Securely Connect Remote IoT Devices: P2P SSH On Windows 10 & More
Is the digital frontier truly secure, or are we sailing into uncharted waters with our interconnected devices? The ability to securely connect remote IoT devices in a peer-to-peer (p2p) environment on Windows 10 is not just a technical challenge; it's a necessity in today's increasingly networked world.
The world of the Internet of Things (IoT) is expanding rapidly, connecting devices from smart home appliances to industrial sensors. This expansion, however, comes with significant security risks. Data breaches, unauthorized access, and malicious attacks are constant threats. This article delves into the critical steps required to securely connect remote IoT devices using p2p technology on Windows 10, equipping you with the knowledge to protect your systems and data. Setting up a secure remote connection requires a multifaceted approach, encompassing software configuration, security protocols, and a firm understanding of the underlying principles. While the convenience of remote access and control is undeniable, it must be balanced with robust security measures to mitigate the inherent risks. From understanding the role of SSH to implementing encryption, we'll explore the practical techniques and strategies that safeguard your IoT ecosystem.
Let's consider a fictional individual, Alex Chen, a cybersecurity professional working remotely. Alex's expertise lies in securing IoT networks. The following table provides a glimpse into Alex's background and professional expertise:
- Kristi Noems Transformation Before After Whats Changed
- Methstreams Watch Free Live Sports Nfl Nba More
| Category | Details |
|---|---|
| Name | Alex Chen |
| Age | 35 |
| Education | Master of Science in Cybersecurity |
| Professional Experience | 10 years in cybersecurity, specializing in IoT security. |
| Current Role | Lead Security Architect at a major IoT solutions provider |
| Skills | Firewall configuration, intrusion detection/prevention, SSH, VPN, PKI, encryption protocols (TLS/SSL, AES), network segmentation. |
| Certifications | CISSP, CISM, CEH |
| Projects | Developed and implemented secure IoT solutions for smart cities, industrial automation, and healthcare. |
| Website Reference | SANS Institute (IoT Security) |
The journey toward secure remote connectivity begins with understanding the fundamentals. The core issue involves establishing a protected channel for data transmission between your Windows 10 machine and the remote IoT devices. This necessitates employing robust security protocols, ensuring data integrity, and validating the authenticity of both devices. Several methods and protocols contribute to achieving this. The goal is to create a secure, reliable connection that can withstand potential threats.
One of the most fundamental steps is downloading and installing the necessary client software. For many remote access solutions, this starts with downloading and installing the remoteiot client on your Windows 10 device. Always obtain the software from the official website to ensure you are receiving a legitimate, secure version. Installing software from untrusted sources poses a significant security risk, potentially exposing your system to malware or unauthorized access. This step is your first line of defense; make sure the software originates from a verified and trusted source.
