Secure IoT Access: P2P SSH On Windows 10 Guide
Are you struggling to remotely manage and monitor your Internet of Things (IoT) devices, fearing unauthorized access and data breaches? Securing your IoT infrastructure doesn't have to be a daunting task, and leveraging the power of Peer-to-Peer (P2P) SSH on Windows 10 provides a robust and accessible solution.
The ever-expanding world of interconnected devices presents both incredible opportunities and significant security challenges. From home automation systems to industrial control units, the ability to securely connect to and manage these devices remotely is paramount. This is where SSH (Secure Shell) and P2P connections come into play, offering a powerful combination for encrypted communication and enhanced security. The core of this process lies in establishing an SSH client, setting up port forwarding (if necessary), and ensuring the IoT device is correctly configured and accessible. The inherent security features of SSH, coupled with the flexibility of P2P connections, allow for a secure and efficient method of remote device management, protecting sensitive data and preventing unauthorized access.
Before diving into the technical aspects, it's crucial to understand the underlying principles. SSH is a cryptographic network protocol that provides secure communication over an unsecured network. It establishes a secure channel between a local and a remote computer, encrypting the data transmitted between them. This encryption prevents eavesdropping and tampering, making it a secure method for remote access. P2P connections, on the other hand, allow for direct communication between two devices without the need for a central server. This can be particularly useful in scenarios where devices are behind firewalls or on private networks, as it reduces the attack surface and simplifies the setup process. By combining these technologies, users can create a secure and efficient method for remote IoT device management.
- Morena Mitch Videos Explore The Hottest Content
- Amirah Dyme Wiki Bio Age More Everything You Need To Know
For those unfamiliar with the technology, there is a lot to learn, but the rewards are well worth the effort. The combination of SSH and P2P provides a solid foundation for secure remote access. Implementing this type of setup allows users to monitor their IoT devices from anywhere in the world, receiving real-time information and making necessary adjustments. For businesses, this translates to streamlined operations and reduced downtime, while for hobbyists, it opens up a world of possibilities for experimentation and remote control. Whether youre a seasoned IT professional or a tech-savvy individual, the ability to securely connect to remote IoT devices is an essential skill in today's interconnected world.
Key Components and Preparations:
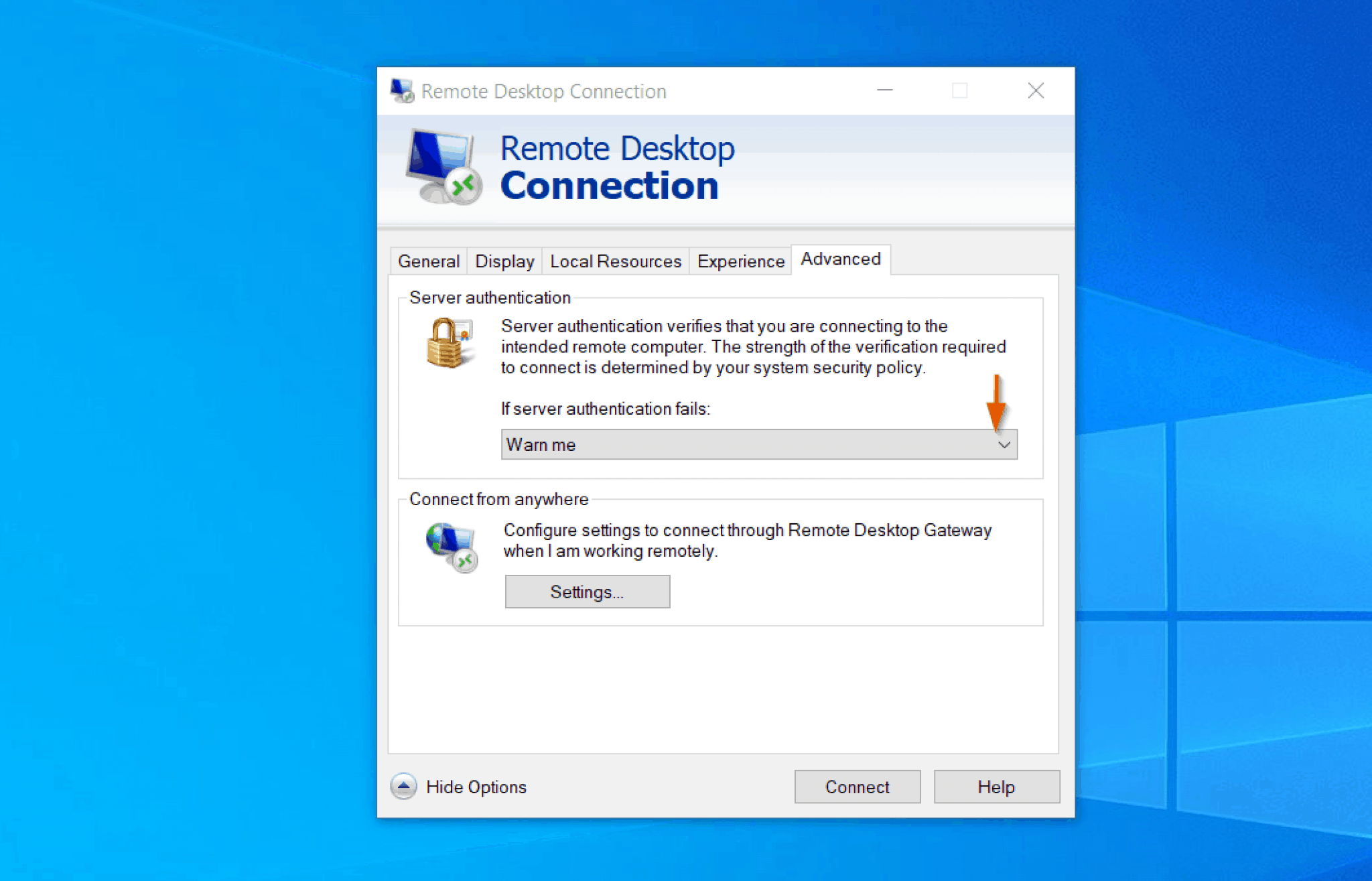
The process of setting up a secure P2P SSH connection on Windows 10 involves several key steps. Firstly, you'll need to ensure you have the right tools in place. Windows 10's native OpenSSH capabilities provide all the necessary features to establish these secure, direct connections. If you prefer, or for more advanced control, you can also opt for third-party SSH clients like PuTTY, which are readily available and offer a user-friendly interface. Whichever option you choose, the first step is installing and configuring an SSH client on your Windows 10 machine.
