Secure IoT Access: SSH & AWS - Your Guide To Remote Device Management
In an increasingly interconnected world, where devices are scattered across remote locations and often locked behind stringent firewalls, how do we efficiently and securely manage them? The answer lies in the power of remote access and the robust capabilities of technologies like Secure Shell (SSH) tunneling and the Internet of Things (IoT).
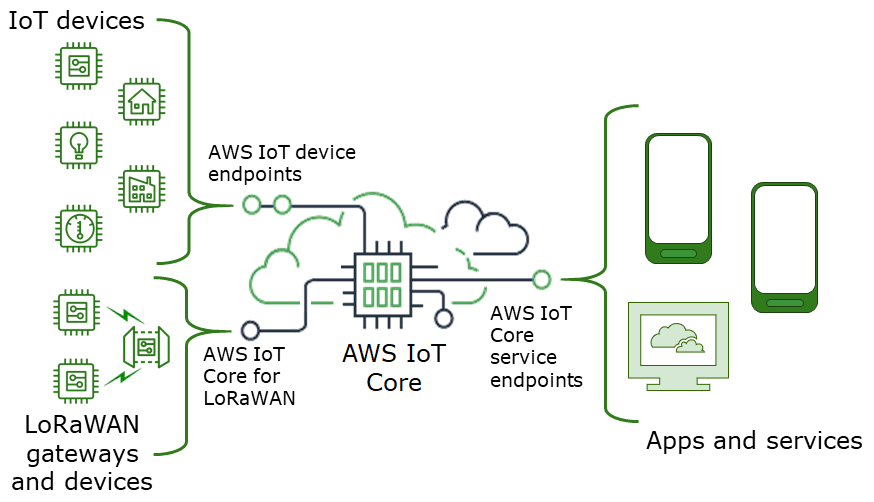
The ability to troubleshoot, update configurations, and perform other vital operational tasks on devices deployed in challenging environments is paramount. Secure tunneling, a feature within AWS IoT Device Management, has emerged as a critical solution for many organizations, providing a reliable means to accomplish these remote tasks. This technology allows for the establishment of bidirectional communication with remote devices, all managed over a secure connection facilitated by AWS IoT. One of the key advantages of secure tunneling is its ability to function without requiring modifications to existing inbound firewall rules, thereby maintaining the same level of security afforded by the firewall at a remote site. This approach contrasts with traditional methods that may demand constant updates or complex configurations.
| Key Concepts | Details |
|---|---|
| Secure Tunneling | A feature within AWS IoT Device Management that allows for secure, bidirectional communication with remote devices. It leverages a secure connection managed by AWS IoT, eliminating the need to update inbound firewall rules. |
| SSH (Secure Shell) | A cryptographic network protocol for operating network services securely over an unsecured network. It provides a secure channel over an untrusted network. |
| AWS IoT Core | A managed cloud service that lets connected devices easily and securely interact with cloud applications and other devices. |
| Firewall Rules | Rules that govern the flow of network traffic in and out of a network or device, crucial for maintaining security. |
| Remote Access | The ability to access and manage devices or systems from a location other than their physical location. This is a core concept for IoT operations. |
| VPN/Proxy Connection | Alternative methods, typically employed by those not utilizing AWS, offering communication layers to enable devices to connect to the internet and interact with services. |
For further information, please consult the official AWS documentation: AWS IoT Core Official Website
The landscape of IoT is constantly evolving, and the integration of technologies like SSH is becoming increasingly important. The ability to remotely access devices, troubleshoot issues, and update configurations without physical presence significantly enhances operational efficiency and reduces downtime. Within the context of AWS, this often involves using the AWS IoT Core service, which provides a secure and scalable platform for managing these connections.
Let's delve into the specifics. Consider the challenge of managing numerous IoT devices deployed at remote sites, each behind a restricted firewall. Without a secure and reliable remote access mechanism, troubleshooting, software updates, and critical configuration changes become difficult and time-consuming. Secure tunneling, as offered by AWS IoT, provides a solution by establishing secure, bidirectional communication channels directly to these devices. This process does not necessitate changes to existing firewall configurations, maintaining the security posture while providing essential access.
For those not utilizing the AWS ecosystem, a more traditional approach might involve using SSH combined with a Virtual Private Network (VPN) or a proxy connection. These methods also offer communication pathways for devices to interact with the internet and, by extension, other services. However, AWS IoTs secure tunneling often streamlines the process, offering a more managed and integrated solution, specifically tailored to the needs of IoT devices and environments.
- Jeremy Meeks From Mugshot To Model His Inspiring Journey
- Mathew Knowles From Destinys Child To Beyoncs Dad Beyond
As we explore the details, the focus is on the practical aspects of implementing secure remote access for IoT devices. The core concept remains: establishing secure communication channels between the devices and the infrastructure managing them. This involves leveraging protocols like SSH and cloud services provided by AWS. By understanding these fundamentals, it is possible to streamline device management, enhance security, and optimize the workflow. The combination of SSH and AWS IoT services creates a framework for managing connected devices effectively.
