AWS IoT Secure Tunneling: Remote Device Access Simplified
Isn't it time we untangled the complexities of remotely accessing your Internet of Things (IoT) devices? AWS IoT Secure Tunneling offers a streamlined, secure path for bidirectional communication, eliminating the need for cumbersome firewall adjustments and empowering you to manage your IoT devices from anywhere.
In today's rapidly evolving technological landscape, the need for secure, reliable remote access to IoT devices is paramount. Whether you're a seasoned developer or just starting to explore the world of connected devices, the ability to securely connect to your devices, diagnose issues, and perform maintenance tasks remotely is invaluable. AWS IoT Secure Tunneling emerges as a powerful solution, designed to simplify this process and enhance your overall IoT management capabilities.
This technology is a feature of AWS IoT Device Management, providing a secure, managed connection that bypasses the traditional barriers often associated with remote access. This means you can troubleshoot device anomalies, perform software updates, and even access your web server application running on a remote device, all without the need for updates to your existing inbound firewall rules. This maintains the same security level provided by firewall rules at a remote site.
- Diddy Scandal Shocking Celebrity List Allegations Unveiled
- Dive Into Retro Bowl Unblocked Cheats College Fun
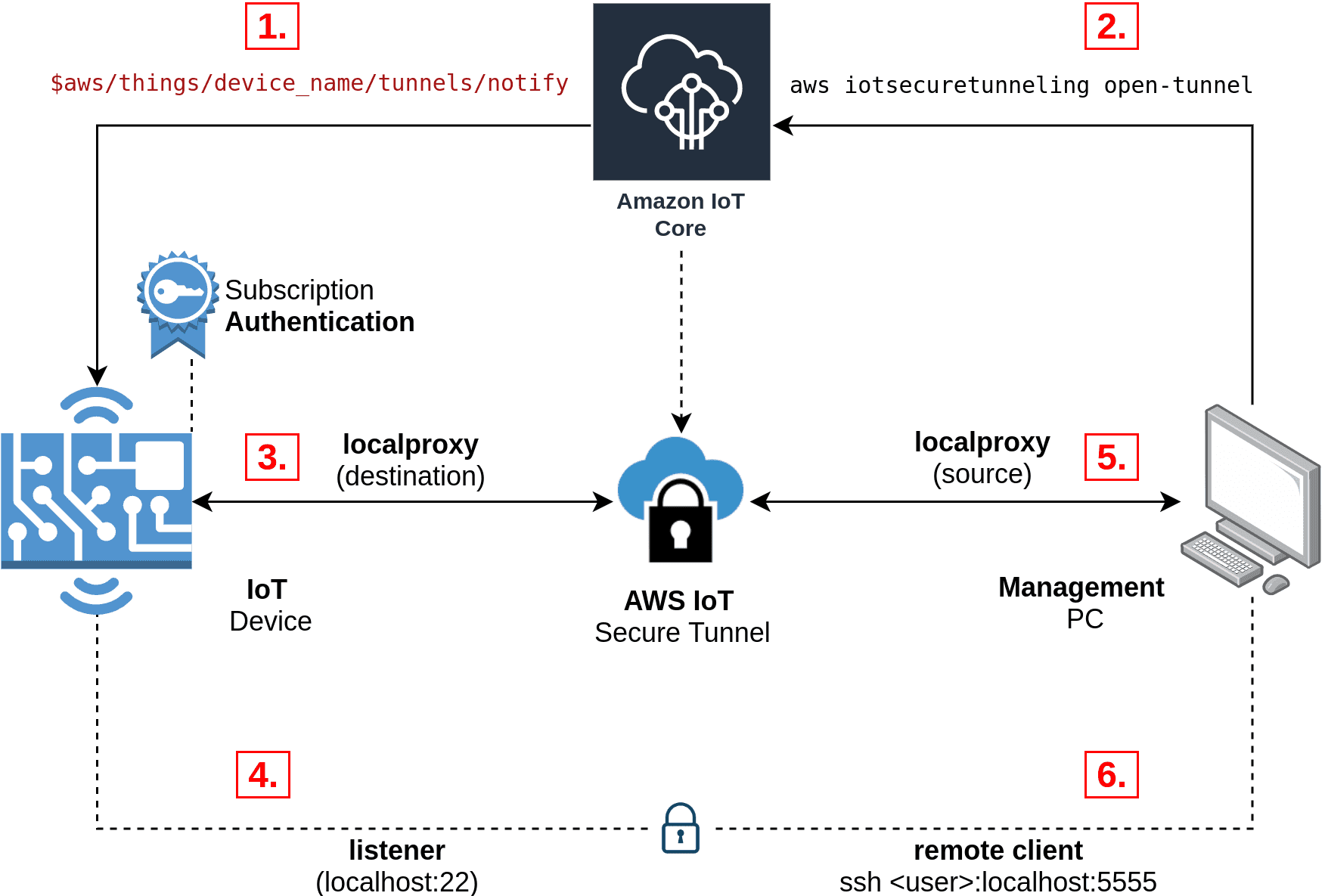
Let's delve deeper into the mechanics of AWS IoT Secure Tunneling. At its core, the service creates a secure, bidirectional communication channel between your local machine (the source) and your remote IoT device (the destination). This tunnel is managed by AWS IoT, ensuring that the connection is secure and reliable. The process generally involves the following steps:
- Tunnel Creation: You initiate the process by creating a tunnel using the AWS IoT console or the AWS IoT API. This action generates a unique tunnel identifier and establishes the foundational infrastructure for communication.
