IoT Device Management: Secure Remote Access Guide & Best Practices
Is your company truly prepared to safeguard its IoT devices when accessing them remotely? The surge in interconnected devices has created a vast attack surface, demanding a proactive approach to security that goes beyond traditional methods.
While the ability to manage IoT devices from any location offers significant advantages, many organizations, especially those operating within private networks, have overlooked the critical need for secure remote management when traversing public networks. This oversight leaves them vulnerable to a range of cyber threats. Securing remote access is not merely a convenience; it's a fundamental requirement for maintaining operational integrity and protecting sensitive data. This article delves into the core challenges and best practices to ensure the robust security of your IoT infrastructure, regardless of the deployment scenario.
To provide a more comprehensive understanding, heres a breakdown of key considerations for remote IoT device management:
- Mert Ramazan Demirs Career From Arka Sokaklar To Yal Apkn Beyond
- Vernon Trumbull Net Worth Unveiling The Bayoubilly Stars Wealth
| Category | Details ||-----------------|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|| Definition | Remote IoT Device Management (RDM) encompasses the processes of equipping, validating, configuring, monitoring, and analyzing IoT devices from a centralized dashboard. The goal is to provide and support the full spectrum of their functional capabilities. || Key Processes | Equipping, Validation, Configuration, Monitoring, Analysis || Core Functionality | - Device onboarding and provisioning, Configuration management, Performance monitoring, Security management (including patch management and vulnerability scanning), Remote troubleshooting and diagnostics, Firmware Over-The-Air (FOTA) updates, Lifecycle Management, and more.|| Benefits | Simplified operations, Cost reduction, Improved Efficiency, Enhanced Security, Scalability, Remote Access, and the ability to manage multiple devices simultaneously. || Challenges | Cybersecurity threats, Network latency, device compatibility, scalability and complexity, cost concerns, and the necessity of a robust security posture. || Tools & Technologies | Remote Monitoring and Management (RMM) tools, Secure Tunneling, Cloud-based platforms, API integrations, and a variety of software solutions focused on different aspects of IoT management. || Best Practices | Implement strong security policies, Utilize encryption, Employ RMM tools, Secure tunneling, Regular security audits, and continuous monitoring || Lifecycle Stages | Provisioning, Monitoring, Maintaining, Decommissioning || Compliance | Compliance with relevant industry regulations (e.g., HIPAA, GDPR) is essential, especially when dealing with sensitive data. || Platforms | Rakwireless, Wanesy Management Center, Gemtek, AWS IoT Device Management, TeamViewer IoT. |
Source: Example IoT Management Reference Website (Replace with an authentic website link)
One crucial aspect of the IoT ecosystem is the concept of IoT device lifecycle management. This framework is a foundational element, ensuring that IoT devices remain functional, secure, and compliant from the moment they are deployed to their eventual retirement. This lifecycle comprises several distinct stages, each requiring careful attention: provisioning, monitoring, maintaining, and decommissioning. A well-defined lifecycle strategy minimizes risks and maximizes the longevity and value of your IoT investments. By understanding and managing each stage of the device lifecycle, organizations can maintain a more secure and efficient IoT infrastructure.
- Khalyla Kuhns New Love Life After Bobby Lee Split Details Privacy
- Ali Vitali Salary Net Worth Career Insights
The challenges confronting remote IoT device management are numerous, but they can be addressed with a structured and diligent approach. One of the most significant of these challenges is cybersecurity. The very nature of IoT, with its reliance on connected devices, creates an expanded attack surface. Any vulnerability can be exploited by malicious actors, resulting in data breaches, system disruptions, and financial losses. The rise in IoT malware attacks, with a notable increase in malicious payloads, underscores the urgency of this concern.
Beyond cybersecurity, other challenges arise from the complexities inherent in the IoT landscape. These include connectivity issues, the need for scalability to accommodate a growing number of devices, the complexities associated with integrating devices from various vendors, and the ever-present challenge of managing these devices effectively while adhering to regulatory requirements. Addressing these challenges requires a holistic approach, encompassing robust security protocols, the use of specialized management tools, and proactive monitoring and maintenance strategies.
The benefits of adopting a robust remote device management strategy are clear. You can simultaneously manage multiple devices remotely, rather than requiring physical presence for each task, offering significant time and cost savings. The ability to remotely monitor and manage devices is particularly valuable in industries where personnel are geographically dispersed or where physical access is challenging, such as in remote applications where battery replacements or device recharging are difficult. The ability to implement remote management streamlines operations and reduces operational expenses.
