SSH Remote Access: Free Guide For IoT & Raspberry Pi
Are you tired of being tethered to your desk, unable to access your Ubuntu Linux machine or IoT devices when you're away? Unlock the limitless potential of remote access and secure control with Secure Shell (SSH), a powerful tool that puts you in command from anywhere, anytime.
The digital age demands flexibility and accessibility. Whether you're a seasoned developer, a tech enthusiast, or a professional managing a network of interconnected devices, the ability to securely access and control your systems remotely is no longer a luxury, but a necessity. This is particularly true in the realm of the Internet of Things (IoT), where devices are often deployed in geographically dispersed locations, requiring robust and secure remote management solutions.
Secure Shell (SSH) is the cornerstone of secure remote access. It provides a secure channel over which you can interact with your remote systems. Unlike older, less secure protocols like Telnet, SSH encrypts all communication, protecting your data and credentials from prying eyes. This is especially critical when dealing with sensitive information or managing critical infrastructure.
- Jeremy Meeks From Mugshot To Model His Inspiring Journey
- Kristi Noems Transformation Before After Whats Changed
One of the core advantages of SSH is its flexibility. It can be used for a wide variety of tasks including secure file transfer, remote command execution, and tunneling network connections. This versatility makes it an indispensable tool for system administrators, developers, and anyone who needs to manage remote servers or devices. The key to this versatility lies in its ability to establish encrypted tunnels, enabling secure communication even when the underlying network isn't inherently secure. With the establishment of a secure SSL/TLS tunnel, you can use SSH to access your IoT devices remotely. This eliminates the need to expose your devices to the public internet directly, significantly enhancing their security.
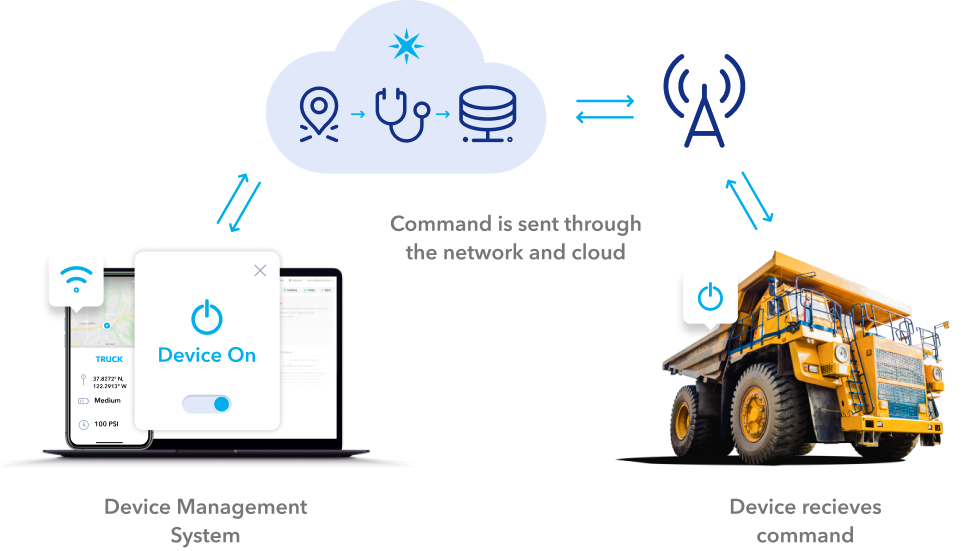
There are several methods of establishing a secure connection, including using public key authentication and port forwarding. The latter is a common technique, but it requires configuring your router to forward specific ports to your target device. This can be cumbersome and potentially expose your device to vulnerabilities if not configured correctly. One of the most advantageous methods is utilizing SSH remote access without port forwarding. This is a highly recommended method to enhance security by eliminating the need to open ports on your router. This approach typically involves establishing a secure connection to a third-party server that acts as an intermediary, allowing you to bypass the need for port forwarding altogether.
Several free and commercial tools are available that simplify this process. Tools like Tectia SSH provide robust features, including 24/7 support and certificate-based authentication. Other platforms such as SocketXP and RemoteIoT offer innovative solutions for accessing IoT devices, simplifying the process of creating secure, remote connections. By leveraging these technologies, you can create a secure and reliable environment for accessing your IoT devices, regardless of your physical location.
- Is Iron Resurrection Returning In 2025 Latest Updates News
- Oxleakscom Is It Legit Or A Scam Reviews Analysis
Many free alternatives exist for SSH remote IoT. This includes OpenSSH (a widely used open-source implementation of the SSH protocol) and PuTTY (a popular SSH client for Windows). Tools like the RemoteIoT platform also offer options, allowing users to manage their IoT devices remotely via secure channels. These tools provide essential functionalities for managing remote connections, including secure authentication, encrypted data transfer, and remote command execution. The Raspberry Pi, due to its affordability and versatility, is the perfect device for testing and building secure remote access IoT projects.
A critical aspect of any remote access setup is implementing and understanding best security practices. This includes the use of strong passwords, regularly updating your system, and employing techniques like two-factor authentication to add an extra layer of security. With the right tools and a strong understanding of security best practices, you can create a robust and secure remote access infrastructure for your IoT devices.