- Proxy Deployment: Software proxies are deployed on both the source and destination devices. These proxies act as intermediaries, relaying data streams between the secure tunnel and the device applications.
- Secure Connection: The source and destination proxies use access tokens to connect to the AWS IoT Secure Tunneling proxy server. This establishes an encrypted and authenticated connection, ensuring the security of your data.
- Data Transmission: Once the tunnel is established, you can securely transmit data between your local machine and the remote IoT device. This can include SSH connections for remote operation, debugging, and more.
To further illustrate the capabilities of AWS IoT Secure Tunneling, consider some use cases that showcase its versatility:
- Remote Debugging: When a device in the field experiences an issue, you can establish a secure tunnel to remotely access the device and debug the problem, eliminating the need for physical access.
- Software Updates: Securely update the software on your remote devices without compromising your network's security. This can be done even if the devices are behind a firewall.
- Remote Monitoring: Monitor the performance and health of your IoT devices remotely, and receive real-time alerts if an issue arises.
- Device Diagnostics: Remotely run diagnostics on your IoT devices to identify potential problems or areas for improvement.
The following table provides a detailed overview of the functionalities and settings involved:
- Who Is Mohammad Bin Salmans Wife Family Life Details
- What Does Eepy Mean Origins Uses Of Internet Slang
| Feature | Description | Details |
|---|---|---|
| Bidirectional Communication | Enables two-way data flow between local and remote devices. | Crucial for interactive operations and remote control. |
| Firewall Compatibility | Operates without needing inbound firewall rule updates. | Maintains existing security protocols at remote sites. |
| AWS IoT Management | Connection management is handled by AWS IoT. | Simplifies setup and ongoing maintenance of secure links. |
| Secure Connection | Data is transmitted over a secure, encrypted channel. | Protects sensitive data from unauthorized access. |
| Remote Access | Provides secure remote access to IoT devices from anywhere. | Increases operational efficiency and reduces downtime. |
| Use Cases | Examples include debugging, updates, and diagnostics. | Demonstrates the versatility of the service. |
| Demo Availability | An AWS IoT Secure Tunneling demo is available on GitHub. | Offers a practical example to understand the process. |
| Access Control | Requires appropriate permissions to access the 'opentunnel' action. | Ensures secure access control. |
| Token Management | Includes an option to specify a timeout for credentials. | Enhances security through timely token expiration. |
| Bandwidth Considerations | Maximum bandwidth per tunnel is defined. | Important for maintaining connection quality. |
| Tunnel Management in Console | Tunnels can be managed via the AWS IoT console. | Offers control over tunnel creation, deletion, and monitoring. |
| API Operations | Includes API options like 'CloseTunnel'. | Provides flexibility in managing tunnels through programmatic access. |
| IAM Roles and Policies | Best practices recommend using IAM roles and policies. | Enforces strict access control. |
| Tunnel Multiplexing | A single tunnel can support up to three data streams. | Enhances efficiency by using multiple TCP connections per stream. |
| Logging & Monitoring | Monitor endpoint resource usage and cloudwatch metrics. | Provides insights into tunnel health. |
For a comprehensive understanding and practical application of these concepts, explore the following key aspects of AWS IoT Secure Tunneling. Start local proxy in source mode and start local proxy in destination mode
The "iot agent snippet" in the context of AWS IoT Secure Tunneling, refers to small code snippets that guide you through the setup and configuration of the local proxy on both the source and destination devices.
