Secure Remote IoT: Free P2P SSH Download For Windows 10
In an era defined by ubiquitous connectivity, how do you ensure the safety and integrity of your Internet of Things (IoT) devices when accessing them remotely, and can you do it without breaking the bank? The answer, surprisingly, is yes, and the key lies in understanding how to securely connect remote IoT devices and leverage peer-to-peer (P2P) technologies, specifically using Secure Shell (SSH) on your Windows 10 system, for free. This article will serve as your comprehensive guide.
The exponential growth of IoT devices, from smart home appliances to industrial sensors, has created a vast landscape of interconnected systems. Managing these devices remotely is no longer a luxury; its a necessity. Whether youre a tech enthusiast managing a home automation setup or a business owner overseeing a network of remote sensors, the ability to securely access and control your IoT devices is paramount. The challenges, however, are numerous. The inherent vulnerabilities of IoT devices, coupled with the complexities of network security, present a significant hurdle for many users. This is where secure P2P connections, especially when combined with SSH, come into play, offering a robust, cost-effective solution.
Let's delve into the specifics. Consider the benefits of P2P SSH:
- Damon Imani On The View Viral Moments Satire You Cant Miss
- Kolkata Doctor Rape Case New Details Updates You Need To Know
- Enhanced Security: SSH employs strong encryption to protect data in transit, safeguarding against eavesdropping and unauthorized access.
- Cost-Effectiveness: Utilizing free tools and open-source technologies like SSH and remoteiot p2p eliminates the need for expensive proprietary solutions.
- Flexibility: P2P connections enable direct communication between devices, bypassing the need for a central server, which can be crucial in environments with limited internet connectivity or stringent security requirements.
- Ease of Implementation: While the concept may seem complex, setting up a secure P2P SSH connection on Windows 10 can be achieved with readily available software and straightforward configuration steps.
This detailed guide will illuminate the process of securely connecting remote IoT devices utilizing P2P SSH on Windows 10, completely free of charge. By the end, you'll be equipped with the expertise to safeguard your IoT ecosystem, empower your remote management capabilities, and significantly reduce your associated costs.
Now, let's begin with the core: the methods and protocols that underpin secure P2P connectivity. These form the foundation upon which your secure remote access strategy will be built.
In essence, the process of securing remote IoT connections involves a multifaceted approach centered on the principles of cryptographic security and access control. These mechanisms, when properly implemented, safeguard against a range of potential threats, from unauthorized access to data breaches. Consider the following key components:
- Baby Alien Fan Bus Videos Watch Explore The Viral Trend
- Cha Eunwoos Religion Unveiling The Kpop Stars Beliefs 2024
- Encryption: At the heart of secure communication lies encryption. Encryption transforms readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic key. Only the intended recipient, possessing the appropriate key, can decrypt the ciphertext back into its original form. This ensures that even if an attacker intercepts the data in transit, they cannot decipher its contents. SSH, for instance, utilizes robust encryption algorithms like AES (Advanced Encryption Standard) to protect data transmitted over the network.
- Authentication: Authentication verifies the identity of the connecting device or user. It ensures that only authorized parties can access the remote IoT device. Common authentication methods include:
- Passwords: Users enter a password to prove their identity. While convenient, passwords can be vulnerable to brute-force attacks and are generally less secure.
- Public-key cryptography: This method uses a pair of keys: a public key, which is shared, and a private key, which is kept secret. The server verifies the user's identity by checking that the user possesses the private key corresponding to the public key. This approach is significantly more secure than password-based authentication.
- Multi-factor Authentication (MFA): MFA combines multiple authentication methods, such as a password and a one-time code generated by a mobile app. This adds an extra layer of security, making it much harder for attackers to gain unauthorized access.
- Access Control: Once a user has been authenticated, access control mechanisms determine what actions they are permitted to perform on the remote IoT device. This involves defining user roles, permissions, and privileges. For example, a user might be granted read-only access to sensor data, while another user has the ability to modify device settings. Access control helps to limit the damage an attacker can inflict if they somehow compromise a user's credentials.
To illustrate the practical application, let's look at how these principles translate into the real world. Using SSH provides a robust and secure means of remotely managing IoT devices.