Remote access to IoT devices isn't just about control; it's about data. By accessing the data generated by your IoT devices remotely, you can monitor performance, diagnose issues, and make informed decisions based on real-time information. This opens up new possibilities for optimizing your IoT deployments, increasing efficiency, and improving the overall user experience.
For a comprehensive guide to setting up and maintaining SSH remote access, it's vital to familiarize yourself with the steps involved. This guide walks you through everything you need to know to configure your devices for remote access, emphasizing the importance of security at every stage. Also, by restricting IoT device access to specific IP addresses, you can add an extra layer of protection against unauthorized access. The use of tools like socketxp enhances this process, allowing the creation of secure tunnels that make your devices virtually invisible to port scans and protect them from DDoS attacks.
With the right tools and a strong understanding of security best practices, you can create a robust and secure remote access infrastructure for your IoT devices. Remember, secure remote access is more than just a convenience; it is a necessity. So, protect your devices. Maintain your devices.
| Feature | Details |
|---|---|
| SSH Remote Access | Enables secure access and control of devices from any location using the Secure Shell (SSH) protocol. |
| Security | Encrypts all communication, protecting data and credentials. Avoids port forwarding, enhancing security. |
| Flexibility | Allows for secure file transfer, remote command execution, and tunneling network connections. |
| Free Tools | Includes OpenSSH, PuTTY, and the RemoteIoT platform, offering free download options for starting IoT projects. |
| Commercial Options | Tectia SSH provides 24/7 support and certificate support. |
| Platform Compatibility | Compatible with Windows, Android, and Raspberry Pi, promoting cross-platform management. |
| SocketXP | Provides a web portal for access, with features like an xterm terminal icon next to devices. |
| Best Practices | Emphasizes using strong passwords, regular system updates, and two-factor authentication for security. |
| RemoteIoT Platform | Offers a free download option to manage IoT devices remotely, ensuring seamless connectivity. |
The RemoteIoT platform ssh addresses this by offering a free download option for users who want to manage their iot devices remotely.
For those utilizing Raspberry Pi devices, the ssh remote iot raspberry pi free download concept is revolutionizing how developers and hobbyists interact with IoT devices. Several free options exist for SSH remote IoT, including OpenSSH, PuTTY and tools such as the RemoteIoT platform. You can set up remote access using an Android device. Learn how to securely enable remote SSH login for IoT devices using Android. Begin by generating SSH keys on your Android device and configuring your IoT device for SSH access.
Consider these step for setting up the configuration:
- Download and Install: Download and install the necessary SSH client.
- Get Authentication Token: Obtain an authentication token from your service provider.
- Configure IoT Remote SSH: Configure the IoT device for remote web service access.
This setup is critical for building scalable connected systems, enabling efficient management and control.
Managing remote SSH login IoT passwords securely is a comprehensive process. Learn about how to restrict IoT device access to specific IP addresses or login IP in the web browser. Protecting your devices against DDoS attacks and making them virtually invisible to port scans is also essential. The ability to access your IoT devices SSH server using a local endpoint provides an added layer of security and simplifies the connection process. Accessing IoT devices remotely is essential for managing smart systems efficiently, and Secure Shell (SSH) provides a secure way to do so.
Several options are available for remote access:
- Access the socketxp web portal.
- Access your US IoT gateway.
- Start your free trial today.
By leveraging these tools, you can create a secure and reliable environment for accessing your IoT devices from anywhere. Whether youre managing a single device or a complex network of interconnected systems, the concepts outlined in this guide are invaluable for securing remote access and taking full control of your devices.
For brief introductions of different alternatives, you can consult an ssh client page. There is also an extensive ssh client comparison page on Wikipedia. And remember: while numerous free options exist, it is essential to understand and implement the best practices for security.
In conclusion, the combination of SSH and IoT, particularly in the context of Raspberry Pi, is transforming the way we interact with technology. With the information and tools, you can confidently manage your devices remotely, increase efficiency, and enhance the security of your systems. Embrace the power of secure remote access and unlock the full potential of your connected world.

Detail Author:
- Name : Prof. Jaida Bailey
- Username : shoeger
- Email : kameron91@toy.com
- Birthdate : 2003-09-25
- Address : 6575 Schroeder Locks Apt. 322 Cathrynburgh, MD 91368-8499
- Phone : 1-539-316-6793
- Company : Collier, Boyer and Cole
- Job : Electrical Power-Line Installer
- Bio : Sint eos necessitatibus dolorem quam aperiam. A harum amet aliquid et animi optio. Voluptatem consequatur rem ab et eos et. Officia voluptatem beatae quibusdam consequatur est tempora.
Socials
twitter:
- url : https://twitter.com/rogers_williamson
- username : rogers_williamson
- bio : Esse praesentium sint qui eius ullam corporis magni. Cupiditate ex exercitationem in sint perferendis fuga. Iusto vitae quasi assumenda deserunt ducimus.
- followers : 832
- following : 2417
linkedin:
- url : https://linkedin.com/in/rogers2446
- username : rogers2446
- bio : Ullam consectetur quam vitae fugit eaque qui et.
- followers : 2870
- following : 590
facebook:
- url : https://facebook.com/williamsonr
- username : williamsonr
- bio : Et qui quos quis facilis rerum.
- followers : 6203
- following : 320