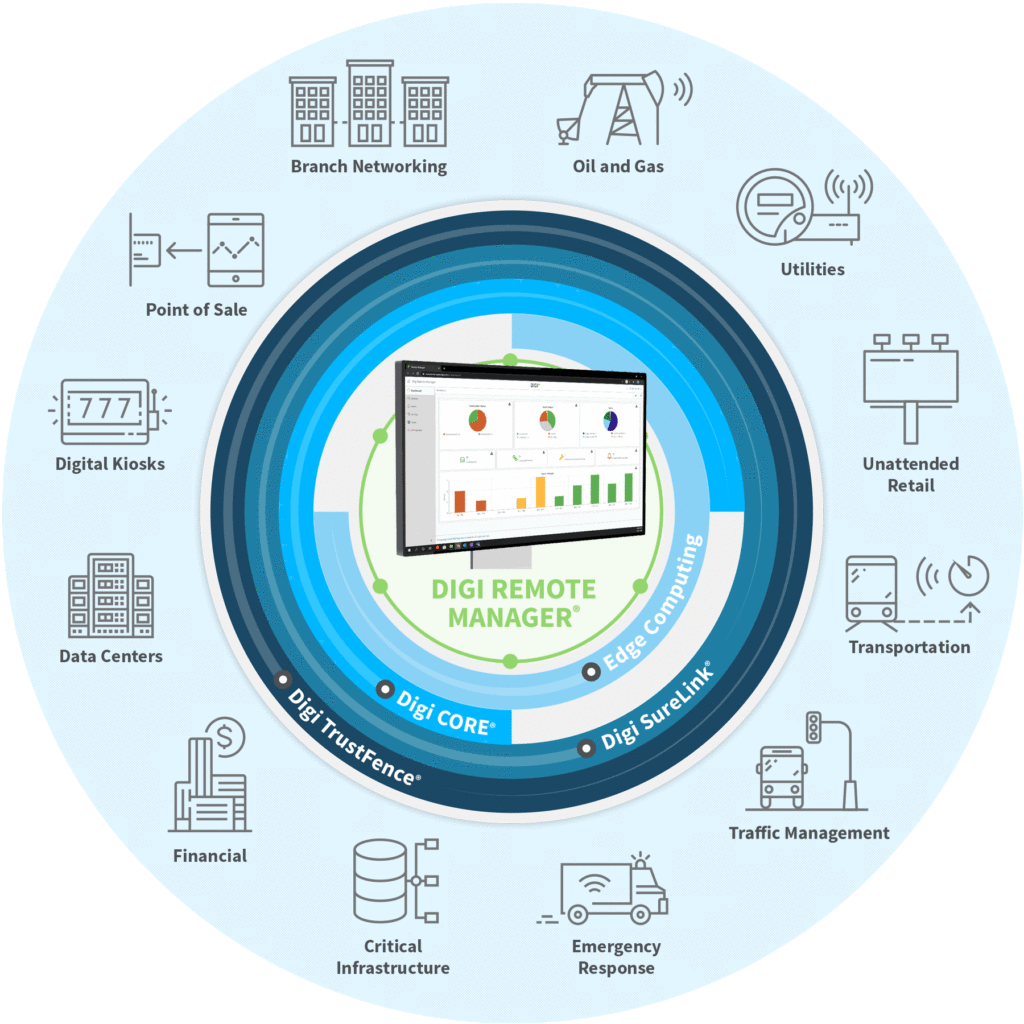
Remote management of IoT devices is a complex series of processes designed to equip, validate, configure, monitor, and analyze devices through a centralized dashboard. The aim is to provide and support the full spectrum of their functional capabilities. A comprehensive remote management solution will go beyond basic screen sharing to include terminal access, application control, and edge management, offering a complete solution to even the most intricate IoT management scenarios. It is important to note that implementing remote control practices can be tricky. It is important to consider all potential pitfalls.
Implementing and scaling IoT device management often involves complex considerations. Before implementing any management practices, be sure you understand the system's capabilities. The following are best practices to ensure secure remote management of IoT devices in any scenario.
To secure your IoT infrastructure, start with your companys security policies. Ensure that well-defined security policies are in place for all IoT devices. Such policies serve as the backbone for how security is deployed and managed, specifying the who, what, where, and when of security measures. This includes defining which personnel are authorized, the channels through which access is granted, and the times during which maintenance and updates can occur. A clear security policy provides a framework, ensuring consistency and accountability across the entire IoT ecosystem.
Investing in remote monitoring and management (RMM) tools provides a mechanism for tracking device health, monitoring login attempts, and analyzing resource usage for each IoT device without requiring physical access. These tools enable proactive management and early detection of potential issues. For example, RMM tools can provide real-time alerts on unusual login attempts, helping to prevent unauthorized access. In addition, they provide insight into the performance of each device, helping to identify and address issues that may impact functionality.
Implementing a secure transition to new technologies requires careful planning and execution. Begin by thoroughly evaluating the security implications of any new technology before its deployment. This includes assessing potential vulnerabilities and integrating security measures. For example, you may wish to implement secure tunneling to maintain a secure connection to devices that are behind firewalls. Proper training of personnel is essential to minimize risks. Develop a detailed, step-by-step plan for integrating new technologies, and ensure that all stakeholders are informed. This structured approach reduces the risk of security breaches, simplifies maintenance, and increases the overall return on investment in new technology.