When setting up an AWS IoT Secure Tunnel, the device needs to be able to connect to the AWS IoT device gateway. The "iot agent snippet" provides guidance on how to set up the connection, how to subscribe to a specific MQTT topic on AWS IoT Core, and how to receive notifications about any AWS IoT tunnels created with that device as a target. These are crucial components for establishing and maintaining a secure tunneling connection.
To delete an individual tunnel or multiple tunnels from the AWS IoT console, go to the tunnels hub, choose the tunnels that you want to delete, and then choose delete tunnel.To delete an individual tunnel or multiple tunnels using the AWS IoT API reference API, use the closetunnel API operation.
When using AWS IoT Secure Tunneling, the device might get disconnected unexpectedly even if the tunnel is open. A device can get disconnected for multiple reasons. Here are some factors you should keep in mind.
Here is a set of best practices for securing IoT devices with AWS IoT Secure Tunneling:
- IAM Roles and Policies: Use AWS Identity and Access Management (IAM) roles and policies to control access. This ensures that only authorized entities can create and manage secure tunnels.
- Minimize Token Lifetimes: Specify a short timeout for credentials to mitigate the risk of unauthorized access if tokens are compromised.
- Monitor Tunnel Health: Use CloudWatch metrics to monitor tunnel state changes and packet loss. This can help you quickly identify and address any issues that may arise.
- Create Allow Lists: Create an allow list of AWS IoT IPs and domains in local firewall policies to restrict the network traffic allowed to and from your devices.
- Close Unused Tunnels: When the task is complete, use the AWS IoT console to close the tunnel for security reasons.
This system seamlessly integrates with AWS IoT services, utilizing a software proxy on both source and destination devices. This proxy facilitates a smooth data stream relay between the secure tunneling service and your device application. You will also need to have permission to access the opentunnel action. After the tunnel has been opened, AWS IoT device management provides the cat for the source that you can download on the source.
Here are some of the key components and features of AWS IoT Secure Tunneling:
- The Tunnel: A secure communication channel managed by AWS IoT.
- The Source Proxy: A software component that runs on your local machine (source) and initiates the connection.
- The Destination Proxy: A software component that runs on your remote device (destination) and handles incoming connections.
- Access Tokens: Credentials used by the proxies to authenticate with the AWS IoT Secure Tunneling service.
- The AWS IoT Console: The interface you use to manage and monitor your tunnels.
When the tunnel is created, make sure to do following things.
Here\u2019s where things get interesting! You can run the script to securely bind your machine to your iot device directly from your terminal.
In conclusion, AWS IoT Secure Tunneling offers a robust, secure, and user-friendly solution for remote access to your IoT devices. By simplifying the complexities of network configuration and providing a secure, managed connection, AWS IoT Secure Tunneling empowers you to efficiently manage your devices, troubleshoot issues, and optimize your IoT operations.

Detail Author:
- Name : Pierre Gaylord DVM
- Username : vsanford
- Email : cecil.volkman@kautzer.org
- Birthdate : 1983-03-18
- Address : 85584 Hickle Landing Suite 026 Bruenborough, KY 89755-2019
- Phone : 267-308-3115
- Company : McGlynn, Senger and Ward
- Job : Radiologic Technologist and Technician
- Bio : Quibusdam itaque enim nulla alias. Numquam beatae ipsa aut consequatur ea architecto totam cum. Qui dolorum iusto nobis non. Soluta quisquam distinctio nihil dolorem eum vero quas impedit.
Socials
instagram:
- url : https://instagram.com/boyer2012
- username : boyer2012
- bio : Consequatur explicabo itaque aut qui ex qui. Animi et ut dolorum. Assumenda aut neque voluptatibus.
- followers : 827
- following : 1451
linkedin:
- url : https://linkedin.com/in/pboyer
- username : pboyer
- bio : Rerum unde distinctio eum quia minus.
- followers : 1641
- following : 1067
twitter:
- url : https://twitter.com/pierreboyer
- username : pierreboyer
- bio : Qui quaerat aliquid dolorem inventore nihil ipsum maiores. Provident officia reprehenderit doloribus laborum quam consequatur.
- followers : 6859
- following : 1648