The technical steps required to securely connect remote IoT devices, particularly within the context of Windows 10, involve several key stages. First, you'll need to establish the underlying infrastructure, which means installing the necessary software. Then, you'll configure the security parameters to ensure the integrity and confidentiality of your data, and finally, you will test the connection to verify that the setup is working correctly. The following is a step-by-step approach:
- Software Installation: The first step is downloading and installing the remoteiot p2p client software. This software serves as the gateway for secure P2P connections. The software is generally available from the official website of remoteiot, always ensuring that you obtain it from a reputable source to avoid potential malware.
- Configuration of Security Settings: After the installation, the software needs to be configured to ensure a secure connection. This process typically involves:
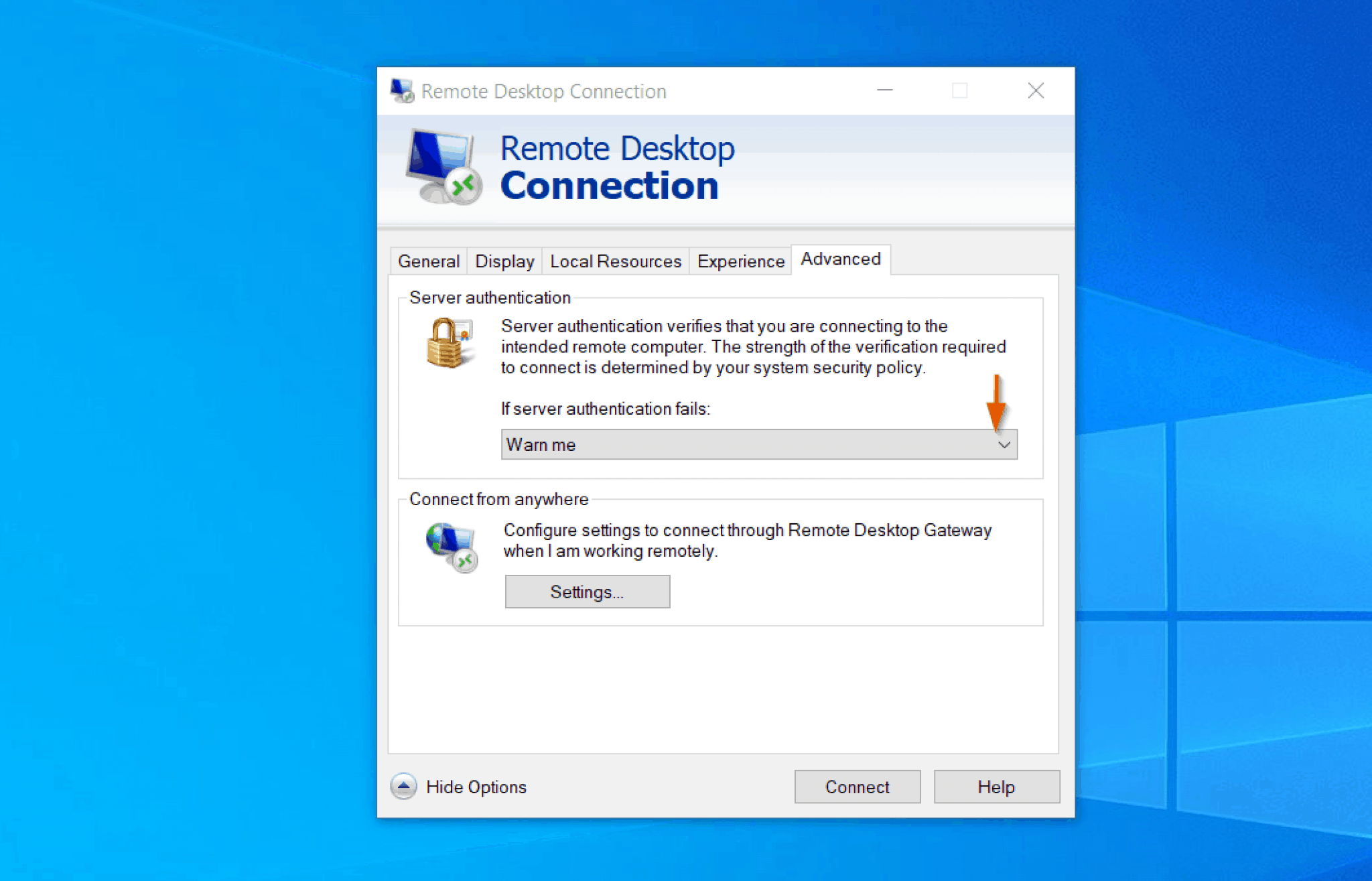
- Setting up an SSH server on your Windows 10 machine You may need to install an SSH server on your Windows 10 machine. Programs like OpenSSH (which comes bundled with recent versions of Windows 10) or PuTTY, provide SSH server functionality.