Remote IoT enables you to securely connect and manage machines and devices from virtually anywhere. Secure connections and ease of access are a key part of a complete security plan. This is often achieved through secure tunneling that protects data in transit by encrypting all network traffic using an SSH tunnel. It means that no one, not even the Remote IOT provider, can read the data in the tunnel. When it comes to securing remote IoT access, security is a top priority.
Another key component is the implementation of a unified dashboard. A well-designed dashboard provides a single pane of glass through which you can monitor device health, network usage, and other critical metrics. Such dashboards often provide real-time alerts based on monitored data. For example, you could set up alerts for devices that exceed CPU or memory usage. Comprehensive dashboards also allow you to run batch jobs on multiple devices at once, streamlining maintenance and updating procedures.
In order to improve IoT device security, there are some basic steps that can be taken. The first step is to utilize encryption methods like AES or DES to secure data transmitted by IoT devices. Encryption transforms data into an unreadable format, ensuring that even if intercepted, the information remains secure. It is also important to implement data protection strategies, including antivirus software, automated monitoring, data visibility solutions, and robust authentication protocols.
Many IoT devices are deployed behind restrictive firewalls at remote sites, necessitating a secure method to gain access for tasks such as troubleshooting, configuration updates, and other operational tasks. Secure tunneling is a key feature of AWS IoT device management, assisting customers in executing remote tasks. Additionally, the AWS offers services to elevate customers even further.
To remove remote device management, you typically need to unenroll the device from the management system. This is often done via the device settings or the management software. This procedure will always involve providing access credentials, such as a password, to ensure that only authorized personnel can make changes. This step is critical to maintaining control and security of your IoT devices.
The ability to remotely control devices, combined with comprehensive monitoring capabilities, is essential. These functions allow you to view a complete overview of all your IoT devices within a single, centralized dashboard. This includes the ability to monitor CPU, memory, and network usage remotely. It also allows you to receive alerts based on the data collected and run batch jobs across multiple devices. This streamlines operations and enhances the ability to proactively manage your devices.
With the vast amount of sensitive data that IoT devices collect and transmit, secure remote management is paramount. This demands a multi-layered security approach, encompassing not only strong authentication and encryption, but also constant monitoring and the rapid response to identified threats. The need for data protection strategies, including antivirus software, automated monitoring systems, and robust authentication, cannot be overstated. A strong security posture is the foundation of a secure remote access strategy.
Poor network quality is also an issue. Poor network quality can disrupt communication between IoT devices and users, making remote access less reliable in some cases. This can affect the devices performance, especially if the devices are in remote areas where the network is unstable. For this reason, it is important to establish a stable network for these devices.
When considering the implementation of IoT device security, the following actions are paramount: Employ strong passwords and multi-factor authentication to restrict access. Regularly update firmware to patch security vulnerabilities. Segment your IoT devices from your main network to contain potential breaches. Monitor network traffic for suspicious activity.* Secure data transmission through encryption methods.
It streamlines the management of IoT devices at scale, improving operational efficiency and reducing risks. In today's interconnected operations, every device, machine, and controller could be a target for attackers. IoT malware attacks have risen significantly, accompanied by a surge in malicious payloads. In order to keep operations secure, you must continually assess and enhance your security practices.


Detail Author:
- Name : Kaylie Strosin PhD
- Username : beatrice96
- Email : jaskolski.jamir@yahoo.com
- Birthdate : 1974-11-08
- Address : 29159 Greenholt Prairie Angelofort, VT 76237
- Phone : +1.681.906.8312
- Company : Hoppe PLC
- Job : Speech-Language Pathologist
- Bio : Quo enim similique omnis sequi placeat doloremque inventore vel. Quo minima voluptas voluptatem. Saepe vitae eaque perspiciatis quia consequatur.
Socials
facebook:
- url : https://facebook.com/vwiza
- username : vwiza
- bio : Ex voluptatem dolorem aut eveniet quos eius. Minus omnis voluptas sit vitae.
- followers : 4173
- following : 495
twitter:
- url : https://twitter.com/wizav
- username : wizav
- bio : Magnam asperiores sit ut. Reiciendis facere distinctio corporis et. Aperiam sit earum veritatis incidunt deleniti.
- followers : 5769
- following : 2256
linkedin:
- url : https://linkedin.com/in/veda_real
- username : veda_real
- bio : Repellat voluptatibus non sit qui rem saepe ut.
- followers : 2765
- following : 968
instagram:
- url : https://instagram.com/veda.wiza
- username : veda.wiza
- bio : Aspernatur ut sapiente autem ea quam quis. Quia quos harum sint odio. Ad quam dolor dolores aut.
- followers : 6053
- following : 1251