Next, you'll need to configure your IoT device for SSH access. This typically involves enabling SSH on the device itself and setting up user credentials. The exact steps will vary depending on the device's operating system and configuration, but generally involve accessing the device's settings or control panel and enabling the SSH service. Ensure to set strong passwords or implement key-based authentication to enhance security. Its recommended to use strong, unique passwords and to change them regularly. Also, be sure to update the devices firmware to the latest version to patch known vulnerabilities. Proper user management and security settings are crucial in this phase.
Finally, youll need to set up your network for remote access. This may involve configuring port forwarding on your router, allowing traffic from the internet to be directed to your Windows 10 machine. However, with P2P connections, this step may not always be necessary, especially if your devices can directly connect to each other without relying on a central server. P2P SSH often bypasses the need for traditional port forwarding, simplifying the setup and increasing security. Its important to remember that opening ports on your router can increase the risk of unauthorized access, so it is best practice to be extremely careful in its configuration. Always use strong passwords and consider using a firewall to further protect your network.
Step-by-Step Guide to Setting Up a Secure P2P SSH Connection:
1. Install an SSH Client: As mentioned earlier, Windows 10 has a built-in OpenSSH client. You can verify if its installed by opening the Command Prompt or PowerShell and typing `ssh`. If it's not installed, you'll need to install it through the Windows Settings app under Apps -> Optional Features. If you prefer a GUI client, you can download and install PuTTY or another SSH client of your choice.
2. Configure Your IoT Device: Enable SSH on your IoT device. This process varies depending on the device, but typically involves logging into the device's management interface and enabling the SSH service. This could be through a web interface, command line, or dedicated application. Make sure you create a secure user account with a strong password. For enhanced security, consider using SSH key-based authentication, which is generally more secure than password authentication.
3. Establish a P2P Connection (If Applicable): The specifics of a P2P connection will depend on the nature of your devices and network. If your devices are on the same local network, they can often communicate directly without special configuration. If your devices are on separate networks, you might need to use a P2P VPN or a similar solution. Tools like ZeroTier or Tailscale can simplify the creation of a P2P network. These tools create virtual private networks (VPNs) that allow your devices to securely communicate with each other over the internet as if they were on the same local network. This makes the setup considerably easier.
4. Connect via SSH: Once the SSH client is installed and configured on your Windows 10 machine and your IoT device is configured for SSH, you can establish a connection. Open your SSH client (Command Prompt, PowerShell, or PuTTY). Then use the following command (replacing the placeholders with your devices information): `ssh [username]@[IP address or hostname of your IoT device]`. Enter the password when prompted (or the passphrase for your SSH key). If this connection is successful, you will be connected to your device.
5. Security Best Practices: The security of your connection depends on the security of your configuration. Ensure you are employing these best practices: Use strong, unique passwords or SSH keys. Keep your SSH client and server up to date. Disable password authentication if possible and use key-based authentication. Firewall your Windows 10 machine and the IoT device. Regularly audit your logs for any suspicious activity. Restrict access by creating specific user accounts only. Always keep the firmware on your IoT devices up-to-date. Implement multi-factor authentication (MFA), if supported by your SSH client and device.
Advanced Techniques and Tips:
For users looking to enhance their setup further, there are several advanced techniques and tips to consider. One important measure is the use of SSH keys for authentication. SSH keys are more secure than passwords because they rely on cryptographic keys rather than easily guessable passwords. Another useful technique is port forwarding. If youre not using a direct P2P connection, you can forward traffic from your router to your Windows 10 machine. This requires configuring your router to direct incoming traffic on a specific port to the local IP address of your Windows machine and to the port used by your SSH server. This can be a more complex process, but it can be necessary when not utilizing P2P technology.