- Configuring firewall rules: The Windows Firewall needs to be configured to allow incoming connections on the port used by SSH (typically port 22). This involves creating an inbound rule that permits traffic on the specified port.
- Generating and/or using SSH keys: For enhanced security, it is highly recommended to use SSH keys instead of password-based authentication. This entails generating a key pair: a private key that you keep secure and a public key that you share with the IoT device.
- Setting up the remote IoT device The IoT device, such as a Raspberry Pi, must also be configured to accept SSH connections. This involves installing an SSH server on the device and authorizing the public key of your Windows 10 machine.
- Testing the Connection: Once both your Windows 10 machine and the IoT device are properly configured, the final step involves testing the connection. You'll use an SSH client (such as PuTTY on Windows or the built-in SSH client in the command prompt or PowerShell) to connect to the IoT device using its IP address or hostname. Youll then need to provide the user name and, depending on your authentication method, either the password or the path to your private key. If everything is configured correctly, you should be able to securely access the command-line interface of your IoT device.
Remember that the actual configuration steps may vary depending on the specific software and hardware you use, but the underlying principles and sequence of steps generally remain consistent. Detailed instructions can be found on the software's official documentation or in numerous online tutorials.
Let's now address the scenario involving a Raspberry Pi, a popular choice for IoT projects:
Integrating a Raspberry Pi into your secure P2P network mirrors the general steps described above, with a few considerations specific to the Raspberry Pi's architecture and operating system (typically Raspberry Pi OS, a Debian-based Linux distribution).
- Raspberry Pi Setup: First, you'll need to set up your Raspberry Pi, which typically includes installing an operating system on an SD card, configuring the network settings, and connecting the device to your network.
- SSH Server Configuration on Raspberry Pi:
- Enabling SSH: By default, SSH might be disabled on newer Raspberry Pi OS installations. You'll need to enable SSH. You can do this through the Raspberry Pi configuration utility (raspi-config) or by creating an empty file named "ssh" in the boot partition of your SD card before booting the Raspberry Pi.
- Configuring SSH Key Authentication: (Highly Recommended) Generate an SSH key pair on your Windows 10 machine. Copy the public key to the Raspberry Pi's ".ssh/authorized_keys" file for the user you will be using for SSH access (usually the 'pi' user). This enables secure key-based authentication.
- Setting a Strong Password: (If using password authentication) If you opt for password authentication (which is less secure than key-based authentication), make sure to change the default password for the 'pi' user (or any other user you use for SSH access) to a strong, unique password.
- Network Configuration:
- Static IP or DHCP Reservation: Assign a static IP address to your Raspberry Pi or configure your router to reserve a specific IP address for the device. This ensures a stable IP address, which is crucial for reliable remote access.
- Port Forwarding (If applicable): If your Raspberry Pi is behind a router and you want to access it from outside your local network, you'll need to configure port forwarding on your router. Forward port 22 (or the port you have configured for SSH) to the Raspberry Pi's IP address.
- Testing the Connection: Using an SSH client on your Windows 10 machine, attempt to connect to your Raspberry Pi using its IP address or hostname. If you've used SSH key authentication, you should be able to connect without being prompted for a password (or with the password for your private key if you've secured it with a passphrase).
