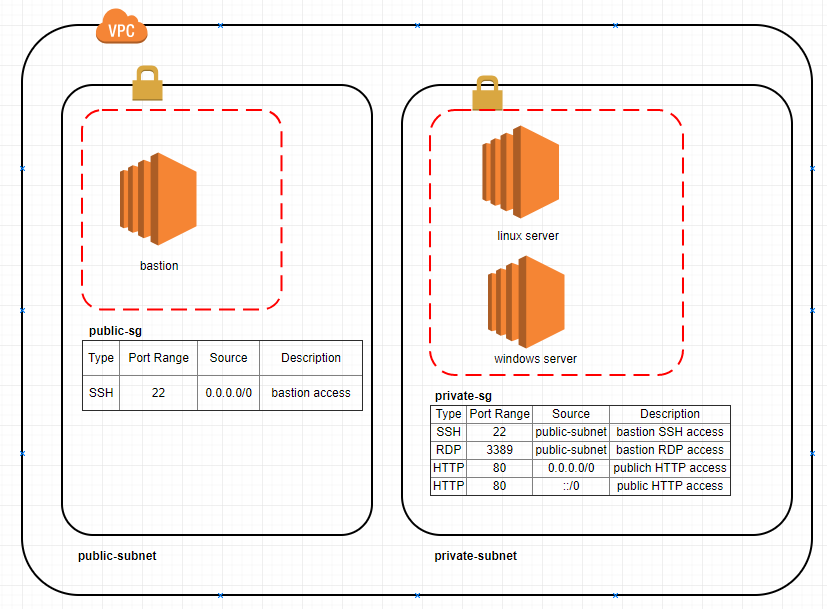
For the Linux/macOS environment, the security group settings are pivotal; they need to permit the IP address of your machine from which you will connect. You then execute a specific command from your Linux/macOS machine to establish the tunnel. Essentially, an SSH tunnel receives the request from your local IP address and forwards it to the bastion host, hence the importance of TCP forwarding for the bastion host. This configuration enables you to securely access the RDS database through the SSH tunnel.
The integration of SSH tunneling is a versatile solution that secures and simplifies remote access to your infrastructure, from connecting to EC2 instances and RDS databases to managing IoT devices. This approach ensures that your resources remain protected by encrypted connections, even when they are situated behind firewalls. The flexibility offered by solutions like AWS Systems Manager and AWS IoT Secure Tunneling underscores the significance of secure and efficient remote access in modern cloud environments.

Detail Author:
- Name : Prof. Isabelle Tillman MD
- Username : bethany.greenholt
- Email : considine.jordan@fadel.com
- Birthdate : 1972-01-05
- Address : 189 Alvina Path Port Sven, AL 41053-4181
- Phone : 253-633-0359
- Company : Ryan-Abshire
- Job : Motion Picture Projectionist
- Bio : Sapiente nam amet eos officia. Reprehenderit repellat unde sit repellendus aperiam molestias dolor. Sed asperiores est similique placeat animi nihil exercitationem.
Socials
linkedin:
- url : https://linkedin.com/in/grimesf
- username : grimesf
- bio : Libero autem adipisci nostrum minima qui qui.
- followers : 2967
- following : 394
tiktok:
- url : https://tiktok.com/@frankie_dev
- username : frankie_dev
- bio : Labore adipisci voluptatem dolores consequuntur beatae ratione.
- followers : 4813
- following : 1561
instagram:
- url : https://instagram.com/frankie.grimes
- username : frankie.grimes
- bio : Error aut pariatur exercitationem exercitationem quia. Ipsa voluptatibus illo ad eius.
- followers : 4161
- following : 804