Another area to explore is the use of SSH tunnels. SSH tunnels allow you to forward traffic from one port on your local machine to another port on a remote machine. This is useful for accessing services that are running on your IoT device but arent directly exposed to the internet. Additionally, consider implementing a firewall. Firewalls are an essential part of any security setup. They can be used to control the traffic that is allowed to enter and exit your network, providing an additional layer of protection against unauthorized access. Finally, always keep your software up to date, patching any vulnerabilities that are discovered, which is crucial to keeping your setup secure. Monitoring your logs for suspicious activity is also a key part of a strong security posture.
Troubleshooting Common Issues:
Even with a well-planned setup, you may encounter some issues. One of the most common problems is connection failure. Double-check your IP addresses, usernames, and passwords. Also, make sure the SSH service is running on your IoT device, and that there are no firewall rules blocking the connection. If using port forwarding, verify that the ports are correctly configured on your router. If you're experiencing problems, it's also helpful to review your system logs for more specific error messages.
Another frequent problem is that of permission issues. The SSH server on the IoT device may be configured with strict permissions that prevent you from accessing certain files or directories. This can often be resolved by adjusting the permissions on the device. If you have difficulty connecting, temporarily disable your firewall to rule out any potential interference. Then, re-enable the firewall and adjust your rules accordingly. If all else fails, try resetting your SSH configuration. This can sometimes resolve issues that arise from incorrect settings.
The Benefits of P2P SSH:
P2P SSH offers significant advantages over traditional methods. Primarily, it enhances security. By removing the need for a central server, you reduce the attack surface and minimize the risk of data breaches. Its efficient. P2P connections often simplify the setup process, eliminating the need for complex port forwarding and other network configurations. P2P setups also offer greater flexibility. They allow you to connect to devices even if they are behind firewalls or on private networks. Additionally, P2P SSH can provide better performance. Data travels directly between devices, reducing latency and improving overall performance.
For those managing multiple devices, a secure P2P SSH setup can be a significant time-saver. Instead of configuring multiple ports and managing complex network configurations, P2P SSH provides a simplified, user-friendly method for accessing your devices. This increases productivity and reduces the administrative overhead. The benefits are clear: streamlined operations, increased security, and a better user experience. In today's complex and interconnected landscape, the ability to securely manage remote devices is a must-have skill, making P2P SSH an essential tool for both professionals and hobbyists alike.
The Future of Remote Access and IoT Security:
As the world of IoT continues to evolve, the importance of secure remote access methods like P2P SSH will only increase. With an ever-growing number of connected devices, the potential for cyberattacks will also grow. It is vital to stay current with the latest security best practices and technologies. This includes regularly updating your software, monitoring your network for suspicious activity, and implementing strong authentication methods. The use of SSH and P2P technologies is just one piece of the larger puzzle of IoT security. Continuous monitoring and analysis are essential to maintaining the integrity and safety of your data.
Looking ahead, we can expect to see even more sophisticated tools and techniques for securing remote access. This includes the development of more user-friendly interfaces, automated security solutions, and enhanced encryption algorithms. The key will be staying informed and adapting to the ever-changing threat landscape. As threats evolve, so too must the security measures. By proactively implementing robust security protocols and adhering to best practices, we can work towards a safer and more secure IoT ecosystem.
In today's interconnected world, securely connecting to remote IoT devices has become an essential skill. By using P2P SSH on Windows 10, you can establish secure and direct connections, safeguarding your data and enhancing your IoT operations. Start your journey today and unlock the full potential of your connected devices.


Detail Author:
- Name : Hilbert Bednar
- Username : ahmed.bartell
- Email : vdamore@gmail.com
- Birthdate : 2004-11-24
- Address : 1405 Farrell Stream Winnifredchester, IN 36712-8520
- Phone : 1-732-840-1085
- Company : Buckridge, Moore and Flatley
- Job : Forming Machine Operator
- Bio : Veritatis ipsam sit qui deleniti. Nulla consectetur fugiat animi culpa maiores itaque. Tempore maxime ea aut voluptatum voluptas. Repellendus qui temporibus debitis quia facilis amet qui occaecati.
Socials
tiktok:
- url : https://tiktok.com/@hulda_schmitt
- username : hulda_schmitt
- bio : Itaque optio natus architecto cupiditate exercitationem sint.
- followers : 186
- following : 1129
twitter:
- url : https://twitter.com/hulda_real
- username : hulda_real
- bio : Iure quod molestiae voluptatem veritatis. Sint quia architecto qui consequuntur assumenda tenetur impedit. Autem omnis ullam dolorem debitis vitae vel.
- followers : 1366
- following : 753
instagram:
- url : https://instagram.com/hulda_schmitt
- username : hulda_schmitt
- bio : Consectetur aliquid velit nisi fugit. Molestiae cum non expedita dicta provident.
- followers : 3944
- following : 75
linkedin:
- url : https://linkedin.com/in/schmitth
- username : schmitth
- bio : Vitae rerum voluptatem quidem ut qui unde.
- followers : 748
- following : 2118