Once you have successfully established a secure connection to your Raspberry Pi, you can then use SSH to manage the device remotely, transfer files securely (using tools like SCP or SFTP), and run commands on the Raspberry Pi's command line. You can also set up P2P connections by utilizing tools like remoteiot, the process would be the same, download, install and configure, then you can register your Raspberry Pi.
Security, however, is not a set-it-and-forget-it proposition. It demands ongoing vigilance and proactive measures to address potential vulnerabilities. It's an evolving landscape where attackers constantly seek new avenues of exploitation. This necessitates a multi-layered approach to security, encompassing not only the technical aspects of connection setup but also the broader ecosystem of your IoT devices.
Here's how to enhance the security of your setup:
- Regular Software Updates: Keep your operating systems, SSH servers, and any other software components up-to-date with the latest security patches. Software updates often address known vulnerabilities.
- Strong Passwords and Key Management: As mentioned, use strong, unique passwords (if using them), and always prioritize SSH key-based authentication. Change passwords regularly and protect your private SSH keys with a passphrase.
- Firewall Configuration: Configure firewalls on both your Windows 10 machine and your Raspberry Pi (or other IoT devices) to restrict incoming and outgoing network traffic. Only allow necessary traffic on specific ports.
- Network Segmentation: If possible, segment your network to isolate your IoT devices from other devices. This limits the potential damage if one of your IoT devices is compromised.
- Monitoring and Logging: Implement monitoring and logging to detect suspicious activity, such as failed login attempts or unusual network traffic. This can help you identify and respond to potential security breaches.
- Disable Unnecessary Services: Disable any services on your IoT devices that are not required. Each service represents a potential attack vector.
- Physical Security: Protect your IoT devices physically. Ensure they are not accessible to unauthorized individuals.
Real-World Examples
Consider a scenario where a small business wants to remotely monitor temperature and humidity sensors in a warehouse:
- Hardware: Raspberry Pi configured with sensors and connected to a local network.
- Software: Appropriate sensor drivers and data logging applications installed on the Raspberry Pi.
- Setup: Using the steps outlined in this guide, the business owner configures the Raspberry Pi for secure SSH access from their Windows 10 computer. This enables the owner to monitor the data logs.
- Benefits: The business owner can monitor sensor data remotely, set up alerts, and troubleshoot issues without visiting the warehouse physically, leading to cost savings and improved operational efficiency.
Or, a home automation enthusiast with a smart home setup, including a Raspberry Pi for managing lights, security cameras, and other devices:
- Hardware: Raspberry Pi controlling the various smart home devices, connected to a home network.
- Software: Home automation software installed on the Raspberry Pi.
- Setup: The enthusiast uses the steps in this guide to enable secure SSH access to the Raspberry Pi from their Windows 10 computer, allowing them to remotely control the lights, security cameras, and other devices.
- Benefits: The enthusiast can control the smart home devices from anywhere with an internet connection, enhancing convenience and security.


Detail Author:
- Name : Prof. Delilah Boyer
- Username : champlin.alex
- Email : greenfelder.stacy@yahoo.com
- Birthdate : 1987-02-17
- Address : 785 Spencer Walk Suite 268 West Cedrick, NV 39178
- Phone : 838.681.2011
- Company : Batz, Reichert and Streich
- Job : Agricultural Equipment Operator
- Bio : Expedita atque repudiandae optio. Est deserunt ipsum atque doloribus molestiae nam. Ut voluptatem deleniti architecto dolorum.
Socials
facebook:
- url : https://facebook.com/catharine.batz
- username : catharine.batz
- bio : Dolores quos laboriosam ab ullam cupiditate quibusdam.
- followers : 4446
- following : 713
tiktok:
- url : https://tiktok.com/@cbatz
- username : cbatz
- bio : Animi officia amet eum repudiandae beatae qui qui.
- followers : 950
- following : 1513
instagram:
- url : https://instagram.com/batz1993
- username : batz1993
- bio : Sit magnam quae quod enim nam est qui. Consectetur aut fugiat in. Velit et beatae ut ipsa facere.
- followers : 4165
- following : 1562
linkedin:
- url : https://linkedin.com/in/catharine9518
- username : catharine9518
- bio : Voluptatem ut eum soluta.
- followers : 1119
- following : 1356