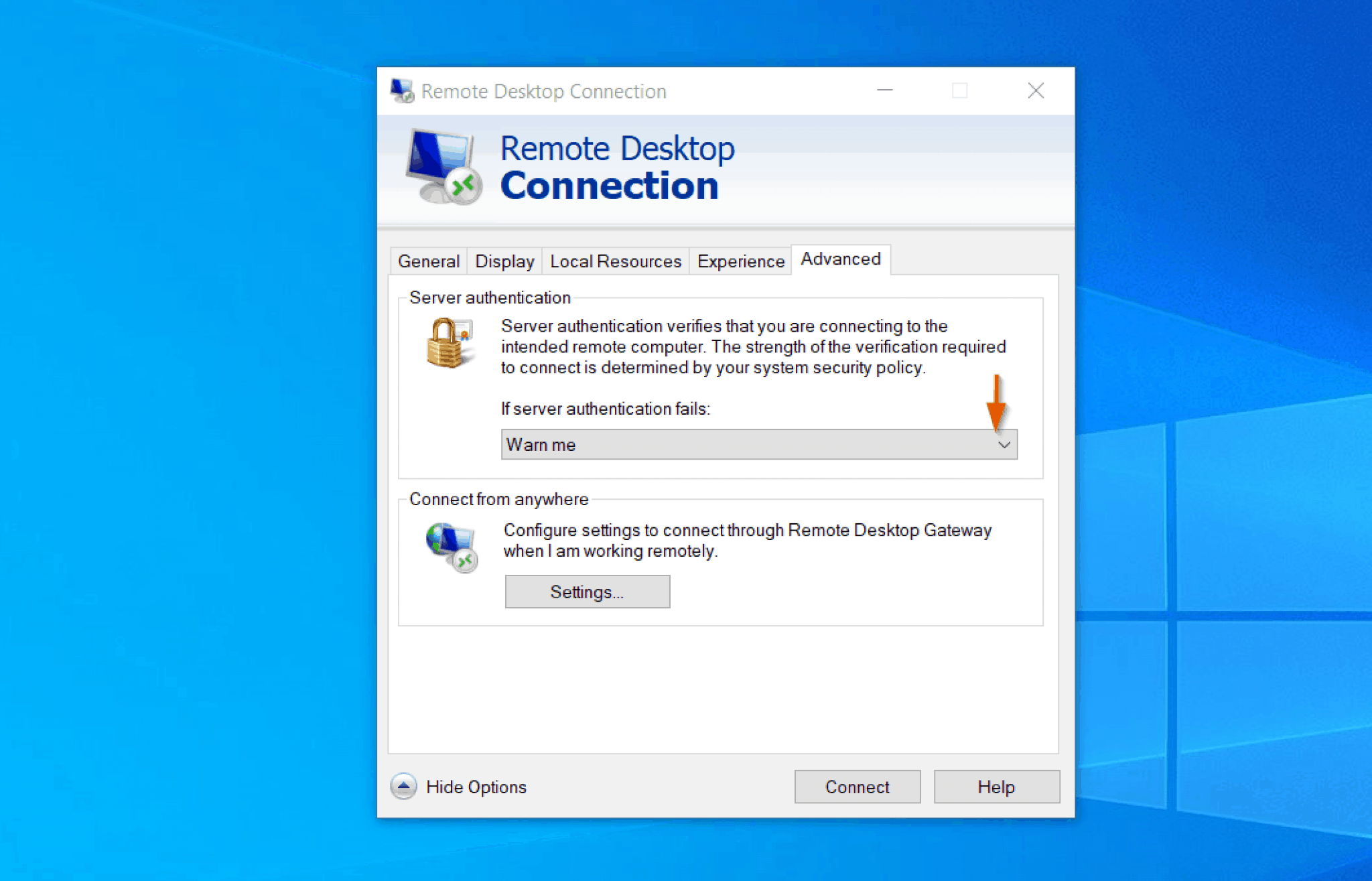
Once the client is installed, the configuration process commences. This involves a series of steps designed to harden the connection. This often involves the configuration of security settings within the remoteiot client. These settings typically include defining access permissions, setting up encryption protocols, and implementing authentication mechanisms. It's crucial to understand and correctly configure these settings to create a secure channel for communication. A poorly configured client can expose your devices to vulnerabilities.
The cornerstone of secure remote access lies in the use of SSH (Secure Shell). SSH provides a secure, encrypted channel for communication over an unsecured network. SSH establishes a secure connection, encrypting all data transmitted between your Windows 10 machine and the remote IoT device, protecting it from eavesdropping or tampering. Discovering how to access SSH on a remote IoT device allows efficient management of your IoT ecosystem. Using SSH you are able to manage the device securely. This is essential for protecting the integrity of the data transmitted. This is especially crucial when dealing with sensitive data or configurations, such as accessing or modifying network settings or transferring confidential information. Implementing SSH ensures that your data remains confidential.
Encryption, authentication, and access control are vital in securing remote IoT connections. Encryption scrambles data, rendering it unreadable to unauthorized parties. Authentication verifies the identity of the devices trying to connect. Access control restricts who can access specific resources. Combining these elements creates a robust security framework. These mechanisms form a layered security approach, working together to protect against a wide range of potential threats.
A significant element in securing remote IoT access lies in the proper configuration of security settings. This is particularly vital when utilizing SSH, since SSH's effectiveness relies on strong cryptographic keys and appropriate access controls. This also extends to configuring firewalls to permit only authorized traffic, and implementing multi-factor authentication to reduce the risk of unauthorized access. Careful configuration will fortify the connection against various cyber threats, thereby securing both the data in transit and the IoT devices themselves.
Testing the connection is a crucial step in ensuring its reliability. After configuring the security settings, a test connection verifies that the remote access is functioning correctly. This involves verifying the ability to connect to the remote device and validate the successful operation of the various security protocols implemented. A successful test run provides assurance that the connection is secure and ready for use. Regularly testing the connection is a good practice.