The use of SSH in conjunction with AWS IoT empowers you to stay in control, minimize downtime, and improve device management without needing to be physically near each device. This level of remote access facilitates efficient management, troubleshooting, and maintenance. It is essential to recognize that security is paramount in the IoT landscape, where devices may contain sensitive data or be responsible for critical operations. Proper SSH configuration and adherence to best practices are indispensable for securing connections and safeguarding data.
To use secure tunneling, the initial step is to prepare your IoT device for SSH access. This may involve installing necessary software components and configuring the device to accept SSH connections. Following this, you can utilize AWS IoT Core to establish a secure tunnel. The AWS IoT console provides an interface to open tunnels and manage the connections. When the tunnel is created, you receive access tokens for the source (e.g., your AWS environment) and destination (the remote device). These tokens are used to authenticate and secure the connection. The process involves the AWS infrastructure managing the secure exchange of data between the source and destination, ensuring the privacy and integrity of communications.
When creating an SSH tunnel, it's often necessary to have created an IoT thing in the AWS IoT registry. An IoT thing represents a physical or logical device in the cloud. Once the device is registered and configured, you can proceed to open the tunnel using the quick setup method, which is a streamlined way to rotate access tokens and initiate an SSH connection within your browser. This method simplifies the process of accessing a remote device.
The best practices for SSH configuration are crucial for ensuring a secure and reliable setup. This includes using strong passwords or SSH keys, regularly updating SSH server software, and restricting access to authorized users only. Additionally, monitoring SSH logs and configuring security groups to control network traffic are vital. Securely configuring SSH helps to protect devices from unauthorized access and potential security breaches.
Consider a scenario where you are attempting to establish an SSH tunnel between your AWS environment and a remote device, such as your Macbook. The process begins with setting up the tunnel using AWS IoT Core. Upon successful creation, you receive access tokens specifically for the source (AWS) and the destination (Macbook). These tokens facilitate the secure exchange of data and establish the connection. The security of this connection is maintained through the AWS infrastructure. This method supports bidirectional communication, enabling you to send commands, receive data, and perform various operations on the remote device.
Many organizations have successfully implemented remote IoT VPC (Virtual Private Cloud) SSH solutions to enhance their operations. For example, a manufacturing company might employ AWS VPC and SSH to remotely monitor and control industrial IoT devices. This approach streamlines operations, improves efficiency, and reduces downtime. This underlines the practical benefits and real-world applications of combining these technologies.
The quick setup method enables the rotation of access tokens and allows you to SSH into the remote device within your browser. However, depending on the requirements and complexity of your setup, using your own server can give you greater control and flexibility. This approach provides options to customize your environment and streamline operations.
In essence, the core focus of IoT SSH connect is creating secure connections between devices within an IoT ecosystem. SSH offers a secure means to access and manage remote systems, making it an excellent choice for IoT applications where remote management is often necessary. The process can include setting up the destination device for SSH access, which involves configuring the device and enabling SSH services.
AWS IoT Device Management offers a rich set of tools that enable businesses to build IoT applications across many different industries. However, when it comes to remote access to devices, it typically involves sending a control message through an MQTT topic or updating the devices shadow. The device agent will then take action. The introduction of SSH offers a different way to connect to and maintain devices remotely.
Whether you're a seasoned professional or just starting in the world of IoT, understanding these principles is crucial. The seamless integration of SSH and AWS IoT offers a secure, scalable, and efficient means of managing your connected devices. It provides a powerful framework for accessing, monitoring, and controlling your IoT infrastructure from anywhere in the world.


Detail Author:
- Name : Pierre Gaylord DVM
- Username : vsanford
- Email : cecil.volkman@kautzer.org
- Birthdate : 1983-03-18
- Address : 85584 Hickle Landing Suite 026 Bruenborough, KY 89755-2019
- Phone : 267-308-3115
- Company : McGlynn, Senger and Ward
- Job : Radiologic Technologist and Technician
- Bio : Quibusdam itaque enim nulla alias. Numquam beatae ipsa aut consequatur ea architecto totam cum. Qui dolorum iusto nobis non. Soluta quisquam distinctio nihil dolorem eum vero quas impedit.
Socials
instagram:
- url : https://instagram.com/boyer2012
- username : boyer2012
- bio : Consequatur explicabo itaque aut qui ex qui. Animi et ut dolorum. Assumenda aut neque voluptatibus.
- followers : 827
- following : 1451
linkedin:
- url : https://linkedin.com/in/pboyer
- username : pboyer
- bio : Rerum unde distinctio eum quia minus.
- followers : 1641
- following : 1067
twitter:
- url : https://twitter.com/pierreboyer
- username : pierreboyer
- bio : Qui quaerat aliquid dolorem inventore nihil ipsum maiores. Provident officia reprehenderit doloribus laborum quam consequatur.
- followers : 6859
- following : 1648