The Raspberry Pi, often employed in IoT projects, can also be used in the context of secure remote access. The Raspberry Pi, a low-cost, credit-card-sized computer, is popular among tech enthusiasts and professionals who are looking to build and deploy IoT solutions. Implementing secure remote access for the Raspberry Pi involves many of the same principles discussed earlier, including the installation of the appropriate client software, SSH configuration, and adherence to established security protocols. For those looking to securely connect remote IoT devices, consider leveraging the Raspberry Pi Foundation's resources for guidance.
For individuals working in or studying cybersecurity, having the ability to establish secure remote connections with IoT devices is an indispensable skill. This capacity to connect securely is essential for managing, maintaining, and troubleshooting remote devices. It becomes vital for tasks like diagnosing equipment failures remotely, implementing software updates, or monitoring data streams, all without the need to physically access the device.
The evolution of IoT and p2p technology has highlighted the criticality of safeguarding systems. Whether a seasoned technology professional or a casual user, an understanding of how to protect the systems when exploiting the benefits of IoT and p2p is crucial. This understanding includes knowing the best practices, tools, and configurations to securely connect remote IoT devices in a p2p environment. Staying informed on the evolving cyber-threat landscape and proactively implementing security measures are essential for safe IoT operations.
The significance of these secure connections is only growing. The proliferation of interconnected devices means that an increasing number of systems are exposed to potential vulnerabilities. By implementing robust security measures, you mitigate the risk of data breaches, protect sensitive information, and safeguard the integrity of your IoT ecosystem. The benefits of a securely connected IoT environment are far-reaching, encompassing not just data protection, but also operational efficiency, device management, and system stability.
The process of setting up secure remote connections requires careful attention to detail and an understanding of the various components involved. The right approach will incorporate the adoption of secure configuration techniques, implementing robust security protocols, and the usage of secure tools, which will lead to the creation of a strong defense against a broad range of threats. The ability to securely connect remote IoT devices in a p2p network is an increasingly critical skill in today's tech-driven world. Take the appropriate steps now to guarantee your system's security and protect your sensitive data.
When attempting to download software for secure remote access, always prioritize the official source. The official website will be the safest place to obtain the necessary client software, and downloading from unofficial sources can introduce serious security risks. The official site will typically provide the latest and secure versions, protecting your devices from malware and potential vulnerabilities.
The advantages of employing secure remote IoT connectivity on Windows 10 stretch beyond mere accessibility. They provide essential data protection, facilitate smooth device maintenance, and offer complete operational control. With appropriate security procedures in place, one can experience the full advantages of IoT technology without compromising data safety and network integrity.
In a nutshell, securing remote IoT connections involves a multifaceted strategy. This includes downloading and installing the software from reliable sources, configuring security settings correctly, and running test connections for verification. Always ensure that your system is up-to-date, and that the security measures are regularly maintained and updated. Understanding the risks involved and diligently practicing security best practices are key to safeguarding your systems. Implementing these steps ensures the safety of your data, and enables you to harness the power of the IoT without exposing your system to risks.
The Raspberry Pi Foundation provides valuable resources, including guides and tutorials, that can assist in setting up and securing remote access for Raspberry Pi devices. Organizations such as the Raspberry Pi Foundation offer educational resources and support that are essential for learning and deploying these technologies safely. Use their resources to enhance your understanding and skills.


Detail Author:
- Name : Ocie Wisoky
- Username : nathaniel58
- Email : qschumm@hotmail.com
- Birthdate : 1992-05-25
- Address : 229 Tessie View Suite 366 West Rowanfurt, CT 35867
- Phone : (503) 394-8065
- Company : Koepp-Kilback
- Job : Molding and Casting Worker
- Bio : Consequuntur repellendus aliquid vel quasi officiis dolorum neque. Molestias odio velit ea et eius et suscipit. Consectetur cupiditate recusandae blanditiis voluptates.
Socials
twitter:
- url : https://twitter.com/sipesa
- username : sipesa
- bio : Ut consequatur nemo quidem dolores. Officiis voluptatem consequuntur beatae qui deserunt error. Dolores minus dolor exercitationem.
- followers : 5005
- following : 2977
tiktok:
- url : https://tiktok.com/@sipesa
- username : sipesa
- bio : Qui maxime sequi quibusdam aut. Natus aut ipsam ea at adipisci est aperiam.
- followers : 3524
- following : 834